Introduction
Regulations, compliance, and certain incidents often lead our companies to reinforce their cybersecurity measures. Security Information and Event Management (SIEM) stands at the forefront of this defense, offering a comprehensive approach to threat detection, analysis, and response.
In this guide to SIEM fundamentals, we delve into its definition, exploring its essential functions and pivotal role in modern cybersecurity strategies. Additionally, we illuminate practical use cases, demonstrating how SIEM empowers organizations to proactively safeguard their digital assets against evolving threats.What is SIEM?
A SIEM is an advanced cybersecurity solution. It collects and analyzes security data in real-time. From multiple sources across an organization. Correlating data enables threat detection. And rapid response to breaches, suspicious activities.
A SIEM provides comprehensive visibility, protection. Against sophisticated cyber attacks today. Pronounced "sim," it plays a central role. In security operations with actionable alerts. Compliance reporting, complete audit trail.
Why is SIEM important?
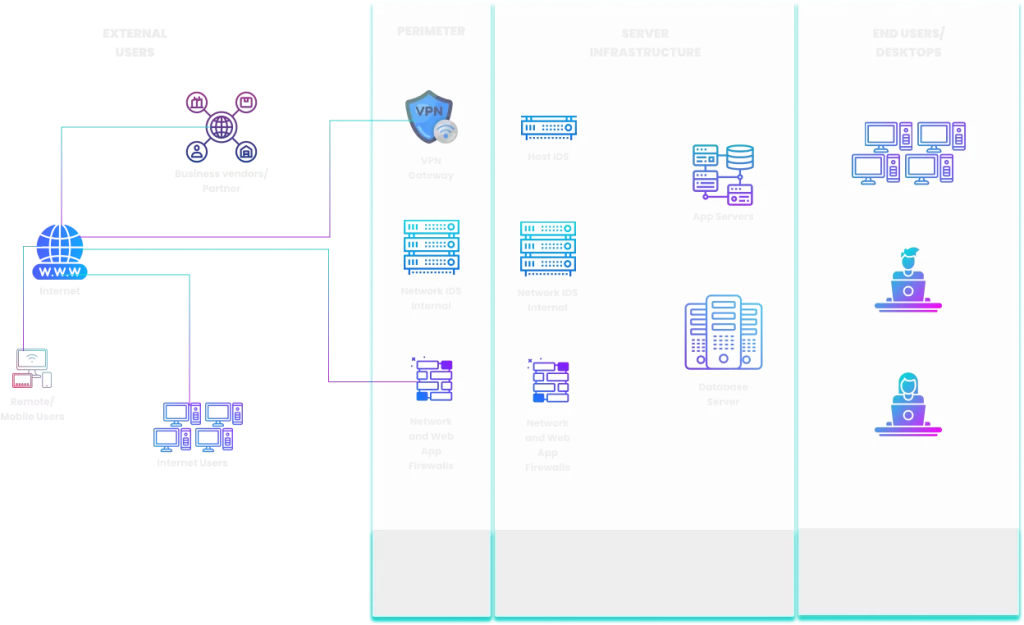
A SIEM solution is crucial for robust cybersecurity. Firstly, it proactively detects and counters threats. Through continuous monitoring and correlation analysis.
Moreover, a SIEM ensures regulatory compliance. It meets data protection, industry-specific requirements. Providing comprehensive audit trails, compliance reports.
Additionally, SIEM mitigates risk effectively. By identifying suspicious activities promptly. Enabling rapid incident response, threat containment.
Furthermore, SIEM enhances incident response capabilities. Offering real-time security alerts, automated processes. And a centralized view of events.
Case studies demonstrate SIEM's proven ROI. Reducing response times, downtimes significantly. Preventing costly data breaches, financial losses.
A SIEM is scalable, adapting seamlessly. To growing data volumes, infrastructures. It's a long-term investment addressing emerging challenges.
Finally, SIEM aligns with industry standards. Such as NIST Cybersecurity Framework, ISO 27001. Following best practices, strengthening security posture.
SIEM: Key Terms and Concepts
When discussing SIEM (Security Information and Event Management), it's essential to understand key terms and concepts. Let's explore some crucial ones:
Security Events: Activities or occurrences monitored for potential security implications. Examples: failed logins, firewall blocks, malware detections.
Log Management: Centralized collection, storage, and analysis of logs from diverse sources. Enabling correlation, auditing, and incident investigation.
Correlation Rules: Predefined logic to identify patterns or combinations of events. Triggering alerts for potential threats or policy violations.
