I. Understanding SWIFT Attestation
SWIFT Attestation is a crucial process for financial institutions worldwide. It ensures compliance with SWIFT's security standards and best practices. This attestation impacts various stakeholders within banks, from CISOs to IT teams. Operations managers also play a key role in this process. Bank executives need to understand its importance for their organization's security and reputation. The attestation involves multiple steps and requires coordination across departments. Let's explore what SWIFT Attestation entails and why it matters to your bank.
What is SWIFT Attestation?
SWIFT attestation is an annual process where all users of the SWIFT financial messaging system must attest to their level of compliance with the mandatory security controls outlined in the SWIFT Customer Security Controls Framework (CSCF). The attestation involves a self-assessment against these controls, which is then shared with SWIFT and can be accessed by other SWIFT users.
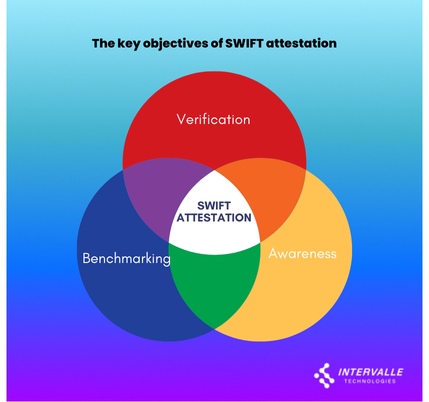
The key objectives of SWIFT attestation are:
Verification: It verifies that financial institutions have implemented the necessary controls to secure their SWIFT environment.
Awareness: It raises awareness within institutions about their security posture and areas that may require improvement.
Benchmarking: It allows institutions to benchmark their security controls against industry standards and peers.
Independent Assessment Requirement
To enhance the accuracy of attestations, SWIFT requires all users to perform an independent assessment as part of the attestation process. This can be done through an internal assessment by the 2nd or 3rd line of defense, or an external assessment by a qualified cybersecurity assessor.
SWIFT Attestation: Key Steps and Compliance
The SWIFT Customer Security Programme (CSP) mandates that all SWIFT users annually attest to their compliance with the Customer Security Controls Framework (CSCF). Consequently, this process ensures that organizations align with evolving security standards, safeguarding the integrity of the global financial network. Furthermore, by following the outlined steps, users can effectively demonstrate their commitment to robust cybersecurity practices.

Ultimately, this attestation not only fulfills regulatory requirements but also strengthens trust and transparency across the SWIFT network. Here's an overview of the attestation process.
1. Review the CSCF
Initially, each year, usually in July, SWIFT releases an updated version of the Customer Security Controls Framework (CSCF). Consequently, users must carefully review the revised controls and evaluate their current compliance status. Moreover, it’s crucial to identify any new or modified requirements, which will guide subsequent implementation efforts. Proactive planning ensures organizations stay aligned with SWIFT's evolving security expectations.
2. Implement Security Measures
After reviewing the CSCF, users must promptly implement the necessary security measures to align with the updated controls. Specifically, this involves strengthening local SWIFT-related infrastructure, refining security policies, and ensuring all practices meet the required standards. Timely action is essential, as it minimizes vulnerabilities and enhances overall cybersecurity resilience within the organization.
3. Conduct Independent Assessment
To ensure the credibility of the attestation, an independent assessment of all mandatory controls is required. Consequently, this assessment can be carried out by internal teams, such as Compliance or Internal Audit, or by external auditors. The goal is to verify the accuracy and completeness of the attestation. As a result, this bolsters the integrity of the entire process and instills greater confidence.
4. Submit Attestation
Following the review and assessment, users must submit their attestation via the SWIFT KYC Security Attestation (KYC-SA) application by December 31 each year. Consequently, this submission demonstrates the user’s compliance with the CSCF. Timely submission is vital to avoid potential penalties and to ensure that the organization remains in good standing with SWIFT.
5. View Counterparty Attestations
After completing their own attestation, users gain access to the KYC-SA application, where they can subsequently view the attestation status of their counterparties. Therefore, this transparency enables organizations to assess the security posture of their business partners. Monitoring counterparties’ compliance supports risk management efforts and fosters a secure and trusted network environment.
6. Regulatory Oversight
In cases of non-compliance or failure to attest, SWIFT notifies domestic regulatory authorities, which may result in regulatory scrutiny. Additionally, SWIFT randomly selects a sample of attestations each year for verification. Therefore, these measures emphasize the importance of maintaining compliance, as they carry significant implications for regulatory and reputational standing.
By strategically following these steps, organizations can ensure a smooth SWIFT attestation process, thereby reinforcing their cybersecurity posture and aligning with industry standards.
The SWIFT Customer Security Controls Framework (CSCF)

The SWIFT Customer Security Controls Framework (CSCF) is a comprehensive set of security controls designed to enhance the cybersecurity posture of financial institutions using the SWIFT messaging system. Established as part of the SWIFT Customer Security Programme (CSP), the CSCF outlines mandatory and advisory security measures that users must implement to protect their local environments and the broader SWIFT community.
Overview of Mandatory Security Controls
The swift cscf consists of 32 security controls, which include 25 mandatory controls and 7 advisory controls. These controls are structured around three key objectives:
1. Secure Your Environment:
This involves measures to restrict internet access, protect critical systems from the general IT environment, and reduce vulnerabilities.
