Designing and Building a Global Security Operations Center (SOC)
The importance of establishing and developing a Global Security Operations Center (SOC) becomes evident as a vital strategy for enterprises to efficiently mitigate such complex hazards. In recent times, many enterprises have faced a rise in network risks, leading to a reevaluation of their security protocols.
Amidst this constantly changing landscape, which encompasses various challenges like digital assaults, malware, DDOS attacks, ransomware, and unauthorized access attempts, there are significant risks to critical infrastructure and data integrity.Exploring the Modern Cyber Threat Landscape for a Global Security Operations Centers (SOCs)
The range of digital dangers underscores the necessity for a thorough defense strategy for headquarters. These risks typically fall into several primary groups: Advanced Cyber Attacks: Advanced persistent dangers (APTs) are ongoing digital assaults that target companies persistently and stealthily, posing significant dangers due to their continuous nature. Dynamic Attack Methods: Hacker groups continuously develop innovative techniques, such as viruses, malware, and ransomware, to breach defenses. It is crucial to keep safety measures up-to-date to counter these evolving risks effectively.Persistent Safety Breaches: Despite strong safety measures, attackers often succeed in infiltrating setups and exfiltrating information through unauthorized access, resulting in information loss events.
In today's rapidly evolving digital defense landscape, prioritizing proactive measures, continuous surveillance, and leveraging advanced analytics are globally imperative. The subsequent sections of this article will explore the pivotal role of a Global Defense Hub in implementing these strategies, thus strengthening enterprise data protection posture across diverse regions.
Foundations of an Effective Global Security Operations Center (SOC)
The central hub of modern enterprise cybersecurity acts as a fortress against diverse vulnerabilities. Its significance lies in its proactive approach to risk identification, rapid handling of situations, and continuous monitoring to protect critical assets from cyberattacks and vunerabilities.
Defining the Key Aspects of a SOC
A Global Security Operations Center (SOC) serves as a centralized entity committed to live surveillance and defense against digital risks. Specializing in digital protection, this Digital surveillance Hub seamlessly integrates advanced instruments, highly skilled analysts, and robust protocols. Notifications are promptly reviewed by the group of accountable experts to provide swift assistance when needed.
This collaboration empowers the Hub to efficiently detect, analyze, and respond promptly to events. By leveraging advanced instruments like intrusion spotting frameworks and cyber defense platforms, both the skilled experts within the Command Post and an individual expert continuously assess and address evolving dangers.
Implementing strong protocols guarantees a methodical and efficient approach to addressing and reducing occurrences, guided by collective expertise. This comprehensive combination of cutting-edge tools, skilled analysts, and reliable protocols establishes a seamless defense system, ensuring ongoing protection for organizational digital assets and infrastructure.
Amidst evolving digital threats, the digital defense unit and individual experts remain proactive, adapting flexibly to mitigate risks.
SOC Components and Architecture
A system dedicated to protection generally consists of several vital components. These elements collaborate to build a robust defense framework, improving an entity's capacity to identify, evaluate, respond to, and recover from events effectively. They collectively contribute to establishing a resilient defense architecture, enhancing an entity's ability to manage events proficiently.