Threat Intelligence: Contextualized data about emerging cyber threats, indicators of compromise (IoCs), and adversary tactics, techniques, and procedures (TTPs).
MITRE ATT&CK: A globally accessible knowledge base of adversary tactics and techniques. Mapping enterprise datasets to the ATT&CK matrix enhances threat detection.
Security Analytics: Advanced data analysis and machine learning capabilities within SIEM. Enabling user behavior analytics (UBA) and anomaly detection.
Security Operations Center (SOC): A centralized unit combining people, processes, and technology. Responsible for monitoring, detecting, investigating, and responding to cybersecurity incidents.
SOC Analyst: A cybersecurity professional within the SOC. Responsible for monitoring SIEM alerts, analyzing security events, and initiating incident response.
Security Orchestration and Automated Response (SOAR): Integrated capabilities for incident management, orchestration, and automated response actions based on SIEM alerts.
By mastering these SIEM concepts, the role of a SOC/SOC Analyst, organizations can effectively leverage their SIEM solution across the security operations lifecycle.
Core Functionality of SIEM
To discover the true capabilities of a Security Information and Event Management (SIEM) system, it's essential to understand its core functionalities.
A robust SIEM, like Qradar or Fortisiem, gathers and analyzes security event data from numerous sources, identifying potential threats before they escalate into significant issues.
Identifying SIEM use cases
Crafting effective SIEM use cases necessitates a profound grasp of your organization's distinctive risk landscape. Transitioning from identification to justification, each use case underscores its rationale, drawing from ubiquitous attacker tactics, industry-specific indicators, or germane context. A meticulous evaluation process ensures your chosen use cases mirror present threats and strike a chord with stakeholders.
Baseline Threat Assessment
Initiate by examining prevalent attack methods within your sector. Transitioning from examination to integration, trustworthy sources, such as MITRE ATT&CK matrices, Verizon Data Breach Investigation Reports, and renowned cybercrime databases inform your baseline threat appraisal. Harmonizing SIEM use cases with predominant themes buttresses defenses against plausible threats.
Historical Analysis
Analyze historical incidents afflicting your institution or comparable players within your domain. Recognizing repetitive patterns or peculiarities manifest during antecedent breaches illuminates latent signals requiring heightened vigilance. Embedding industry-particular indices arms your SOC squad with indispensable hints for prompt detection and annihilation of equivalent invasions.
Regulatory Compliance
Consider internal policies regulating data confidentiality, obligatory edicts, and binding accords. Safeguard adherence to external standards, encompassing GDPR, HIPAA, PCI-DSS, averts juridical jeopardy whilst nurturing customer trust. Blending compliance-centered use cases with conventional threat prevention augments SIEM solution versatility.
Personalization
Recollect that every enterprise entertains idiosyncratic risk portfolios. Personification reigns supreme when manufacturing SIEM use cases calibrated precisely for your operational milieu. Customization comprises adjusting generic blueprints relative to exclusive criteria, weightage schemas, and escalation procedures, producing a tailored bulwark defending your interests.
Continuous Improvement
To ensure staying ahead in the ever-evolving landscape of SIEM use cases, continuous self-assessment of their origins, goals, and outcomes is imperative. By systematically reviewing each component, organizations can significantly bolster their cybersecurity defenses against prevalent threats, fortify mission-critical systems, and sustain uninterrupted business operations within a consistently adversarial digital battlefield.
Data aggregation
SIEM systems accumulate and merge distinct types of data – logs, events, and alerts – originating from various security instruments deployed within the network, namely firewalls, anti-virus programs, and Intrusion Detection Systems. Consolidation simplifies thorough examination and correlation, thereby reinforcing prompt menace discovery.
High-caliber data aggregation amplifies awareness, expedites operational processes, and fortifies grounded choices regarding cybersecurity measures.
Nevertheless, placing excessive faith in standalone, computerized machine learning could result in misleading conclusions stemming from dubious data sources or inadequate situational comprehension.
Real-time Analysis
SIEM systems perform real-time analysis of incoming data, meticulously examining each event as soon as it arrives. This constant surveillance empowers them to spot irregularities such as unusually large data transfers, repeated login attempts, or unexpected network traffic fluctuations.
They also discern intricate patterns indicative of malicious intent, like coordinated attacks or insider threats. Consequently, potential security risks are exposed immediately.
Upon detecting abnormal behaviors, such as policy violations or unauthorized access attempts, SIEM tools activate instant notifications, enabling security analysts to take quick action.
Rules could be specific policies defining acceptable usage or predefined conditions based on industry standards.