2. Know and Limit Access:
This objective focuses on managing identities, controlling access privileges, and preventing credential compromise.
3. Detect and Respond:
This includes monitoring for anomalous activities, planning for incident response, and ensuring information sharing in the event of a security incident.
The mandatory controls establish a baseline security standard that all SWIFT users must adhere to, ensuring a unified approach to cybersecurity across the SWIFT network. The advisory controls are recommended practices that can further bolster security but are not mandatory.
Importance in the Financial Messaging System
The CSCF is crucial for several reasons:
- Cybersecurity Resilience:
The financial sector is a prime target for cyberattacks. The CSCF helps institutions improve their defenses against such threats, ensuring the integrity and confidentiality of financial transactions.
- Standardization:
By providing a common set of controls, the CSCF promotes consistency in security practices among all SWIFT users, reducing the risk of vulnerabilities that could be exploited by attackers.
- Regulatory Compliance:
Many financial institutions are subject to regulatory requirements regarding cybersecurity. Adhering to the CSCF helps organizations demonstrate compliance with these regulations, potentially avoiding penalties.
- Collective Security:
The framework fosters collaboration among SWIFT users, creating a collective defense against cyber threats. By ensuring that all members of the SWIFT community implement robust security measures, the overall security of the network is enhanced.
In summary, the SWIFT Customer Security Controls Framework plays a vital role in safeguarding the financial messaging system by establishing mandatory security controls that enhance the cybersecurity resilience of institutions and promote a unified approach to managing cyber risks.
II. The SWIFT Attestation Process
The SWIFT attestation process is crucial for financial institutions worldwide. It ensures compliance with global standards and security measures. However, many find this process complex and challenging. In this section, we'll break down the steps involved. We'll explore how banks navigate the attestation requirements. You'll learn about common pitfalls and best practices. Additionally, we'll discuss recent changes that impact the process. Understanding this system is key for smooth international transactions.
A. Annual SWIFT Attestation Cycle:
The SWIFT attestation process operates on a defined annual cycle, which is critical for ensuring compliance with the SWIFT Customer Security Controls Framework (CSCF).
Timeframe for Attestation
- Re-attestation Period:
All SWIFT users must complete their re-attestation between July and December each year. This timeframe allows institutions to assess their compliance against the latest version of the CSCF, which is updated annually in early July.
- Submission Deadline: Users are required to submit their completed attestation by December 31 of the same year. This deadline ensures that all users confirm their swift csp compliance.
- New Users: Institutions that are new to the SWIFT network must complete their attestation before they can go live, ensuring that they meet security standards from the outset.
Frequency of Attestation
- Annual Requirement:
SWIFT mandates that all users submit a security attestation at least once a year. This annual requirement is designed to maintain a consistent level of security across the SWIFT community and to adapt to evolving cybersecurity threats.
Importance of Timely Attestation
Failure to submit a valid attestation or to comply with the mandatory controls can lead to significant consequences, including being reported to local supervisory authorities and potential restrictions on access to the SWIFT network. Therefore, adhering to the established timelines is crucial for maintaining compliance and security within the financial messaging system.
In summary, the SWIFT attestation cycle is structured to ensure that all users regularly verify their compliance with security controls, thereby enhancing the overall cybersecurity posture of the SWIFT network.
B. Step-by-Step Guide to SWIFT Attestation
The SWIFT attestation process is essential for ensuring compliance with the SWIFT Customer Security Controls Framework (CSCF). Here’s a detailed step-by-step guide to the attestation process:
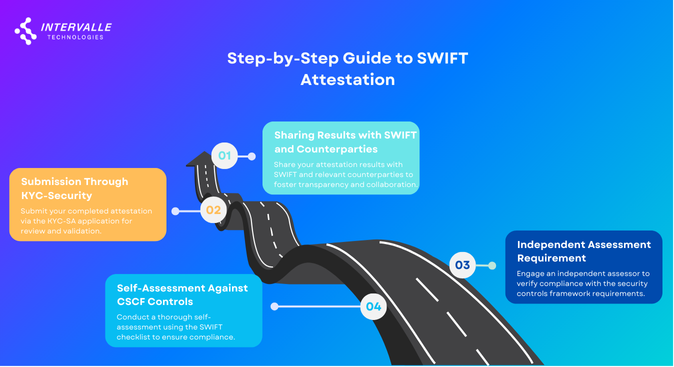
1. Self-Assessment Against CSCF Controls
- Conduct a Self-Assessment:
Financial institutions must perform an annual self-assessment of their local environment against the mandatory controls outlined in the CSCF. This includes evaluating compliance with 25 mandatory controls and 7 advisory controls, focusing on key areas such as securing the environment, managing access, and detecting anomalies.
- Document Findings:
Institutions should document their findings, identifying areas of compliance and any gaps that need to be addressed to meet the required standards.
2. Independent Assessment Requirement
- Engage in Independent Assessment: As part of the attestation process, institutions are required to undergo an independent assessment. This can be conducted either internally (by the second or third line of defense, such as internal audit) or externally (by a qualified third-party assessor) to validate the self-assessment results.
- Select Qualified Assessors: When opting for external assessments, institutions must ensure that the assessors have relevant cybersecurity experience and certifications (e.g., CISA). Internal assessments should be conducted by teams independent of the first line of defense to maintain objectivity.
