What Can SIEM Detect? A CISO's Technical Guide to Modern Threats
Understanding what can SIEM detect is fundamental for building a resilient cybersecurity posture. For years, Security Information and Event Management (SIEM) solutions have served as the central nervous system for security operations centers (SOCs). They aggregate vast oceans of data from across the enterprise.
This includes logs from firewalls, servers, endpoints, and cloud applications. By correlating this information, a SIEM provides the context needed to identify malicious activity that would otherwise remain invisible.
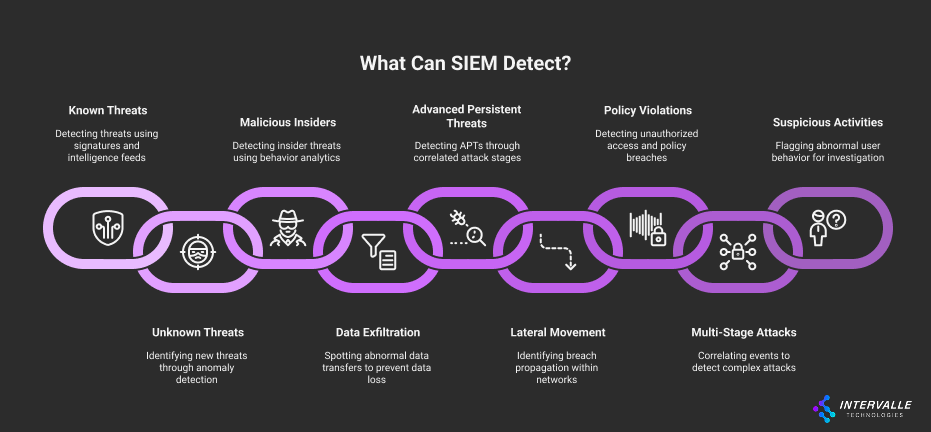
However, the question of what a SIEM can detect has evolved dramatically. Early SIEMs were primarily log collectors and rule-based alerting engines. They were effective at spotting known threats with clear signatures.
Today’s threat landscape is dominated by stealthy, multi-stage attacks and sophisticated insider threats. Consequently, modern SIEM platforms have adapted. They now incorporate machine learning, behavioral analytics, and threat intelligence to uncover subtle anomalies and complex attack patterns.
This guide provides a technical deep dive for CISOs, SOC managers, and IT directors. We will explore the full spectrum of threats a modern SIEM can identify. We will also cover how it accomplishes this and how you can maximize its value.
The Evolving Threat Landscape: Why Unified Visibility Is Paramount
The modern digital environment is a complex, distributed ecosystem. It spans on-premises data centers, multiple cloud providers, and countless remote endpoints. This complexity creates visibility gaps that threat actors are eager to exploit.
A recent IBM report found that the average cost of a data breach reached $4.45 million in 2023. This unde rscores the financial imperative of effective threat detection. Without a
centralized view, security teams are forced to manually piece together clues from dozens of siloed security tools. This appr oach is slow, inefficient, and prone to human error.
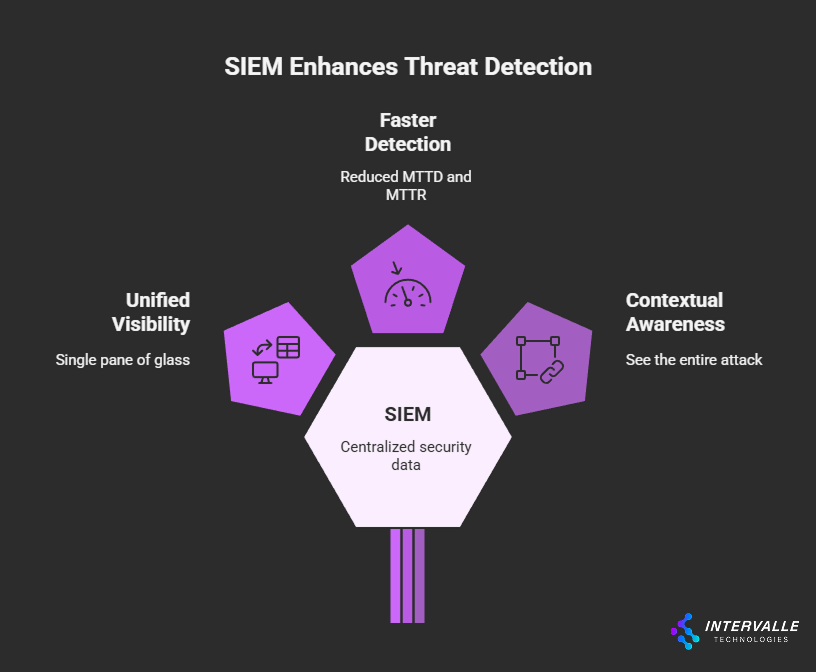
A SIEM directly addresses this challenge. It acts as a single pane of glass, ingesting and normalizing data from every corner of the IT infrastructure. This unified visibility is no longer a luxury; it is a necessity for survival.