Sophisticated algorithms might involve statistical baselines or heuristics, while machine learning incorporates AI-powered predictive modeling to augment pattern recognition and adapt to evolving threats.
Equipping your security infrastructure with a SIEM featuring real-time analysis bolsters defenses, notably reducing incident response intervals.
Leveraging extensive analytical and automated features ensures optimal safeguarding of digital assets. Thus, embracing real-time analysis keeps you at the forefront of tackling emerging cybersecurity challenges effectively.
Threat Detection
Threat Detection is a core feature of SIEM systems, enabling continuous monitoring and analysis of network activities. SIEMs utilize predefined signatures and behaviors, as well as anomaly detection, to spot recognized threats and identify emerging ones.
Effective threat detection empowers organizations to proactively mitigate cyber risks by addressing vulnerabilities early and minimizing damage caused by breaches.
Early warning signs enable informed decision-making, streamlined incident response, and enhanced overall security posture.
Implement comprehensive threat detection strategies utilizing SIEM platforms for heightened situational awareness, rapid response times, and adaptability to emerging threats.
Continually refine detection rules and leverage machine learning algorithms to maintain optimal performance and ensure compliance with organizational security policies.
Incident Response
Incident Response in a SIEM signifies the ability to rapidly respond to detected security incidents. When a SIEM identifies unusual or potentially harmful activities, the incident response function immediately kicks in.
Its primary objective is to contain the suspected threat, assess the extent of the damages, rectify the vulnerabilities, and restore normal operations while ensuring minimal disruption to the business.
Efficient incident response mechanisms involve automation, allowing security personnel to efficiently evaluate the severity of each incident, prioritize them accordingly, and act decisively to counteract attacks.
Integrating machine learning algorithms also empowers SIEMs to predict future incidents, enhancing the overall defensive posture of the protected environment.
By leveraging comprehensive and potent incident response capabilities integrated within SIEM platforms, organizations build resiliency against diverse cyber threats while simultaneously improving their capacity to operate smoothly amidst challenging circumstances. This dual advantage fosters competitive edge, promotes growth, and ensures long-term sustainability in an increasingly volatile digital realm.
Capitalize on automated playbooks, Multi-source Data Correlation, and Up-to-Date Threat Intelligence Feeds to Optimize Incident Handling Processes:
Automated Playbooks:
Streamlined incident response heavily relies on orchestrated and synchronized actions driven by intelligent automation. Customizable playbooks allow security practitioners to define sequences of tasks tailored to distinct types of incidents, enabling seamless execution and accelerating response times.
Multi-Source Data Correlation:
Combining vast arrays of telemetry data from disparate sources fortifies the accuracy and relevance of incident detections. Applying analytics tools and machine learning algorithms to aggregate logs and events bolsters signal-to-noise ratios, resulting in higher fidelity alarms and enhanced visibility across dynamic environments.
Up-to-Date Threat Intelligence Feeds:
Subscribing to reputable external threat intel providers equips organizations with actionable insights regarding novel TTPs (Tactics, Techniques, Procedures) employed by adversaries. Continually incorporating these updates into SIEM rulesets improves pattern recognition, leading to swifter detection and eradication of zero-day exploits and ongoing campaigns targeting vulnerable targets.
Streamlining incident handling processes through these strategic approaches leads to quickened mean-time-to-respond (MTTR) metrics, augmented decision support, and heightened efficacy in combatting persistent threats. Such advancements empower defenders to remain steadfast in defending their respective domains even in the face of expanding and evolving threat landscapes.
Compliance Reporting
Compliance Reporting is a vital SIEM feature helping organizations meet specific regulatory compliance requirements. It creates comprehensive reports detailing adherence to sector-specific standards and rules, capturing security incidents, policy breaches, and holistic security status. Reports simplify audits and assessment processes.
By utilizing Compliance Reporting, businesses guarantee alignment with pertinent industry guidelines, reducing risks, and averting fines.
Transparent reporting cultivates confidence among entities, investors, and authorities alike. Streamlining operations subsequently boosts efficiency and prosperity. Here are examples:
- Healthcare providers demonstrating HIPAA compliance regarding us patient data.
- Finance firms confirming Sarbanes-Oxley Act compliance for transparent accounting procedures.
- Banks proving Payment Card Industry Data Security Standard (PCI DSS) compliance for protecting payment cardholder details.
Maximize advantages by deploying a SIEM solution equipped with sophisticated Compliance Reporting abilities.