3. Submission Through KYC-Security Attestation (KYC-SA) Application
- Use the KYC-SA Application: After completing the self-assessment and independent assessment, institutions must submit their attestation results through the KYC-Security Attestation application (KYC-SA) by the annual deadline of December.
- Include Assessment Details: The submission should include details about the independent assessment, such as the name of the assessing organization and the qualifications of the assessors, to ensure transparency and accountability.
4. Sharing Results with SWIFT and Counterparties
- Share Attestation Results: Once the attestation is submitted, the results are shared with SWIFT and can be accessed by other SWIFT users. This promotes a culture of transparency and enables institutions to benchmark their security controls against peers.
- Address Non-Compliance: Institutions that fail to submit a valid attestation or do not complete the independent assessment are considered non-compliant, which may lead to penalties or restrictions from SWIFT.
By following these steps, financial institutions can effectively navigate the SWIFT attestation process, ensuring compliance with the CSCF and enhancing their overall cybersecurity posture.
Independent Assessment: A Critical Component
Types of Independent Assessments for SWIFT Attestation
SWIFT mandates that all users undergo an independent assessment to validate their compliance with the Customer Security Controls Framework (CSCF). There are two primary types of independent assessments: internal assessments and external assessments.
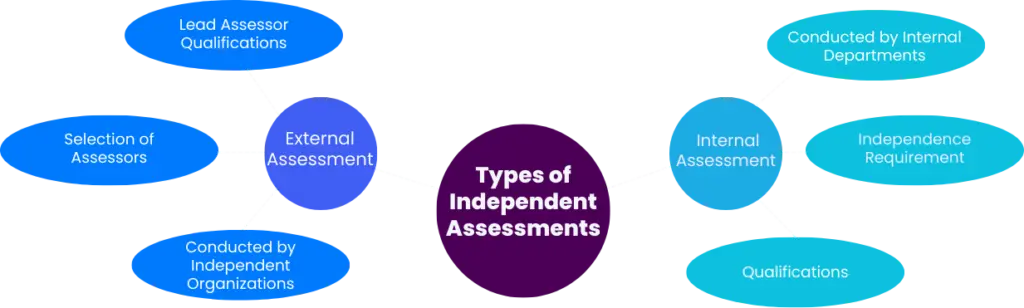
1. Internal Assessment
- Conducted by Internal Departments: An internal assessment is performed by a user’s own independent department, such as compliance, risk management, or internal audit. This department must be separate from the first line of defense (typically the office of the Chief Information Security Officer, CISO).
- Independence Requirement: The assessment team must operate independently to ensure objectivity. This means that those involved in the assessment should not have any reporting lines or conflicts of interest with the control owners being assessed.
- Qualifications: The lead assessor must possess relevant cybersecurity assessment experience and hold at least one recognized professional certification, such as CISA. Other team members should also have appropriate certifications to ensure a competent evaluation.
- Mixed Assessment Option: Institutions can opt for a mixed assessment approach, where both internal and external assessors are utilized. This can provide a broader perspective and leverage the strengths of both assessment types.
2. External Assessment
- Conducted by Independent Organizations: An external assessment is performed by an independent third-party organization that specializes in cybersecurity assessments. This option is often chosen to provide an unbiased evaluation of compliance.
- Selection of Assessors: When selecting an external assessor, institutions must ensure that the chosen organization has relevant experience in cybersecurity assessments and adheres to industry standards, such as PCI DSS.
- Lead Assessor Qualifications: Similar to internal assessments, the lead assessor in an external assessment must hold a relevant professional certification and have recent experience in assessing cybersecurity controls.
- SWIFT-Mandated External Assessments: In certain cases, SWIFT may require specific institutions to undergo external assessments to verify the accuracy of their KYC-Security Attestation (KYC-SA) submissions. Non-compliance with this requirement can lead to reporting to supervisory authorities.
Both internal and external assessments play a crucial role in the SWIFT attestation process. They help ensure that financial institutions maintain robust cybersecurity practices and comply with the mandatory controls set forth in the CSCF. By adhering to these assessment requirements, institutions can enhance their security posture and contribute to the overall security of the SWIFT network.
Requirements for Assessors in SWIFT Attestation
When selecting independent assessors for the SWIFT attestation process, it is crucial to ensure that they meet specific requirements to guarantee the quality and reliability of the assessment. The key requirements for assessors include:
1. Cybersecurity Assessment Experience
- Relevant Experience: Assessors must possess recent and relevant experience in conducting SWIFT audits. This experience should include familiarity with industry-standard frameworks such as PCI DSS, ISO 27001, SOC 2 Type 2, and NIST Cybersecurity Framework (NIST CSF).
- Operational Assessment Skills: The assessors should be capable of executing operational assessments that align with the requirements of the SWIFT Customer Security Controls Framework (CSCF). This ensures that they can effectively evaluate compliance with the mandatory controls.
2. Professional Certifications
- Industry-Recognized Certifications: Assessors should hold relevant professional certifications that demonstrate their expertise in cybersecurity. Key certifications include:
- Certified Information Systems Auditor (CISA)
- Certified Information Systems Security Professional (CISSP)
- PCI Qualified Security Assessor (QSA)
These certifications help ensure that assessors have the necessary knowledge and skills to conduct thorough and effective assessments.
- Supporting Team Certifications: In addition to the lead assessor, supporting team members should also possess relevant certifications to provide comprehensive coverage during the assessment process.