It empowers security teams to see the entire attack chain. They can connect a suspicious login from a new location to an unusual process execution on a critical server. This context is crucial for distinguishing a genuine threat from a benign false positive.
Ultimately, the goal is to reduce the mean time to detect (MTTD) and mean time to respond (MTTR). Effective security operations depend on this capability.
The Proliferation of Sophisticated, Multi-Vector Attacks
Threat actors no longer rely on simple, single-pronged attacks. Modern adversaries, including advanced persistent threats (APTs), employ multi-vector campaigns. These attacks unfold slowly over weeks or months.
They use a combination of techniques to breach defenses, move laterally, and exfiltrate data. An attack might start with a spear-phishing email to compromise an employee’s credentials. The attacker then uses those credentials to access a public-facing application.
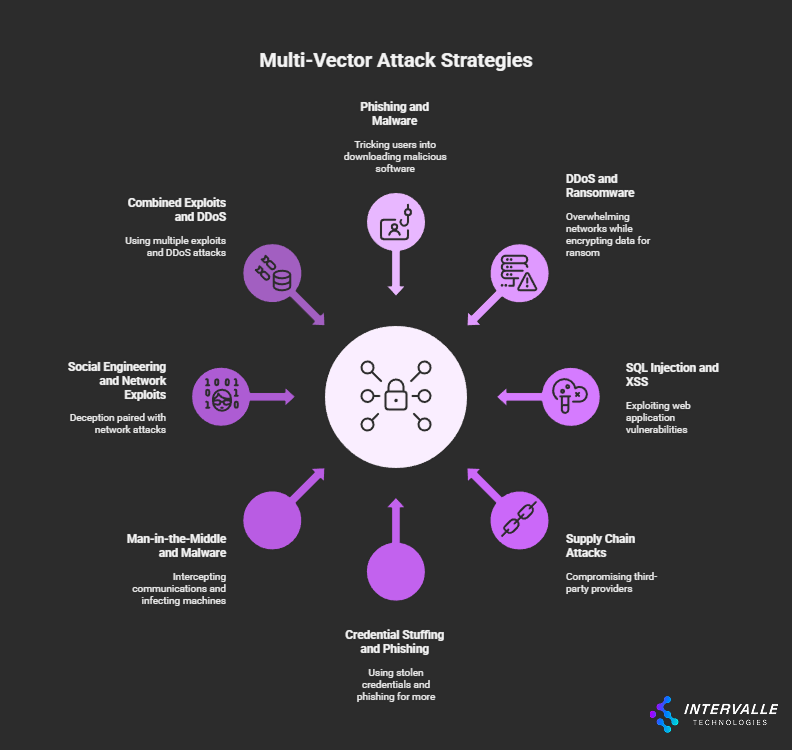
From there, they exploit a vulnerability to gain a foothold on the internal network. Next, they move laterally to find and exfiltrate sensitive data. Each step of this attack generates log entries on different systems.
The email server logs the phishing attempt. The web application firewall logs the suspicious login. The endpoint detection and response (EDR) agent logs the malicious process.
A SIEM is the only tool that can collect, correlate, and analyze these disparate events in real time. It pieces together the puzzle to reveal the full scope of the attack. Without this correlation, each event might be dismissed as a minor, isolated anomaly.
The Insider Threat: A Persistent and Elusive Challenge
Not all threats originate from outside the organization. Insider threats, whether malicious or accidental, pose a significant and growing risk. According to the 2023 Verizon Data Breach Investigations Report, 20% of breaches involve an internal actor.
These threats are notoriously difficult to detect with traditional security tools. Firewalls and antivirus software are designed to stop external attacks.