When choosing suppliers, prioritize compatibility, effortless implementation, scalability, versatility, and committed assistance.
Optimal investments yield lasting achievements and ongoing development. Improved organizational security measurements position your firm competitively, embracing innovation along the path towards digital triumph.
Benefits of Using SIEM
The usefulness of fortifying cybersecurity with a Security Information and Event Management (SIEM) system is no longer in question. In today's digital age, businesses need advanced tools to detect threats, ensure regulatory compliance, and streamline operations. Here are some benefits of implementing a robust SIEM solution into your organization's cybersecurity posture.
Improved Security Visibility
With so many devices connected within modern networks, maintaining complete visibility can be challenging.
However, integrating a SIEM tool provides real-time monitoring and analysis of events across all network assets.
This centralization offers enhanced situational awareness, enabling security teams to quickly identify suspicious activities and respond appropriately before they escalate into severe incidents.
By utilizing machine learning algorithms and artificial intelligence, SIEMs can also predict potential vulnerabilities and provide actionable recommendations.
Accelerated Threat Detection and Response with SIEM
One key advantage of using a SIEM platform is its ability to aggregate data from multiple sources, correlate events, and prioritize alerts based on severity levels.
These features allow analysts to focus their attention on genuine threats instead of sifting through mountains of irrelevant logs.
Consequently, organizations leveraging SIEM solutions enjoy faster mean time to detect (MTTD) and mean time to resolve (MTTR) compared to those without them.
Moreover, automation capabilities further expedite incident resolution processes while reducing human errors.
Better Compliance Management
Regulatory requirements continue evolving, making it increasingly difficult for companies to maintain compliance consistently.
Implementing a reliable SIEM solution simplifies compliance management tasks by automatically generating reports aligned with specific industry standards.
It helps demonstrate proof of compliance during audits, reduces manual workload associated with documentation, and minimizes the risk of noncompliance penalties. Some popular regulations supported include GDPR, PCI DSS, SOX, and HIPAA.
Enhanced Operational Efficiency
Lastly, incorporating a SIEM platform leads to improved overall organizational efficiency. Instead of manually managing numerous security controls spread out across disparate systems, security personnel gains access to unified dashboards displaying vital metrics at a glance.
Furthermore, built-in playbooks facilitate standardization of procedures, thereby enhancing consistency and repeatability of responses.
Ultimately, these enhancements enable teams to allocate resources more effectively towards strategic initiatives instead of daily firefighting.
In conclusion, deploying a SIEM system brings significant advantages related to increased visibility, quicker threat detection, better compliance management, and heightened operational efficiency.
With cybercrime continually rising, investing in a comprehensive SIEM solution has become essential for any business aiming to protect sensitive information and safeguard reputation. Embrace SIEM technology now to stay ahead of emerging threats and achieve sustainable growth in the long run.
Implementing a Successful SIEM Strategy
Initiating the SIEM selection and implementation process mandates a profound comprehension of the organizational landscape.
Meticulously mapping the digital terrain permits astute decision-making, leading to seamless integration and enhanced cybersecurity defenses.
Delving deep into the nuances of the environment serves as a springboard for devising informed strategies centered around specific threats and vulnerabilities.
Subsequently, embarking on the SIEM voyage armed with holistic situational awareness culminates in a robust, efficacious, and coordinated security apparatus, ready to combat ever-evolving cyber adversaries.
Identifying SIEM use cases
cial to justify the inclusion of each use case by identifying its underlying rationale, whether it stems from prevalent attacker tactics, industry-specific indicators, or any other pertinent context.
This rigorous evaluation process guarantees that your chosen use cases accurately reflect current threats and resonate with your stakeholders.
To begin, consider the most common methods employed by malicious actors within your sector.
Draw inspiration from trusted sources such as MITRE ATT&CK matrices, Verizon Data Breach Investigations Reports, and other authoritative databases detailing prevailing trends in cybercrime.
Aligning your SIEM use cases with these prominent themes bolsters your defensive capabilities against likely attacks.
Next, scrutinize past incidents experienced by your own enterprise or similar entities operating within your niche.
Identifying recurring patterns or unusual behaviors exhibited during previous breaches may reveal previously overlooked warning signs warranting closer examination.
Inclusion of such industry-specific indicators equips your SOC team with vital cues necessary for swift recognition and neutralization of analogous intrusions moving forward.
Additionally, factor in any internal policies governing data privacy, regulatory mandates, and contractual obligations.
Ensuring conformity with external regulations like GDPR, HIPAA, or PCI-DSS not only mitigates legal exposure but also fosters trust between your entity and valued customers.