3. Independence from the 1st Line of Defense
- Conflict of Interest: Assessors must demonstrate independence from the first line of defense, which typically includes the operational teams responsible for implementing security controls. This independence is essential to ensure that the assessment is conducted objectively and without bias.
- No Self-Assessment: Assessors should not be involved in assessing their own activities or services, even if conducted through independent individuals within the same organization. This requirement helps maintain the integrity of the assessment process [3].
Selecting qualified independent assessors who meet these requirements is vital for the SWIFT attestation process. By ensuring that assessors have the necessary experience, certifications, and independence, financial institutions can enhance the reliability of their compliance evaluations and contribute to the overall security of the SWIFT network.
IV. Compliance and Penalties
Compliance with SWIFT regulations is vital in the financial industry. Banks and financial institutions are required to adhere to stringent guidelines, with significant consequences for non-compliance. This section examines the penalties associated with violating SWIFT rules, exploring various types of sanctions and their effects. It's crucial for all SWIFT users to be aware of these risks.
Achieving Compliance
Achieving compliance with the SWIFT Customer Security Controls Framework (CSCF) involves meeting all mandatory controls and ensuring the timely submission of a valid attestation. Here’s a breakdown of the key components involved in this process.
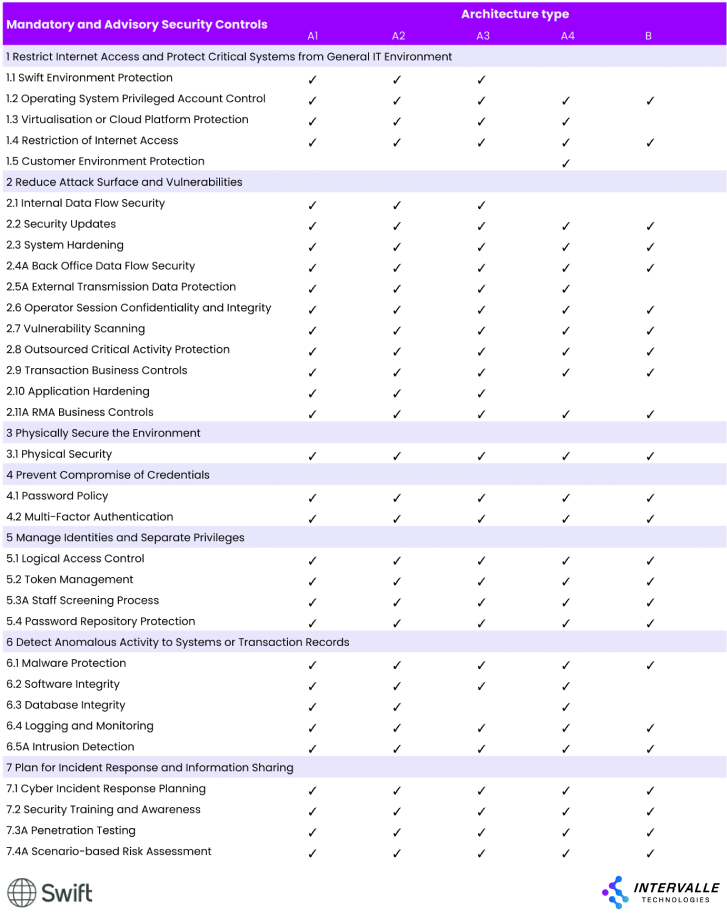
Meeting All CSCF Mandatory Controls
- Understanding the Controls: Financial institutions must familiarize themselves with the 25 mandatory and 7 advisory controls outlined in the CSCF. These controls are designed to establish a robust security baseline and are categorized into three main objectives: securing the environment, managing access, and detecting and responding to threats.
- Implementation: Institutions must implement the mandatory controls within their local SWIFT infrastructure. This includes conducting a gap analysis to identify areas needing improvement and developing a plan to address these gaps effectively. Continuous monitoring and regular reviews of the implemented controls are essential to ensure they remain effective against evolving threats.
- Documentation: Organizations should document their compliance status, noting any deviations from the mandatory controls and the steps taken to rectify them. This documentation is crucial for the attestation process and for demonstrating compliance to SWIFT and relevant authorities.
Timely Submission of Valid Attestation
- Annual Attestation Requirement: All SWIFT users are required to complete an annual security attestation, which involves a self-assessment against the mandatory controls. This attestation must be submitted through the KYC-Security Attestation (KYC-SA) application by the deadline of December 31 each year.
- Independent Assessment: As part of the attestation process, institutions must also conduct an independent assessment to validate their compliance. This can be done internally or through a qualified external assessor, ensuring that the attestation results are accurate and reliable.
- Consequences of Non-Compliance: Institutions that fail to submit a valid attestation or do not meet the mandatory controls may face penalties, including being reported to local regulatory authorities. This emphasizes the importance of adhering to the established timelines and maintaining compliance with the CSCF.
In summary, achieving compliance with the SWIFT CSCF requires a thorough understanding and implementation of mandatory controls, along with the timely submission of a valid attestation. By following these steps, financial institutions can enhance their cybersecurity posture and contribute to the overall security of the SWIFT network.
Consequences of Non-Compliance with SWIFT Attestation
Non-compliance with the SWIFT Customer Security Controls Framework (CSCF) can have significant implications for financial institutions. Understanding the definition of non-compliance and the potential penalties is crucial for maintaining security and operational integrity within the SWIFT network.