Process in a Global Security Operations Center (SOC)
[caption id="attachment_9501" align="aligncenter" width="2560"]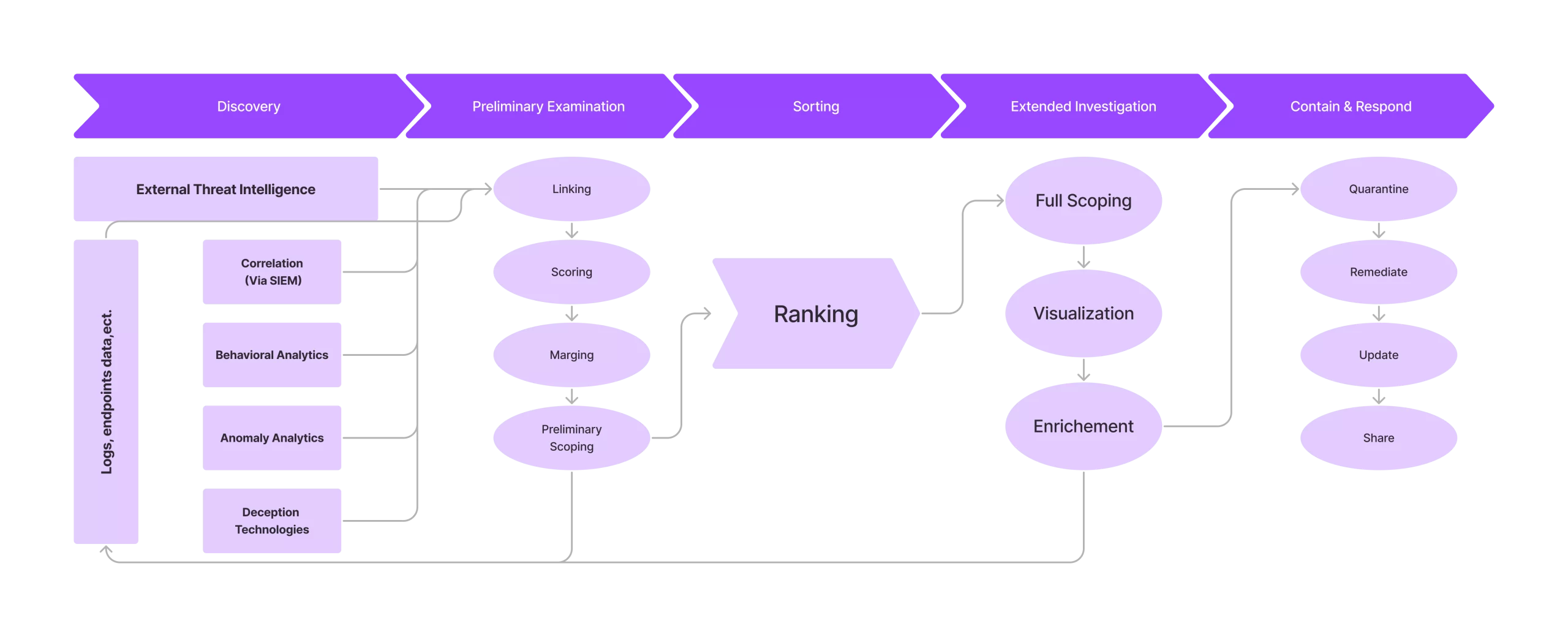 Figure 1. Integration and structuring of various processes across security and IT operations in threat management plans within a SOC (Security Operations Center).[/caption]
Figure 1. Integration and structuring of various processes across security and IT operations in threat management plans within a SOC (Security Operations Center).[/caption]
The operational aspect of safeguarding involves structured workflows and methodologies to detect, respond to, and mitigate digital vulnerabilities. It includes well-defined procedures, incident response strategies, and coordination mechanisms guiding experts through different scenarios, aiming to establish a systematic and efficient approach to addressing online risks, ensuring a unified and coordinated response.
This systematic approach comprises recognition, examination, containment, eradication, restoration, and ongoing refinement stages, facilitating the oversight of incident progression from identification to resolution, thereby enhancing information security and human aspects of cybersecurity.
The Process facet ensures a uniform and synchronized reaction, fostering cooperation among Global Security Operations Center (SOC) unit members and other stakeholders in the cyberdefense realm. By applying standardized procedures, the unit promotes a shared understanding of the reaction process, facilitating collaboration during urgent circumstances, vital for addressing intricate and evolving online threats.
[caption id="attachment_9417" align="aligncenter" width="490"]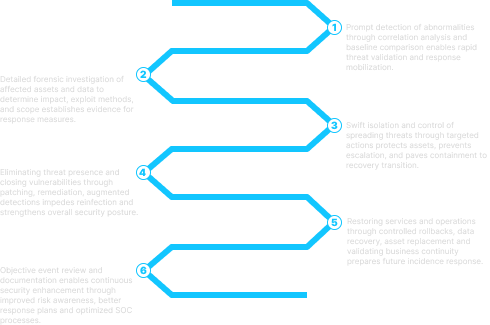 The Security Incident Response Process diagram is organized in six key pillars, starting with incident detection on the left through threat eradication and recovery on the right. Arrows connect the pillars to indicate transition flow.[/caption]
The Security Incident Response Process diagram is organized in six key pillars, starting with incident detection on the left through threat eradication and recovery on the right. Arrows connect the pillars to indicate transition flow.[/caption]
Moreover, the Process aspect incorporates routine training sessions and simulated drills to enhance the group's skills and flexibility in response to changing circumstances. Engaging in simulated situations and continuous training allows experts to refine their abilities, evaluate the effectiveness of current procedures, and stay prepared for new challenges.