Consequently, interweaving compliance-focused use cases alongside those geared towards traditional threat prevention amplifies the versatility of your SIEM solution.
Lastly, bear in mind that no two enterprises share identical risk profiles. Customization remains paramount when constructing SIEM use cases tailored specifically to your operational reality.
Adapting generic templates according to proprietary criteria, weightage schemes, and escalation processes engenders a bespoke defensive apparatus uniquely suited to safeguarding your interests.
Ultimately, cultivating purposeful SIEM use cases demands continuous introspection regarding their origin, intent, and ultimate utility.
Selecting appropriate data sources
Selecting suitable data sources for your SIEM is a critical aspect of designing an efficient security monitoring and threat detection strategy. To make informed decisions, follow these recommendations :
- Value-Volume Matrix: Distinguish data sources based on their volume and worth. For example, proxy logs possess substantial volumes yet yield significant value in creating security detection scenarios like discerning C2 channels and SSH tunnels. Grasping this relationship assists in judicious prioritization of data sources.
- Threat-Centered Selection: Tailor data source choices according to the targeted threats and corresponding responses. Matching data sources with particular threats and reaction measures fine-tunes your SIEM deployment for active menace administration.
- Graduated Approach: Initiate modestly with limited data collections, centering on one source first. This measured introduction showcases SIEM's merits and clarifies requisite reactions for identified threats prior to broadening data gathering endeavors.
- Manageable Performance Levels: Define sensible performance benchmarks for the SIEM tool, guaranteeing alignment with the organization's security surveillance and incident response goals. Evaluating these parameters informs judgments on the suitability of picked data sources in reinforcing SIEM procedures.
By heeding these recommendations, organizations can strategically pick and sequence data sources for their SIEM execution, thereby improving safety stance, threat discovery capacities, and general functional competence.
Configuring alerts and notifications
Configuring alerts and notifications plays a pivotal role in realizing an effective SIEM strategy, including alert escalation. Setting up alerts involves defining conditions triggering automated messages for timely incident response.
Setting up alerts and notifications entails defining conditions triggering automated messages sent via email, SMS, or dashboards. Such triggers could include failed authentication attempts, unexpected system configurations, or irregular network traffic.
Upon configuring alerts, the SIEM platform actively communicates security incidents requiring attention.
Analysts benefit from timely information dissemination without needing constant supervision, thereby improving responsiveness and reducing mean time to acknowledge (MTTA) and resolve (MTTR) issues.
Optimize the alert configuration process by performing iterative fine-tuning exercises. Begin with coarse rules and subsequently refine them, accounting for false negatives or irrelevant alarms.
Also, establish priority levels based on the event's urgency and potential consequences, allowing the security team to allocate resources efficiently.
Lastly, conduct routine audits to maintain relevancy and adapt to changing threat landscapes.
Configuring alerts and notifications forms a fundamental pillar in establishing a mature SIEM practice, driving operational excellence, and maintaining strong cyber resilience. Take charge of your SIEM implementation journey by mastering this indispensable skillset.
Developing incident response plans
Organizations must develop comprehensive incident response plans (IRPs) to manage cybersecurity crises effectively.
An IRP guides the actions taken by the Incident Response Team (IRT) during a security incident, helping mitigate damage and expedite restoration. Below is a concise guide to create an IRP for a SIEM environment.
Establishing an Incident Response Team (IRT):
Form a committed IRT consisting of professionals occupying positions such as Chief Information Security Officer (CISO), incident response administrators, security researchers, and authorized agents from departments like law and public relations. Having a designated IRT ensures efficient handling of security incidents.
Identifying Critical Assets and Risks:
Determining vital assets requiring safeguarding and recognizing possible risks lurking within the organization's systems focuses incident response efforts appropriately. Classify assets based on parameters like sensitivity, availability, confidentiality, and functionality. Pinpoint areas susceptible to compromise due to insufficient controls, weak links, or misconfigurations.
Drafting the Incident Response Plan:
Generate a complete IRP delineating the sequence of events during a security incident. Divide the procedure into sequential stages, namely:
- Identification: Detect the presence of a security incident.
- Eradication: Remove all traces of the intrusion, repair damaged components, and restore systems to their original state.
- Containment: Isolate affected systems, preventing further contagion.
- Recovery: Restore standard operations gradually, validating systems thoroughly, and confirming non-occurrence of residual effects.
- Post-incident Activity: Document findings, perform root cause analyses, recommend corrective actions, and review the IRP for enhancement.