Definition of Non-Compliance
Non-compliance refers to the failure of a financial institution to adhere to the mandatory controls set forth in the CSCF. This can occur in several ways, including:
Failure to submit a valid attestation: Institutions that do not submit their annual security attestation by the deadline or submit an expired attestation are considered non-compliant.
Non-fulfillment of mandatory controls: Institutions that do not implement or maintain the required security controls outlined in the CSCF are deemed non-compliant.
Connection through a non-compliant service provider: If a financial institution relies on a service provider that does not meet SWIFT's compliance standards, it can also be classified as non-compliant.
Inadequate independent assessment: Failing to complete a SWIFT-mandated independent assessment further contributes to non-compliance status.
Potential Penalties and Restrictions
The consequences of non-compliance can be severe and may include:
- Increased Risk of Cyber Attacks: Non-compliant institutions are more vulnerable to cyber threats, which can lead to data breaches, financial losses, and operational disruptions.
- Reputational Damage: Non-compliance can harm an institution's reputation within the financial community. Other organizations may be hesitant to engage in transactions with a non-compliant entity, leading to a loss of trust and business opportunities.
- Restricted Access to the SWIFT Network: SWIFT may impose restrictions on a non-compliant institution's access to the network, which can hinder its ability to conduct international transactions and communicate securely with other financial entities.
- Financial Penalties: Regulatory bodies or SWIFT itself may impose financial penalties on institutions that fail to comply with the CSCF. Such penalties can be substantial and negatively impact the institution's financial health.
- Reporting to Local Authorities: SWIFT and regulatory bodies may report non-compliant institutions to local authorities, which can lead to further investigations, audits, and potential legal repercussions, resulting in additional operational costs and fines.
In summary, non-compliance with SWIFT attestation requirements can lead to a range of serious consequences, including increased cyber risk, reputational harm, restricted access to critical financial networks, financial penalties, and regulatory scrutiny. Institutions must prioritize compliance to safeguard their operations and maintain trust within the financial ecosystem.
V. Best Practices for Successful SWIFT Attestation
SWIFT attestation is crucial for financial institutions worldwide. It ensures compliance with global standards and protects against cyber threats. This process can be complex and time-consuming. However, following best practices can streamline the attestation process. Proper preparation and execution are key to success. Failing to meet SWIFT requirements may result in serious consequences. These can include fines, reputational damage, or even loss of SWIFT access. Understanding and implementing best practices is essential for avoiding penalties and maintaining smooth operations.
A. Preparing for the Attestation
To ensure a smooth and successful SWIFT attestation process, financial institutions should follow these key steps:
Conduct Regular Internal Audits
- Perform frequent internal audits: Conduct regular internal audits to assess compliance with the SWIFT Customer Security Controls Framework (CSCF). This helps identify gaps and areas for improvement well before the attestation deadline.
- Document audit findings: Thoroughly document the findings from internal audits, including any deviations from the mandatory controls. This documentation will be crucial during the independent assessment and attestation process.
- Address identified gaps: Develop and execute remediation plans to address any gaps or non-compliant areas identified during the internal audits. Ensure that all mandatory controls are fully implemented and functioning effectively.
Stay Updated with CSCF Changes
- Monitor for CSCF updates: Regularly check for updates to the CSCF, as SWIFT may introduce changes to the mandatory controls or the attestation process. The latest version of the CSCF is typically released in early July each year.
- Communicate changes internally: Ensure that all relevant stakeholders, including IT, security, and compliance teams, are informed about any updates to the CSCF. This helps maintain awareness and facilitates timely implementation of changes.
- Adjust compliance plans: If SWIFT introduces significant changes to the CSCF, review and adjust the institution's compliance plans accordingly. This may involve revising remediation strategies, updating documentation, or conducting additional internal audits.
Engage with Independent Assessors
- Identify qualified assessors: If opting for an external independent assessment, start the process early to identify and engage with qualified cybersecurity assessors. Ensure that the selected assessors meet SWIFT's requirements for experience and certifications.
- Provide necessary information: Work closely with the independent assessors to provide all necessary information, documentation, and access required for a thorough assessment. This includes details about the institution's SWIFT infrastructure, security controls, and compliance efforts.
By following these best practices, financial institutions can proactively prepare for the SWIFT attestation, minimize the risk of non-compliance, and maintain a strong cybersecurity posture within the SWIFT network.
Implementing Robust Security Measures for SWIFT Attestation
To successfully navigate the SWIFT attestation process and ensure compliance with the Customer Security Controls Framework (CSCF), financial institutions must focus on implementing robust security measures. Here are key areas to concentrate on, along with continuous improvement strategies.
Key Areas to Focus On
1. Restrict Internet Access and Protect Critical Systems
- Segregation of Environments: Ensure that the SWIFT environment is isolated from general IT environments to minimize exposure to external threats.
- Access Controls: Implement strict access controls to limit who can access the SWIFT systems and data. This includes using firewalls and intrusion detection systems.
2. Reduce Attack Surface and Vulnerabilities
- Regular Security Updates: Ensure that all systems are regularly updated with the latest security patches and updates to mitigate vulnerabilities.
- System Hardening: Apply hardening techniques to reduce potential attack vectors, such as disabling unnecessary services and using secure configurations.
3. Manage Identities and Access Privileges
- Multi-Factor Authentication (MFA): Implement MFA to enhance security for user access to SWIFT systems, thereby reducing the risk of credential compromise.