The importance of People in the Global Security Operations Center (SOC)
In this scenario, the 'people' aspect pertains to the individuals comprising the team responsible for overseeing, identifying, and addressing issues within a company. Skilled professionals, including analysts, coordinators, and intelligence specialists, play a pivotal role in strengthening the resilience of this team.
Additionally, clear delineations of responsibilities, ongoing learning, and specialized skills ensure swift and effective responses to challenges. Defined roles facilitate seamless operations, enabling each member to leverage their abilities efficiently. Continuous education is essential for staying updated on current trends and technologies, fostering a proactive approach to maintaining security.
Furthermore, fostering open communication and collaboration among unit members and relevant entities fosters cohesion and overall risk awareness. Regular dialogue improves the team's efficiency and its ability to promptly tackle emerging dangers. Collaborative initiatives with external entities to exchange insight information strengthen the collective effort against online hazards.
At its core, the "People" aspect ensures a strong and adaptable stance, guaranteeing resilience in an ever-changing environment. Essential components like clearly defined roles, continuous training, and collaborative communication foster a proactive unit capable of efficiently safeguarding digital assets. Additionally, the unit is responsible for ensuring alerts are addressed promptly.
The Technology in a Global Global Defense Hubs
The technological component of a Global Defense Hubs includes advanced solutions for robust digital protection in organizations. Among these software apps, SIEM, such as IBM QRadar, aggregates and analyzes logs in live to bolster suspicious activity identification. Additionally, Intrusion Detection and Prevention Systems (IDS/IPS), like Cisco Firepower, monitor and prevent unauthorized connectivity. Firewalls, such as Palo Alto Networks, establish secure barriers, while weakness identification aids like Tenable Vulnerability Management identify and rectify system weaknesses. Moreover, vulnerability Identification Software, like ThreatConnect, enrich contextual information. Furthermore, tools for handling incidents, such as Resilient (by IBM Security), lead analysts through documented processes, supported by forensic analysis software applications like EnCase Forensic. Additionally, incorporating SOAR platforms like IBM QRadar SOAR automates responses, bolstering incident resolution efficiency. Advanced Software Platforms converge to reinforce architecture, improving proactive anomaly identification, analysis, and resolution capabilities. Ultimately, these software products blend well. They boost security and simplify workflows, improving efficiency in handling digital incidents.Security Information and Event Management (SIEM)
[caption id="attachment_9455" align="aligncenter" width="1024"]Endpoint Detection and Response (EDR)
EDR monitors and responds to abnormal activities on individual devices (endpoints) to prevent, detect, and mitigate vulnerabilities. It ensures comprehensive protection by prioritizing the integrity of each individual device within the network, a critical aspect of a robust SOC.
IBM QRadar EDR and Symantec Endpoint Protection track and respond to unusual device activities. Global SOCs rely on tools for entry point integrity, stressing log analysis's importance.