They offer little protection against a user who already has legitimate access credentials. This is where understanding what can SIEM detect becomes critical for internal risk management.
A SIEM equipped with User and Entity Behavior Analytics (UEBA) can baseline normal user activity. It learns what applications a user typically accesses. It knows what time of day they usually work.
It understands how much data they normally transfer. When a user’s behavior deviates significantly from this baseline, the SIEM can generate an alert.
For example, a user who suddenly accesses a sensitive database for the first time at 3:00 AM would trigger a high-fidelity alert. This behavioral approach is essential for uncovering compromised accounts, malicious insiders, and negligent employees before they cause significant damage.
How SIEM Technology Works: The Core Detection Engine
To truly grasp what a SIEM can detect, one must understand its underlying technical architecture. At its core, a SIEM performs four critical functions: data aggregation, normalization, correlation, and presentation. It is the sophisticated interplay between these functions that enables the detection of complex threats.
The process begins with collecting data from a massive array of sources. These sources include network devices, security appliances, servers, applications, and cloud services. The more diverse and comprehensive the data sources, the greater the SIEM's detection capabilities.
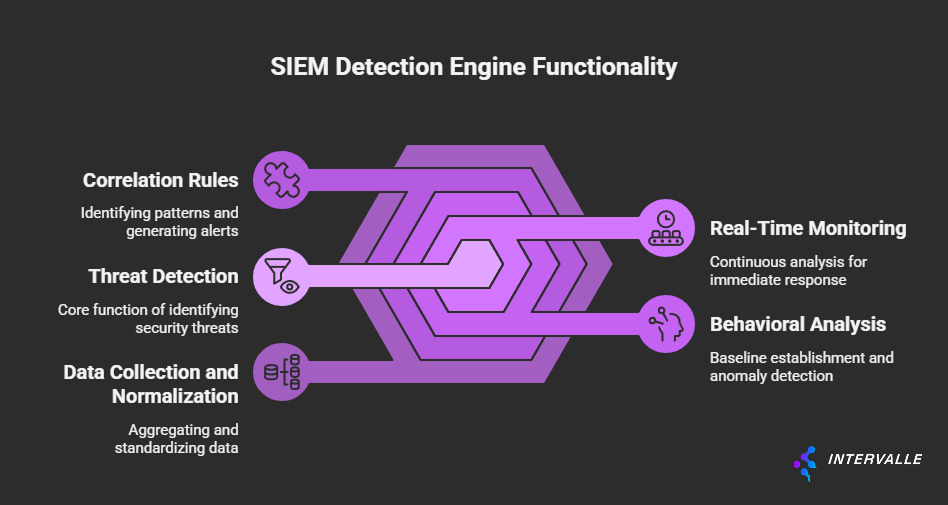
This raw data, however, comes in many different formats. A firewall log looks very different from a Windows event log or an AWS CloudTrail log. This is where normalization comes in.
The SIEM parses these disparate logs into a common, standardized format. This allows the correlation engine to analyze events from different sources in a consistent manner. It is this correlation that transforms raw data into actionable security intelligence.
By applying rules, statistical models, and machine learning algorithms, the SIEM identifies relationships between events that signal a potential threat. The final step is presentation, where alerts and reports are displayed on a dashboard for security analysts to investigate.
Aggregation and Normalization: Creating a Single Source of Truth
The foundation of any effective SIEM solution is its ability to aggregate and normalize data at scale. A typical enterprise generates terabytes of log data every day. A SIEM must be able to ingest this firehose of information without dropping events.
It uses agents or agentless collection methods to pull data from thousands of log sources. These sources can include firewalls, intrusion detection systems (IDS), servers, domain controllers, and cloud platforms like Azure or GCP.
Once collected, the raw logs are parsed and normalized. Normalization is a critical step. It involves extracting key fields from each log entry and mapping them to a common schema.
For example, fields like `source_ip`, `destination_ip`, `user_name`, and `event_id` are standardized across all log types. This creates a unified data set that the correlation engine can work with.
Without normalization, it would be impossible to write a correlation rule that looks for a suspicious login on a firewall followed by unusual activity on a specific server. Normalization creates the single source of truth that underpins all subsequent detection logic.
The Power of Correlation Rules and Threat Intelligence Feeds
Correlation is the analytical heart of a SIEM. This is where normalized events are compared against a set of rules to identify patterns of interest. These rules can be simple or incredibly complex.