- Role-Based Access Control (RBAC): Use RBAC to ensure that users have the minimum necessary access to perform their job functions.
4. Detect Anomalous Activity
- Monitoring and Logging: Establish comprehensive logging and monitoring of all activities within the SWIFT environment to detect any suspicious behavior or anomalies.
- Incident Response Planning: Develop and regularly update an incident response plan to ensure quick action can be taken in the event of a security breach.
5. Physical Security Measures
- Secure Facilities: Ensure that physical access to critical systems is restricted to authorized personnel only, using access controls and surveillance.
Continuous Improvement Strategies
1. Regular Internal Audits
- Conduct frequent internal audits to assess compliance with the CSCF and identify areas for improvement. This proactive approach helps to address issues before the annual attestation.
2. Training and Awareness Programs
- Implement ongoing training programs for employees to raise awareness about cybersecurity threats and best practices. This can help foster a security-conscious culture within the organization.
3. Stay Updated with CSCF Changes
- Regularly review updates to the CSCF and adjust security measures accordingly. SWIFT typically releases updates in early July, providing a roadmap for necessary changes.
4. Engage with Cybersecurity Experts
- Collaborate with cybersecurity service providers to gain insights into emerging threats and best practices. This can enhance the institution's security posture and readiness for the attestation process.
5. Feedback Mechanisms
- Establish feedback mechanisms to learn from past incidents and audits. Continuous feedback helps refine security measures and improve overall compliance efforts.
By focusing on these key areas and implementing continuous improvement strategies, financial institutions can effectively prepare for the SWIFT attestation process, ensuring compliance with the CSCF and enhancing their overall cybersecurity resilience.
Leveraging Technology for Compliance in SWIFT Attestation
To enhance compliance with the SWIFT Customer Security Controls Framework (CSCF), financial institutions can leverage various technologies and tools. This includes utilizing software for security control management and automating parts of the attestation process.
Tools and Software for Security Control Management
Security Information and Event Management (SIEM)
SIEM tools aggregate and analyze security data from across the organization’s IT infrastructure. They provide real-time monitoring, alerting, and reporting, which are essential for identifying security incidents and ensuring compliance with regulatory requirements.
Access Control Systems
These tools manage user permissions and access rights, ensuring that only authorized personnel can access sensitive systems and data. Effective access control helps mitigate insider threats and complies with security standards.
Endpoint Detection and Response (EDR)
EDR solutions monitor endpoint devices for suspicious activities and provide capabilities for threat detection, investigation, and response. They are crucial for maintaining the security of devices connected to the SWIFT network.
Vulnerability Management Tools
These tools continuously scan the organization’s systems for vulnerabilities and provide recommendations for remediation. Regular vulnerability assessments help ensure compliance with the mandatory controls of the CSCF.
Web Application and API Protection (WAAP)
WAAP tools protect web applications and APIs from threats such as SQL injection and cross-site scripting. They help maintain the integrity and security of applications that interact with the SWIFT network.
Automation in the Attestation Process
Automated Compliance Monitoring
Implementing automated compliance monitoring tools can help organizations continuously assess their adherence to the CSCF. These tools can provide alerts for non-compliance issues and track remediation efforts in real-time.
Streamlined Documentation and Reporting
Automation can facilitate the documentation process by generating reports that summarize compliance status and audit findings. This reduces manual effort and ensures that all relevant data is captured accurately for the attestation.
Integration with Existing Security Tools
Many security tools can be integrated to create a cohesive security posture. For instance, SIEM tools can pull data from firewalls, EDR, and vulnerability management systems to provide a comprehensive view of compliance status.
Workflow Automation for Attestation Tasks
Automating routine tasks associated with the attestation process, such as scheduling audits, notifying stakeholders, and tracking deadlines, can improve efficiency and reduce the risk of human error.
Continuous Security Monitoring (CSM)
CSM tools provide ongoing oversight of the security environment, enabling organizations to detect and respond to threats in real-time. This proactive approach helps maintain compliance by ensuring that security controls are functioning effectively.
By leveraging technology through effective security control management tools and automating aspects of the attestation process, financial institutions can enhance their compliance with the SWIFT CSCF. This not only streamlines the attestation process but also strengthens the overall security posture, ensuring that organizations are better equipped to handle evolving cyber threats.
VI. SWIFT Attestation: Beyond Compliance
SWIFT attestation is a crucial process for financial institutions. It goes beyond mere compliance with regulations. Many banks underestimate its importance and potential consequences. Failing to meet SWIFT standards can lead to serious penalties. These may include fines, reputational damage, or even loss of SWIFT access. Understanding the full scope of attestation is vital. This introduction explores why SWIFT attestation matters and what's at stake. We'll uncover the risks and benefits of this essential practice.
Enhancing Overall Cybersecurity Posture Beyond SWIFT Compliance
While compliance with the SWIFT Customer Security Controls Framework (CSCF) is essential for financial institutions, it is crucial to recognize that cybersecurity is a multifaceted challenge that extends beyond SWIFT-specific requirements. By adopting a holistic approach and integrating CSCF compliance with broader security initiatives, organizations can significantly enhance their overall cybersecurity posture and reap additional benefits.