Vulnerability Management Tools
[caption id="attachment_9452" align="aligncenter" width="980"]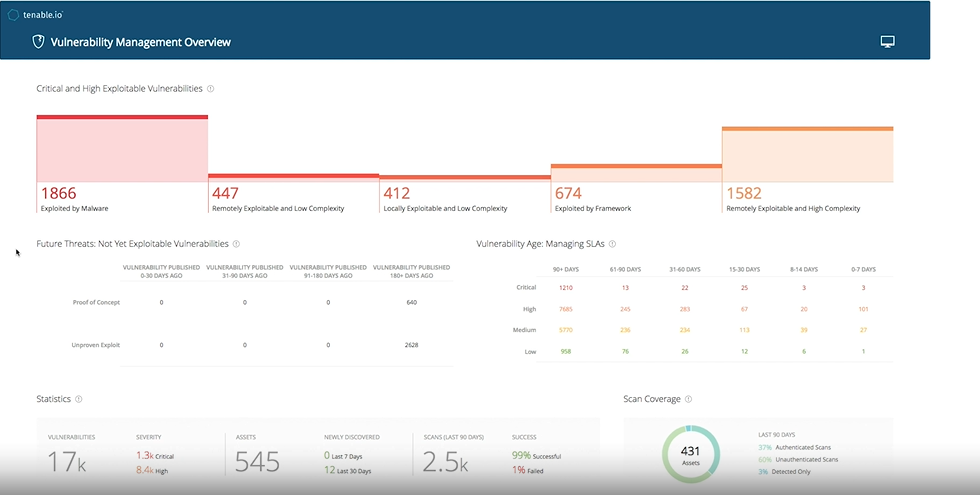 Intervalle Technologies partners with Tenable to fortify cybersecurity defenses through expert deployment of Vulnerability Management solutions.[/caption]
Intervalle Technologies partners with Tenable to fortify cybersecurity defenses through expert deployment of Vulnerability Management solutions.[/caption]
Addressing vulnerabilities proactively is vital for robust defense against online threats, focusing on identifying and rectifying weaknesses prior to exploitation. Modern platforms manage vulnerabilities, ensuring resilience of online safety hubs.
Top vulnerability detect software applications like Tenable.io Vulnerability Management, Nessus Professional, and Nessus Expert offer comprehensive coverage supported by predictive analytics and threat insight.
Leveraging instant insight into the attack surface and prioritized vulnerability information, SOCs can effectively allocate resources to address critical vulnerabilities and enhance IT resilience.
Threat Intelligence Platforms
[caption id="attachment_9454" align="aligncenter" width="1024"]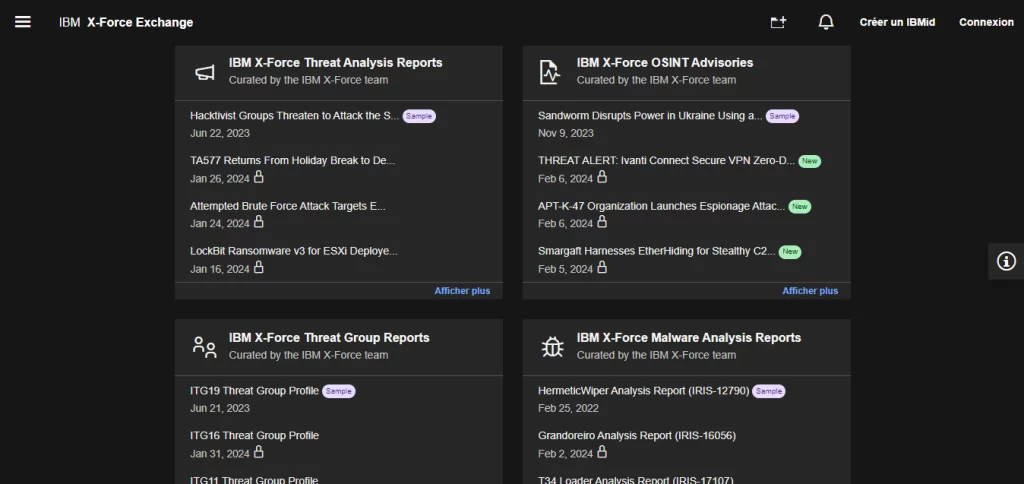 IBM X-Force Threat Analysis Reports[/caption]
IBM X-Force Threat Analysis Reports[/caption]
Insights analysis is crucial for Global Defense Hub to obtain insights into the tactics, techniques, and procedures of existing and emerging actors. Advanced IT risk assessment software applications like IBM X-Force and Symantec GIN ingest records from diverse sources, analyze it for actionable insights, and deliver high-fidelity insight on possible risks.
By leveraging insights into vulnerabilities, SOCs can enhance identification coverage for both known and unknown dangers, conduct thorough threat hunting activities, and refine occurrence reaction workflows. Solutions like IBM QRadar Threat Analysis offer valuable insights into high-risk, vulnerabilities, and adversary tactics, enhancing the decision-making capabilities of SOCs. This enables them to proactively anticipate, detect, and mitigate digital attacks.