A simple rule might be to alert on five failed login attempts for the same user within one minute. A more complex rule could look for a user logging in from a new geographic location, accessing a sensitive file share, and then attempting to upload a large amount of data to an external site, all within a 30-minute window. This is a classic data exfiltration pattern that would be missed without event correlation.
To enhance its detection capabilities, a modern SIEM integrates with external threat intelligence feeds. These feeds provide up-to-date information on known malicious IP addresses, domain names, file hashes, and attacker tactics, techniques, and procedures (TTPs). When an event in the SIEM matches an indicator of compromise (IOC) from a threat intelligence feed, it automatically raises a high-priority alert.
This integration enriches the internal log data with external context. It helps security teams quickly identify known threats and prioritize their response efforts. This proactive approach is a key part of advanced threat detection.
What Can a SIEM Detect? A Comprehensive Breakdown
The primary function of a SIEM is to detect security threats and anomalous behavior. Its capabilities are vast, covering a wide range of attack vectors and malicious activities. By centralizing security data, a SIEM provides the context needed to spot indicators of compromise that would otherwise go unnoticed.
The depth of what can SIEM detect depends on the quality of its data sources, the sophistication of its correlation rules, and the integration of advanced analytics like UEBA. Below, we break down the specific types of threats and activities a well-tuned SIEM is designed to uncover across different domains.
Detecting External Threats and Network Intrusion Attempts
A SIEM excels at identifying threats originating from outside the network perimeter. It analyzes logs from firewalls, VPNs, proxies, and IDS/IPS devices to spot suspicious inbound and outbound traffic. This allows it to detect the earliest stages of an external attack, often before a full compromise occurs.
Brute-Force Attacks and Password Spraying
One of the most common initial access techniques is credential abuse. A SIEM can easily detect brute-force attacks by correlating multiple failed login attempts against a single account from a single source IP.
It can also identify password spraying, a more subtle technique where an attacker tries a few common passwords against many different user accounts. A correlation rule can look for a high ratio of failed to successful logins across the entire organization within a short timeframe.
Phishing and Spear-Phishing Indicators
While a SIEM does not directly analyze email content, it can detect the technical indicators of a successful phishing attack. For example, it can correlate logs from an email security gateway with web proxy logs.
An alert could be triggered if a user clicks a link in a suspicious email and is redirected to a known malicious domain. It can also detect if a user’s machine subsequently initiates a connection to a command-and-control server.
Command and Control (C2) Communication
After gaining an initial foothold, malware will often establish a connection to a C2 server. This allows the attacker to control the compromised system remotely. A SIEM can detect this C2 traffic in several ways.
It can correlate firewall and DNS logs to identify connections to known malicious domains or IP addresses provided by threat intelligence feeds. It can also use behavioral analysis to spot unusual communication patterns, such as a workstation communicating with a rare external IP address over a non-standard port.
Identifying Insider Threats and Compromised Accounts
Detecting threats from within is a major strength of modern SIEM platforms, particularly those with integrated UEBA capabilities. By focusing on behavior rather than signatures, a SIEM can uncover malicious insiders and accounts that have been compromised by external attackers.
User and Entity Behavior Analytics (UEBA)
UEBA is a game-changer for insider threat detection. It uses machine learning to build a dynamic baseline of normal behavior for every user and device on the network. The system learns who typically accesses what data, from where, and at what times.
When a user's activity deviates significantly from their established baseline, the SIEM raises a risk score. This allows it to detect events like an employee suddenly accessing HR records they have never touched before or a server unexpectedly attempting to scan the network.
Privilege Escalation and Unauthorized Access
A key goal for any attacker, internal or external, is to escalate their privileges to gain administrative access. A SIEM can monitor for signs of privilege escalation by analyzing Windows and Linux event logs.
It can detect the creation of new administrative accounts, the addition of a user to a privileged group, or the use of tools like Mimikatz to dump credentials from memory. It can also alert on any access to critical systems or data that violates a user's role-based access control policies.
Data Exfiltration and Intellectual Property Theft
The ultimate goal of many attacks is to steal sensitive data. A SIEM can detect data exfiltration by monitoring for large or unusual outbound data transfers. It can correlate logs from data loss prevention (DLP) systems, file servers, and network devices.
A correlation rule could flag an event where a user who has recently given their notice of resignation suddenly downloads a large volume of files from a proprietary source code repository. Other indicators include data being sent to cloud storage services or transferred via unusual protocols.