Aligning with Industry Standards and Frameworks
Compliance with CSCF should be viewed as a starting point for a more comprehensive cybersecurity strategy. By aligning CSCF implementation with other industry standards and frameworks, such as NIST CSF, ISO 27001, or PCI DSS, financial institutions can create a robust and cohesive security architecture. This alignment ensures that security controls are not implemented in silos but rather as part of a well-coordinated and layered defense system.
Enhancing Risk Management Capabilities
CSCF compliance focuses on specific security controls, but organizations should also prioritize developing robust risk management capabilities. This includes conducting regular risk assessments, identifying and prioritizing risks, and implementing appropriate mitigation strategies. By integrating CSCF compliance with enterprise-wide risk management practices, financial institutions can make more informed decisions about resource allocation and ensure that security investments align with overall business objectives.
Fostering a Culture of Security Awareness
Cybersecurity is not solely an IT issue; it requires the active participation and awareness of all employees. By integrating CSCF compliance with ongoing security awareness training and communication initiatives, organizations can create a culture where everyone understands their role in maintaining a secure environment. This includes educating employees on topics such as phishing, social engineering, and secure data handling practices.
Leveraging Threat Intelligence and Information Sharing
CSCF compliance encourages financial institutions to share threat information with SWIFT and other counterparties. However, organizations should also actively engage in broader threat intelligence sharing initiatives within the financial sector and beyond. By collaborating with industry peers, security vendors, and law enforcement agencies, financial institutions can gain a more comprehensive understanding of emerging threats and proactively defend against them.
Continuous Monitoring and Improvement
CSCF compliance is an ongoing process that requires continuous monitoring and improvement. By integrating CSCF compliance with continuous monitoring and improvement initiatives, financial institutions can identify and address security gaps in a timely manner, adapt to evolving threats, and ensure that security controls remain effective over time. This includes implementing security information and event management (SIEM) solutions, conducting regular security assessments, and continuously updating security policies and procedures.
Compliance with the SWIFT CSCF is a critical component of a comprehensive cybersecurity strategy for financial institutions. However, by aligning CSCF compliance with broader security initiatives, organizations can significantly enhance their overall cybersecurity posture, reduce risk, and better protect against the evolving threat landscape. By fostering a culture of security awareness, leveraging threat intelligence, and continuously monitoring and improving security measures, financial institutions can create a more resilient and secure operating environment that supports long-term growth and success.
Building Trust in the Financial Ecosystem
Building trust in the financial ecosystem is essential for fostering collaboration and ensuring the stability of the global financial network. Here are key aspects of how transparency with counterparties and strengthening the financial network contribute to this trust.
Transparency with Counterparties
- Open Communication: Transparency involves clear and open communication between financial institutions and their counterparties. This includes sharing relevant information regarding security practices, compliance status, and any incidents that may impact trust.
- Trust-Building Measures: Implementing trust-building measures, such as regular updates on compliance with the SWIFT Customer Security Controls Framework (CSCF), can enhance confidence among counterparties. For example, sharing audit results and security assessments can demonstrate an institution's commitment to maintaining high security standards.
- Collaboration and Information Sharing: Encouraging collaboration and information sharing among financial institutions can help address common cybersecurity challenges. By working together, organizations can share best practices, threat intelligence, and lessons learned from incidents, ultimately strengthening the entire ecosystem's resilience against cyber threats.
Strengthening the Global Financial Network
- Commitment to Compliance: Compliance with frameworks like the SWIFT CSCF is crucial for maintaining the integrity of the global financial network. Institutions that adhere to these standards demonstrate their dedication to security and risk management, which fosters trust among their peers.
- Enhanced Security Posture: By implementing robust security measures and continuously improving cybersecurity practices, financial institutions can reduce the risk of breaches and fraud. This not only protects their own operations but also safeguards the interests of their counterparties, reinforcing trust in the network.
- Building a Resilient Ecosystem: A strong financial ecosystem relies on the collective efforts of its participants. By prioritizing transparency, compliance, and collaboration, institutions can contribute to a more resilient financial network that can withstand challenges and adapt to changing threats.
- Positive Impact on Reputation: Institutions that actively promote transparency and compliance are likely to enhance their reputation within the financial community. A strong reputation for security and reliability can lead to increased business opportunities and stronger relationships with clients and counterparties.
Building trust in the financial ecosystem is a multifaceted endeavor that requires a commitment to transparency, compliance, and collaboration. By fostering open communication with counterparties and strengthening the global financial network through adherence to security frameworks like the SWIFT CSCF, financial institutions can enhance their overall cybersecurity posture and contribute to a more secure and efficient financial system. This trust is vital for facilitating smooth transactions and ensuring the long-term stability of the financial ecosystem.
VII. Future Trends in SWIFT Attestation
As the financial landscape evolves, SWIFT attestation faces new challenges. With constant changes in technology and regulation, understanding these trends is crucial. We'll explore what lies ahead for SWIFT attestation. How will it adapt to emerging demands? These insights will help you prepare for what’s coming. Stay with us as we discuss the future of SWIFT attestation. The upcoming trends might surprise you.
Emerging Threats and Challenges
The cybersecurity landscape is rapidly changing, with several emerging threats and challenges that organizations must address:
- Ransomware Evolution: Ransomware attacks continue to pose a significant threat, with attackers increasingly employing more sophisticated tactics. For instance, Dutch bank ABN AMRO recently disclosed a data breach following a ransomware attack on its third-party service provider, AddComm. These malware families are becoming more complex and often collaborate with other threat actors through underground forums, making detection and prevention increasingly challenging.