Refer to blueprints furnished by reputable institutions such as NIST or SANS for shaping the structure and content of the plan.
Developing a Communication Plan:
Engineer a communication scheme to facilitate seamless and lucid exchange of information between the IRT and involved parties, interior and exterior. Comprise touchpoints for reaching out to IRT participants rapidly during a cyber episode. Allocate spokespersons responsible for relaying accurate updates to employees, clients, partners, regulators, and the press.
Testing and Updating the Response Plan:
Periodically assess and revamp the IRP to ascertain its viability and currency in confronting emergent cyberspace menaces. Capitalize on wisdom gained from actual incidents to augment the plan's potency continuously. Schedule mock drills simulating diverse attack vectors regularly, encouraging collaboration and honing response skills within the IRT. Encourage open dialogue concerning procedural weaknesses and improvement avenues, stimulating progression in the realm of cybersecurity preparedness.
Common Use Cases for SIEM
Network intrusion detection
Network intrusion detection constitutes a fundamental pillar in maintaining robust cybersecurity defenses. Leveraging advanced algorithms and statistical analyses, SIEMs can discern subtle discrepancies signaling nefarious actions lurking beneath seemingly benign network traffic.
Such collaborative endeavors expand the depth and breadth of available data points, allowing analysts to dissect granular details concerning IP addresses, ports, protocols, packet payloads, HTTP headers, and transport layer metadata.
Ultimately, these multifaceted perspectives coalesce into a holistic understanding of ongoing network dynamics, equipping defenders with indispensable intel needed to fortify vulnerable entry vectors and circumvent sophisticated attack campaigns.
User behavior analytics
User Behavior Analytics (UBA) represents a burgeoning field heralding unprecedented advancements in combating insidious threats emanating from stealthy perpetrators.
By scrutinizing historical and contemporaneous activities, UBA platforms establish baseline conduct norms for individual users, workgroups, and departments, subsequently flagging incongruencies suggestive of unauthorized access, privilege abuse, or compromised credentials.
SIEM solutions integrate seamlessly with commercial and homegrown UBA technologies, thus widening the purview of monitored identifiers spanning authentication logs, session records, API calls, email correspondences, remote desktop connections, and cloud app usage.
Thereupon, machine learning models parse myriad attributes associated with these transactions, sifting through petabytes of event telemetry to isolate dubious artifacts worthy of deeper investigation.
Amongst others, notable red flags comprise failed login attempts, concurrent sessions, excessive downloads, rapid file modifications, unexplainable location shifts, and sudden surges in privileged entitlements.
Cloud security monitoring
Cloud computing continues to reshape contemporary business landscapes, spawning novel paradigms predicated on hyperconnectivity, virtualization, automation, and ubiquity.
However, this tectonic shift introduces newfound complications vis-a-vis governance, risk management, and compliance, compelling information security practitioners to reassess conventional controls ill-equipped to grapple with ephemeral infrastructures transcending physical confines.
Enterprise-grade SIEMs cater to these evolving demands by extending support for diverse public, private, and hybrid clouds, bridging disparate silos via standardized APIs and native connectors.
Specifically, Amazon Web Services (AWS), Microsoft Azure, Google Cloud Platform (GCP), IBM Cloud, Oracle Cloud, and Salesforce boast turnkey compatibility, permitting bi-directional synchronization of audit trails, configuration settings, inventory states, and runtime metrics.
Once ingested, the consolidated dataset fuels multi-dimensional queries capable of surfacing latent vulnerabilities, misconfigurations, shadow IT instances, unsecured storage containers, exposed endpoints, noncompliant access patterns, and unauthorized data transfers.
Thus, armed with timely warnings, cloud architects can promptly rectify errant configurations, enforce least-privilege principles, and restore equilibrium within tenuous shared responsibility models.
Insider threats
Insiders pose potent menaces due to their intimate knowledge of sensitive assets coupled with legitimate credential sets affording unfettered access to crown jewels.
Whether motivated by financial gains, ideological fervor, retribution, curiosity, or sheer negligence, rogue employees often wield outsized influence over corporate espionage, intellectual property theft, sabotage, or fraudulent activities.
To combat this invisible enemy, SIEMs concentrate on tracing digital footprints left behind by human actors navigating cyberspace.
Correlating disparate touchpoints accrued from authentications, provisioning requests, HR records, travel vouchers, badge swipes, web browsing histories, social feeds, instant messages, and third-party apps paints a vivid portrait of individuals' preferences, tendencies, habits, affiliations, and intentions.