Forensic Tools
In-depth scrutiny and meticulous analysis play a critical role in the operations of a global center focused on probing intrusion breaches, identifying underlying issues, assessing business ramifications, and gathering evidence to enhance hazard Control. Leading-edge digital investigative software applications like AccessData Forensic Toolkit (FTK) and IBM QRadar offer indispensable functionalities for thorough breach investigations.
Sophisticated forensic analysis software app empower operational centers to not only swiftly address intrusions but also craft strategic reactions, delivering conclusive insights, evidence-supported suggestions, and detailed technical analysis essential for fortifying against future vunerabilities. Their capabilities position them as indispensable resources for members pursuing thorough, efficient, and precise examination of incidents related to safeguarding digital assets.
Security Orchestration, Automation, and Response (SOAR)
Security Orchestration, Automation, and Response (SOAR) integrate security tools seamlessly. They streamline intrusion reaction, enhancing effectiveness and consistency.
They empower security teams by simplifying processes and enabling a proactive approach to IT risk mitigation. Leading SOAR platforms, like IBM SOAR, consolidate security software and automate actions. They enhance efficiency in event operations.
Navigating SOC Regulatory Frameworks
Review and interpret global information protection regulations, such as GDPR, HIPAA, and regulations akin to Loi 18-07. This extensive examination is vital for grasping record localization, privacy, and conformity mandates when establishing resilient protection protocols. Additionally, it guarantees a thorough understanding of varied regulatory landscapes, fostering protocols congruent with international information protection standards.
Leveraging Data IT Risk Intelligence for SOCs
Leverage local insight resources to understand prevailing attack vectors and trends at a regional level. Engage with digital defense communities in various regions to gain insights into local actors and their tactics. Promote collaboration across regions to foster a global outlook. Integrate diverse insights for comprehensive defense strategies.
Overcoming Unique SOC Implementation Challenges
Identify industry-specific IT risk challenges across global enterprises in finance, industry, technology, and government sectors. Confront complexities tied to multinational operations, compliance, and the pervasive cross-border IT risk. Extend the approach universally, acknowledging industry nuances worldwide. Operations Center (SOC) strategies are adaptable and capable of addressing sector-specific challenges on a global scale.
Crafting a tailored protection framework for multinational corporations requires understanding local regulations and digital defense complexities. It also involves adapting to evolving landscapes.
This groundwork enables experts to build a resilient architecture customized to each digital defense landscape. It provides superior defense against the most sophisticated global dangers.
Implementing Core SOC Defense Capabilities
When establishing a safe environment for your company, paying meticulous attention to essential protection elements is paramount. These elements form a strong digital defense architecture. They address specific requirements and obstacles for IT Security Leaders.
Relevance of Global Defense Measures
Incorporating worldwide protection measures across varied environments meets conformity mandates. Examples include PCI-DSS and local regulations like Loi 18-07 or GDPR. Tailoring global protection frameworks to regional regulatory contexts is vital. It guarantees a comprehensive defense stance resonating with unique regional intricacies.
Data centers and Web Application Security
Ensuring high-quality safeguarding for Server farms requires a strong approach. improving essential architecture, deploying advanced firewalls, and ongoing tracking are essential. Meanwhile, securing web applications demands stringent access controls, enhanced intrusion prevention, and web application firewalls. These steps serve as effective protections against online risks, bolstering your resistance to possible attacks.
Compliance, precautionary measures, and Continual Improvement of the Global Defense Hub
Compliance, precautionary measures, and Continual Improvement are fundamental pillars in strengthening the effectiveness and resilience of SOCs worldwide. These essential elements, managed by responsible professionals, play critical roles in maintaining a strong defense posture, adapting to evolving dangers, and ensuring continuous enhancements in the protection landscape across diverse regions. Logs will be read meticulously to verify adherence to standards and responsibly implement proactive measures throughout the organization.
Let's break it down:
Compliance Strategies for digital Defense
Developing effective conformity strategies for digital defense requires a comprehensive approach that encompasses governance, risk control, and compliance (GRC) principles.