- Social Engineering and Phishing: Social engineering tactics are becoming more sophisticated, targeting individuals to compromise devices or sensitive information. Modern phishing attacks are adept at bypassing traditional security measures, using personalized tactics to deceive users.
- Supply Chain Vulnerabilities: Supply chain attacks have emerged as a prominent threat vector, where malicious actors exploit vulnerabilities within third-party vendors to infiltrate target networks. Organizations are placing greater emphasis on supply chain risk management to mitigate these risks.
- Artificial Intelligence Threats: The rise of artificial intelligence (AI) presents both opportunities and challenges. While AI can enhance cybersecurity defenses, it can also be exploited by cybercriminals to automate attacks and develop sophisticated phishing schemes. The development of malicious large language models (LLMs) is a particular concern, as these can generate convincing text for misinformation or cyberattacks.
- IoT Security Challenges: The rapid growth of Internet of Things (IoT) devices presents new vulnerabilities. With an estimated 30 billion IoT devices expected by 2025, securing these devices is critical to prevent potential data breaches and privacy infringements
Anticipated Changes in the CSCF
According to our certified GRC SWIFT CSP consultants and cybersecurity experts, several changes are anticipated in the SWIFT Customer Security Controls Framework (CSCF) in the coming years. These changes are primarily driven by the rapid evolution of threats and the emerging challenges they present:
- Updated Mandatory Controls: The CSCF may introduce new mandatory controls to address emerging threats, particularly those related to ransomware, supply chain vulnerabilities, and AI-driven attacks. This ensures that financial institutions remain resilient against evolving cyber threats.
- Focus on Continuous Monitoring: The CSCF is likely to emphasize the importance of continuous monitoring and real-time threat intelligence sharing among SWIFT users. This proactive approach will help organizations stay ahead of potential threats and adapt their security measures accordingly.
- Integration of Advanced Technologies: Future iterations of the CSCF may encourage the integration of advanced technologies, such as AI and machine learning, into compliance frameworks. These technologies can enhance threat detection capabilities and improve the overall security posture of financial institutions.
- Emphasis on Supply Chain Security: Given the rise in supply chain attacks, the CSCF may place greater emphasis on assessing and managing risks associated with third-party vendors and service providers. This will help institutions secure their entire ecosystem, not just their internal operations.
In summary, the evolving cybersecurity landscape presents significant challenges that necessitate proactive measures and adaptations in frameworks like the CSCF. By anticipating these changes and enhancing their security strategies, financial institutions can better protect themselves against emerging threats and contribute to a more secure financial ecosystem.
VIII. Conclusion: Mastering SWIFT Attestation
A. Recap of Key Points
1. SWIFT Attestation: An annual compliance process for financial institutions to verify adherence to the SWIFT Customer Security Controls Framework (CSCF), which includes mandatory security controls designed to enhance cybersecurity.
2. Evolving Cybersecurity Landscape: Financial institutions face emerging threats such as sophisticated ransomware attacks, social engineering, supply chain vulnerabilities, and the exploitation of AI technologies. The CSCF is expected to adapt to these threats with updated controls and a focus on continuous monitoring.
3. Technological Advancements: AI and machine learning can enhance threat detection and automate compliance processes, while blockchain technology offers potential for improved security and transparency in financial transactions.
4. Building Trust: Transparency with counterparties and a commitment to compliance strengthen the global financial network, fostering trust among participants and enhancing overall security.
5. Consequences of Non-Compliance: Failure to comply with the CSCF can lead to penalties, restricted access to SWIFT services, reputational damage, and increased vulnerability to cyber threats.
B. Action Steps for Financial Institutions
1. Conduct Regular Internal Audits: Schedule frequent internal audits to assess compliance with the CSCF and identify areas for improvement.
2. Implement Robust Security Measures: Focus on key areas such as access control, vulnerability management, and incident response to enhance the overall cybersecurity posture.
3. Stay Informed on Emerging Threats: Regularly review threat intelligence reports and updates on cybersecurity trends to adapt security measures accordingly.
4. Engage in Continuous Training: Provide ongoing training for employees to raise awareness about cybersecurity risks and best practices for maintaining security.
5. Leverage Technology: Utilize advanced technologies such as AI and machine learning for threat detection and automate compliance processes to improve efficiency.
6. Foster Transparency with Counterparties: Share compliance and security information with counterparties to build trust and enhance collaboration in addressing cybersecurity challenges.
7. Prepare for the Attestation Process: Begin preparations early by conducting self-assessments, engaging independent assessors, and ensuring timely submission of attestation results.
C. Resources for Further Information
1. SWIFT Customer Security Controls Framework (CSCF):
2. Cybersecurity Frameworks:
- [NIST Cybersecurity Framework]()
- [ISO/IEC 27001 Information Security Management]
3. Threat Intelligence and Cybersecurity Reports:
- [Verizon Data Breach Investigations Report (DBIR)](https://enterprise.verizon.com/resources/reports/dbir/)
- [CrowdStrike Global Threat Report](https://www.crowdstrike.com/global-threat-report/)
4. Cybersecurity Training Resources:
- [SANS Institute Cybersecurity Training]
By following these action steps and utilizing the provided resources, financial institutions can enhance their cybersecurity posture, ensure compliance with the SWIFT CSCF, and contribute to a more secure financial ecosystem.