Subsequent analysis highlights peculiar associations indicating collusive relationships, conflict-of-interest situations, undue pressure, stress levels, burnout symptoms, or incriminating evidence pointing toward wrongdoings.
Preemptively detecting early warning signals triggers preventive measures aimed at containing damages inflicted by disgruntled staff, lone wolves, or malign agents embedded deep within supply chains.
Advanced persistent threats (APT)
Advanced Persistent Threats (APTs) denote clandestine operatives executing prolonged campaigns characterized by stealth, patience, resiliency, adaptiveness, and precision.
Typically sponsored by nation-states, criminal cartels, hacktivist collectives, or industrial espionage groups, APTs relentlessly pursue lucrative targets with calculated determination, leaving no stone unturned in extracting every last drop of leverage attainable.
SIEM solutions play a crucial role in foiling APTs by centralizing vast troves of extant threat intelligence catalogued within built-in rulesets, signatureless anomaly detection mechanisms, and behavioral baselines.
Upon encountering ambiguity surrounding zero-day exploits, SIEMs apply heuristics-based approaches to recognize obscure patterns concealed underneath obfuscated code obfuscation layers.
Suspicious traits include command-and-control (C2) channel formation, encrypted communication flows, and predictable intervals between connection establishment.
Nevertheless, SIEMs supplement rulebases with advanced sandboxing features, deception technologies, and forensic tools, thereby enhancing their arsenal in countering elusive APTs.
Compliance reporting
Organizations must comply with an array of regulatory mandates dictating precise recordkeeping, auditing, logging, and reporting responsibilities.
SIEMs accommodate these prerequisites by furnishing prefabricated reports prescribed by authorities supervising healthcare, finance, retail, manufacturing, energy sectors, among others.
Besides, SIEMs can produce customized outputs meeting specific reporting formats demanded by diverse legislation, enabling hassle-free certifications.
Comprehensive dashboards summarize crucial aspects, whereas drill-down charts illustrate detailed breakdowns revealing hidden narratives behind apparent figures.
Users benefit from interactive visualizations, dynamic filters, and conditional styling options, translating raw facts into digestible stories ready for mass consumption. Rest assured, SIEMs deliver reliable content packaged in readily consumable formats compatible with mainstream dietary restrictions.
In conclusion, selecting fitting data sources and mastering their nuances remain integral components of building effectual SIEM strategies. Cybersecurity enthusiasts stand to profit substantially from our guidance on perfecting these facets.
Future Trends in SIEM Technology
Artificial Intelligence and Machine Learning
Artificial intelligence (AI) and machine learning (ML) have emerged as promising technologies poised to significantly influence forthcoming developments in Security Information and Event Management (SIEM) systems.
AI-enhanced SIEMs facilitate sophisticated threat detection via intelligent algorithms capable of discerning subtle irregularities, thereby reducing false positives and augmenting accuracy. ML, meanwhile, contributes to honing rule sets and fine-tuning SIEM configurations dynamically without explicit programming instructions.
Leveraging AI and ML paves the way for predictive analytics, whereby prospective threats could be pinpointed ahead of actualization, thus permitting preventive measures to deter compromise.
Integrated Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) represents another burgeoning trend amalgamating with conventional SIEM architectures.
EDR specializes in tracking and securing endpoints dispersed across networks, complementing centralized logging and reporting functionalities native to SIEMs.
Combining forces yields potent protective mechanisms boasting expansive reach spanning myriad devices, platforms, and applications.
Merging EDR with SIEMs fortifies event correlations, hastens response times, and promotes holistic asset protection.
Security Orchestration, Automation and Response (SOAR)
Security Orchestration, Automation, and Response (SOAR) heralds additional advancements in SIEM technology.
SOAR platforms integrate disparate components of security operations centers (SOCs), harmonizing workflows, standardizing playbooks, and synchronizing communication channels.
Such consolidation culminates in expediting triage, slashing resolution timelines, and diminishing reliance on labor-intensive tasks.
Coupling SIEM with SOAR translates into cohesive, responsive, and resilient cybersecurity defenses equipped to confront rapidly evolving menaces.
Managed Services and Outsourcing Options
Managed services and outsourcing alternatives constitute an attractive option for resource-constrained firms seeking specialized assistance in navigating the convoluted realm of SIEM.
Third-party providers assume responsibility for administering, configuring, maintaining, and updating clients' SIEM installations, liberating internal staff from arduous chores and allowing them to concentrate on core competencies.
Engaging managed services furnishes establishments with state-of-the-art infrastructure supervised by tenured experts, ensuring round-the-clock vigilance and prompt intervention whenever needed.