Uncovering Malware and Ransomware Activity
A SIEM is a powerful tool for detecting the presence of malware, including ransomware, on the network. It does so by identifying the various TTPs that malware uses to infect systems, spread laterally, and achieve its objectives. It provides a macro view of an infection that EDR tools, focused on a single endpoint, might miss.
Initial Access and Execution Signatures
A SIEM can correlate endpoint security logs to detect the initial execution of a malicious file. It can ingest alerts from EDR and antivirus tools.
It can also identify suspicious process execution chains, such as a Microsoft Office document spawning a PowerShell script that then downloads a file from the internet. This chaining of events provides high-fidelity evidence of a malware infection in progress.
Lateral Movement and Persistence Mechanisms
Once inside, malware often attempts to move laterally to other systems on the network. A SIEM can detect this by monitoring for suspicious authentication patterns, such as a single user account attempting to log into multiple workstations in rapid succession.
It can also analyze network traffic for signs of scanning activity. Furthermore, it can detect persistence mechanisms, such as the creation of new scheduled tasks or modifications to registry run keys, which malware uses to survive a system reboot.
Monitoring for Compliance Deviations and Policy Violations
Beyond threat detection, a SIEM is an indispensable tool for compliance and auditing. It provides the evidence needed to demonstrate adherence to regulatory frameworks like PCI DSS, HIPAA, and GDPR.
It offers pre-built reports and dashboards to simplify the audit process. The scope of what can SIEM detect extends deeply into policy enforcement.
Tracking Access to Sensitive Data
For regulations like HIPAA or GDPR, organizations must control and audit all access to sensitive data. A SIEM can be configured to monitor access to specific file shares, databases, or applications containing protected health information (PHI) or personally identifiable information (PII). It can generate an alert and a detailed audit trail for every access event, including who accessed the data, when they accessed it, and from where.
Auditing System Configuration Changes
Maintaining secure system configurations is a key requirement of many compliance standards. A SIEM can track all changes to critical system configurations.
It can ingest logs from servers and network devices to monitor for unauthorized modifications to firewall rules, user access lists, or system hardening settings. This provides an auditable record of all changes and helps ensure that systems remain in a compliant state.
From Theory to Practice: Implementing a Proactive Detection Strategy
Deploying a SIEM is not a "set it and forget it" exercise. To unlock its full potential, organizations must develop a mature, proactive detection strategy. This involves careful planning, continuous tuning, and a commitment to integrating the SIEM into the core of their security operations.
The journey from a basic logging tool to a sophisticated threat detection engine requires both technical expertise and strategic vision. A well-implemented SIEM becomes the foundation for a threat-informed defense, enabling teams to move from a reactive posture to proactive threat hunting.
The success of a SIEM program hinges on several factors. It requires identifying the right data sources to ingest based on the organization's specific risk profile. It demands the development of custom correlation rules that align with business context and known threat models.
It also necessitates the integration of the SIEM with other security tools to create a cohesive ecosystem. At Intervalle Technologies, we have observed that organizations achieving the highest ROI from their SIEM investment are those that treat it as a continuous program, not a one-time project. This iterative approach ensures the platform evolves alongside the threat landscape.
Key Steps for Effective SIEM Deployment and Tuning
An effective SIEM implementation begins with a clear definition of objectives. What are the primary use cases? Is the focus on compliance, insider threats, or advanced threat detection?
This will dictate which log sources are most critical. A common mistake is to ingest everything, leading to a noisy, unmanageable system. Instead, organizations should take a phased approach, starting with high-value sources like domain controllers, firewalls, and critical servers.
Once data is flowing, the real work of tuning begins. Out-of-the-box correlation rules are a good starting point, but they often generate a high volume of false positives. Security teams must customize these rules and create new ones based on their unique environment.
This involves understanding what normal looks like and writing rules to detect deviations from that baseline. Regular rule review and optimization are essential to maintain a high signal-to-noise ratio. This process allows analysts to focus on genuine threats, enabling a more swift incident response.
Case Study: Detecting a Low-and-Slow Attack with SIEM
Consider a hypothetical financial services company. An attacker compromises an accountant's credentials via a phishing email. The attacker logs into the accountant's workstation outside of normal business hours.