Leveraging frameworks like the NIST Cybersecurity Framework is essential. Guidance from organizations such as the Command, Control, and Interoperability Division enhances digital defense posture. Additionally, Understanding the workplace impact of AI is pivotal. Aligning with resources like US-CERT is essential.Implementing enterprise risk control practices, granular configuration automation, and robust SIEM systems are essential components. Conformity with policies like the National digital Security Policy 2013 further strengthens organizational resilience against digital dangers.
Legal & Regulatory Adherence
Ensuring legal conformity in Global Defense Hubs involves aligning practices with laws, regulations, and standards. This ensures regulatory compliance and operational efficiency. Meeting conformity requirements helps the SOC avoid legal repercussions and financial penalties. This safeguards its reputation and financial stability.
Reduced Legal Risks
Compliance with established standards and regulations minimizes the organization's exposure to legal risks. By meeting conformity requirements, the SOC mitigates the likelihood of facing legal repercussions and financial penalties, thereby safeguarding its reputation and financial stability.
Implementing a Structured Framework in Cybersecurity Operations Hubs Regulatory frameworks like NIST and ISO27001 offer a structured method for deploying and upholding protective measures within the protection hub. These frameworks provide guidance and optimal strategies to help members establish strong defense protocols and ensure continuous compliance with regulatory standards.Strengthening IT Risk Oversight through Advanced Centers
Identifying menaces
Preventive measures within a Global Defense Hub involve the essential task of identifying possible risks and vulnerabilities existing in the environment. By conducting thorough IT risk assessments, the center can gain insights into the various hazards that may compromise operations or information security.
Prioritizing Mitigation
Effective precautionary measures enables members within the SOC to prioritize mitigation efforts based on the severity and likelihood of identified risks. By assessing risks, the team can allocate resources and attention to critical areas that have the possibility to significantly impact operations or compromise information integrity.
Adaptive Strategies
Risk control enables the creation of flexible strategies to tackle evolving dangers. Through ongoing tracking and reassessment of risks, the SOC can proactively adjust its defense measures to counter emerging risks and vulnerabilities, guaranteeing resilience against dynamic defense challenges.
Utilizing Network Security Centers for Continuous Improvement
Cyber Defense Center play a pivotal role in continuous improvement strategies for information security and IT risk governance. Through comprehensive services such as business continuity planning, vulnerability assessment, and threat analysis platform integration, They provide robust security supervision. Additionally, their expertise extends to disaster recovery and business continuity auditing, fostering digital resilience across organizations.
Adaptation to Changes
In the dynamic realm of digital defense, protection centers must continuously evolve to stay ahead of emerging menaces. This requires embracing a culture of ongoing enhancement to foster a flexible environment capable of integrating insights and innovations in protective technology.
Efficiency Enhancement
Regular assessment and refinement of processes within it are vital for enhancing efficiency. By systematically evaluating workflows and procedures, it can optimize resource allocation and action timings, thereby improving overall operational efficiency.
Enhanced Resilience
Continuous enhancement endeavors enhance the resilience of the protection hub by fostering a culture of learning and adaptation. Embracing feedback and integrating insights from previous intrusions enables it to effectively counter emerging risks and challenges, ensuring its capacity to adapt and excel in a constantly evolving digital defense environment.
Conclusion
The establishment and effective operation of a SOC stand as a linchpin in safeguarding enterprises against a dynamic information risk landscape. The insights gleaned from the preceding discussion underscore the pivotal role of AI and Data Protection Apps in fortifying endpoints, supporting efficient event handling and enhancing the prioritization method.
Moving forward, the evolving landscape demands a proactive approach, leveraging advanced analytics, and embracing global information protection paradigms. The convergence of digital resilience with adherence measures, such as Loi 1807 amplifies the importance of holistic digital precautionary measures frameworks. IT Security Leaders must prioritize continuous monitoring, deploy advanced anomaly identification mechanisms, and fortify server farm protection alongside enhanced web application and connectivity control. Embracing user behavior analytics becomes imperative to combat sophisticated cyber-attacks and mitigate risks effectively.