Furthermore, outsourcing presents cost savings compared to recruiting, training, and retaining dedicated in-house specialists, especially for small to medium-sized organizations.
In conclusion, SIEM technology continues advancing at breakneck speeds, propelled by groundbreaking innovations such as AI, ML, integrated EDR, and SOAR.
Simultaneously, managed services and outsourcing provisions deliver affordable and accessible avenues for enterprises aiming to capitalize on cutting-edge cybersecurity defenses.
Navigating these trends warrants diligent attention from practitioners, researchers, and decision-makers keen on preserving organizational resiliency amid mounting digital hazards.
Conclusion
Summary of Key Points
Throughout this discussion, several salient aspects concerning SIEM have surfaced. First and foremost, SIEM serves as a cornerstone element in contemporary cybersecurity approaches, responsible for collating, examining, and responding to manifold security-related events scattered across vast digital landscapes.
Its indispensable nature derives primarily from its capacity to aggregate copious amounts of dissimilar data streams, subsequently subjecting them to elaborate analyses aimed at recognizing nefarious conduct.
Second, the effective utilization of SIEM entails mastering an eclectic mix of skillsets, inclusive of comprehension surrounding security operations, log management, correlation rules, and threat intelligence.
Notably, professionals who possess experience in deploying and tweaking SIEM systems find themselves in high demand owing to the nuances involved in properly setting up these systems.
Lastly, SIEM's evolution trajectory reveals an unmistakable inclination toward infusing progressive technologies such as artificial intelligence, machine learning, and automation to improve accuracy, cut down false positives, and accelerate response times.
Additional Resources for Further Reading
Delving deeper into SIEM concepts and applications calls for tapping reputable sources chockfull of insightful information. Some suggested readings include:
- Security Information and Event Management (SIEM) Implementation, published by Network Pro Library.,offers a comprehensive guide to effectively managing network security. Authored by experts, it covers SIEM deployment, vendor products, incident response, business intelligence, and real-world case studies, providing invaluable insights for organizations. By David R. Miller (Author), Shon Harris (Author), Allen Harper (Author), Stephen VanDyke (Author), Chris Blask (Author).
- Crafting the InfoSec Playbook: Security Monitoring and Incident Response Master Plan* written by Jeff Bollinger (Author), Brandon Enright Matthew Valites, This practical guide by Cisco's Computer Security Incident Response Team emphasizes a data-centric approach to security, advocating for a comprehensive strategy beyond reliance on tools alone.
- SECURITY INFORMATION AND EVENT MANAGEMENT (SIEM): Architecture, Deployment and Best Practices*, authored by Ali Hadi, stands out as a compendium brimming with architectural diagrams, implementation tips, and recommended practices relating to SIEM projects.
Exploring these resources promises to expand horizons and sharpen acumen vis-à-vis SIEM functionality and ramifications.
Glossary of Terms
Unfamiliar jargon often hinders comprehension, particularly when encountering novel topics. Thus, below is a glossary demystifying certain terminologies frequently appearing throughout this exploration:
- Log: Records generated by software applications, operating systems, or networking equipment capturing discrete events transpiring within a computer system. Examples comprise authentication attempts, network connections, program errors, etc.
- Correlation Rules: Directives guiding SIEM engines in associating seemingly disparate entries spread across multifarious logs. Well-crafted correlation rules enable identification of meaningful relationships harboring tangible implications.
- False Negatives: Instances wherein a SIEM fails to flag potentially harmful actions despite their existence. An abundance of false negatives erodes confidence in the system's ability to detect genuine threats.
- False Positives: Occasions whereupon benign occurrences erroneously get tagged as malignant. Surplus false positives result in wasted resources spent pursuing non-issues.
- Normalization: Procedure involving reformatting raw log data into uniform structures conducive to consistent processing and interpretation. Standardization reduces ambiguity and facilitates comparisons between otherwise incongruent datasets.
- Alert Escalation: Progressively intensifying notification cascades initiated once preset triggers activate inside a SIEM platform. Successive stages might involve transmitting messages to higher echelons of the IT department until receiving requisite attention.
- Threat Intelligence: Curated knowledge bases accumulating insights gleaned from observing cybercriminal exploits, tactics, and motifs. Ingesting threat intelligence feeds keeps SIEMs updated with latest known adversaries, henceforth improving their ability to spot novel assault vectors.
Understanding these definitions proves instrumental in grasping intricate facets integral to SIEM technology and its broader implications.