The SIEM correlates the VPN log showing a login from an unfamiliar IP address with the Windows event log showing a successful login at 2:00 AM. This alone might not be a high-priority alert.
However, the attacker then uses PowerShell to query Active Directory for a list of database administrators. The SIEM’s UEBA module flags this as anomalous behavior for an accountant. A few hours later, the attacker uses the RDP protocol to connect from the accountant's machine to a critical database server.
The SIEM correlates these three distinct events—the anomalous login, the unusual process execution, and the suspicious RDP connection. By linking these low-fidelity indicators over time, the SIEM creates a single high-fidelity alert.
It reveals a clear attack path, allowing the SOC team to intervene before any data is exfiltrated. This demonstrates how a SIEM detects threats that individual point solutions would miss.
The Future of Detection: Next-Generation SIEM Capabilities
The field of security information and event management is constantly evolving. As attackers develop new techniques, SIEM vendors are responding with more advanced capabilities. The future of SIEM is intelligent, automated, and cloud-native.
Next-generation platforms are moving beyond traditional rule-based correlation. They are leveraging artificial intelligence and machine learning to detect unknown threats and predict potential attacks. This shift is essential for keeping pace with the increasing volume and sophistication of cyber threats.
For CISOs and security leaders, it is crucial to understand these trends when making strategic investments. The focus is shifting from simple log management to comprehensive security analytics and operations platforms. Modern SIEMs are being integrated more tightly with other security tools, particularly Security Orchestration, Automation, and Response (SOAR).
This integration bridges the gap between detection and response. It allows organizations to automate routine security tasks and orchestrate complex incident response workflows. The question of what can SIEM detect is expanding to include what it can automatically respond to.
The Impact of AI and Machine Learning on Detection
Artificial intelligence (AI) and machine learning (ML) are at the forefront of SIEM innovation. These technologies enable a SIEM to analyze massive datasets and identify subtle patterns that are impossible for humans to spot.
Instead of relying solely on pre-defined rules, an AI-powered SIEM can learn the unique characteristics of an organization's IT environment. It can autonomously build and adapt behavioral baselines for users and systems.
This allows for the detection of zero-day threats and novel attack techniques that have no known signature. For example, an ML model could identify a new strain of ransomware by recognizing its characteristic pattern of rapid file encryption, even if the ransomware’s file hash is unknown. AI also helps to reduce alert fatigue by automatically correlating related alerts into a single incident and assigning a risk score.
This helps analysts prioritize their efforts and focus on the most critical threats. The expertise offered by firms like Intervalle Technologies can be invaluable in harnessing these advanced capabilities.
Integrating SIEM with SOAR for Automated Response
Detecting a threat is only half the battle. The other half is responding quickly and effectively to contain it. The integration of SIEM with SOAR platforms is a powerful force multiplier for security teams.
When a SIEM detects a credible threat, it can automatically trigger a SOAR playbook. This playbook is a pre-defined workflow that orchestrates a series of response actions across different security tools.
For example, if a SIEM detects malware C2 communication from a user's laptop, it can trigger a SOAR playbook that automatically quarantines the device on the network via the network access control (NAC) solution. It could also disable the user's account in Active Directory and open a ticket in the IT service management system.
This automation dramatically reduces the mean time to respond (MTTR). It frees up human analysts to focus on more complex investigation and strategic tasks, transforming the SOC from a reactive to a proactive function.
Conclusion: Maximizing Your SIEM for Proactive Defense
In today's complex cyber landscape, a SIEM is an essential component of any mature security strategy. The question of what can SIEM detect has a broader answer than ever before. Modern platforms have moved far beyond basic log aggregation.
They are sophisticated analytics engines capable of identifying external intrusions, insider threats, advanced malware, and compliance violations. By correlating events from across the entire IT ecosystem, a SIEM provides the unified visibility and contextual intelligence needed to combat today’s stealthy, multi-stage attacks.
For CISOs and security leaders, a SIEM is more than just a technology; it is a strategic asset. It provides the data-driven insights needed to understand and manage cyber risk effectively. However, realizing its full value requires a commitment to continuous improvement.
This includes thoughtful data source selection, ongoing rule tuning, and the adoption of next-generation capabilities like UEBA and AI. When properly implemented and managed, a SIEM empowers security teams to shift from a reactive to a proactive defense. It enables them to not only detect threats faster but also to hunt for them proactively, securing the organization against the challenges of tomorrow.
