SOC Services: From Threat Detection to Business Protection
Sophisticated SOC services have evolved from reactive monitoring to proactive threat orchestration.
Picture this: While your competitors scramble to understand what happened after a breach, your organization already neutralized the threat before it could cause damage. The difference? A mature Security Operations Center that doesn't just watch—it anticipates, adapts, and acts with surgical precision.
Cybercriminals no longer operate like lone wolves breaking into digital homes. They've industrialized. They run operations with quarterly targets, customer service desks, and franchise models. Ransomware-as-a-service platforms generate more revenue than many Fortune 500 companies. Against this backdrop of professionalized cybercrime, organizations need equally sophisticated defense mechanisms.
Enter Security Operations Center services—the strategic nerve center that transforms raw security data into actionable intelligence, turning defensive postures into competitive advantages.
The Evolution of SOC Services in Modern Cybersecurity
The concept of centralized security monitoring has transformed dramatically over the past decade. Traditional SOC services initially focused on log aggregation and basic alert generation. However, today's Security Operations Centers have evolved into sophisticated command centers that leverage artificial intelligence, machine learning, and threat intelligence to provide comprehensive cyber defense capabilities.
This evolution reflects the changing threat landscape. In 2024, the average cost of a data breach reached $4.88 million, according to IBM's Cost of a Data Breach Report. More importantly, organizations with fully deployed security AI and automation experienced breach costs that were $2.2 million lower than those without these capabilities. This stark difference underscores why modern SOC services have become essential infrastructure rather than optional security enhancements.
Furthermore, the shift toward remote work and cloud-first architectures has expanded the attack surface exponentially. Traditional network perimeters have dissolved, creating new challenges that require continuous monitoring across endpoints, cloud workloads, and hybrid environments. Consequently, Security Operations Centers must now provide visibility into diverse infrastructure components while maintaining the agility to respond to threats in real-time.
Core Components of Comprehensive SOC Services
24/7 Threat Monitoring and Detection
The foundation of any effective SOC services lies in continuous monitoring capabilities. Modern threat detection goes far beyond simple signature-based approaches, incorporating behavioral analytics, anomaly detection, and threat hunting methodologies.
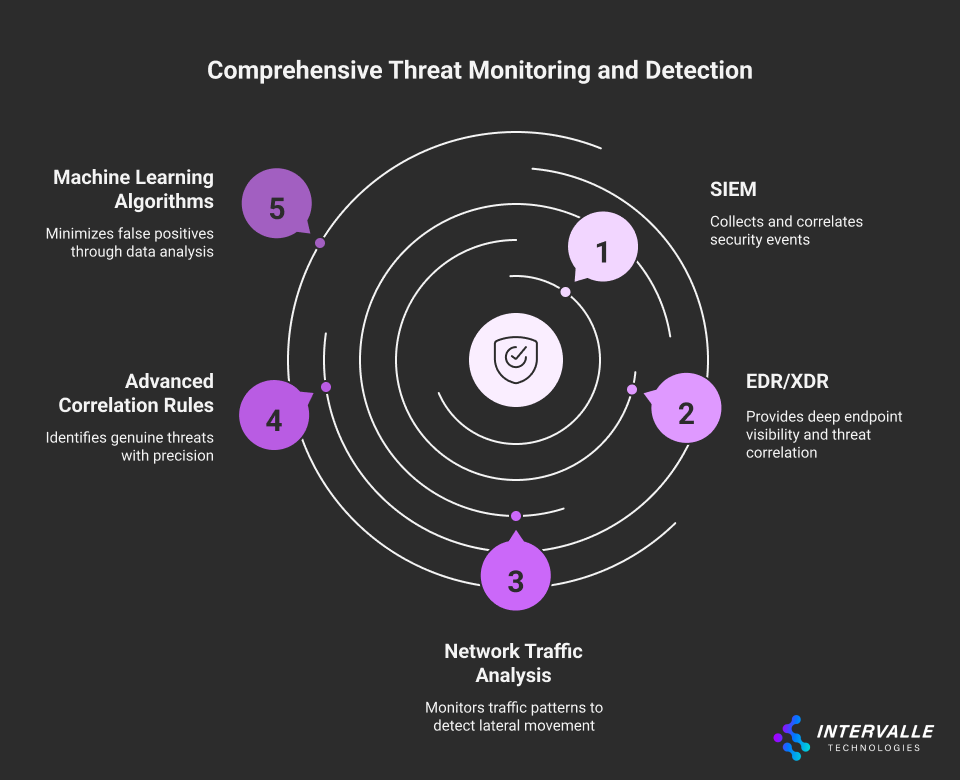
Key Technologies and Capabilities:
- SIEM (Security Information and Event Management): Platforms like Splunk, IBM QRadar, and Microsoft Sentinel collect and correlate security events from across the enterprise infrastructure
- EDR/XDR (Endpoint/Extended Detection and Response): Solutions such as CrowdStrike Falcon and Microsoft Defender XDR provide deep visibility into endpoint activities and cross-platform threat correlation
- Network Traffic Analysis: Tools that monitor east-west and north-south traffic patterns to identify lateral movement and data exfiltration attempts
At Intervalle Technologies, our Security Operations Center processes over 10 billion security events daily, utilizing advanced correlation rules and machine learning algorithms to identify genuine threats while minimizing false positives. This approach ensures that our clients receive actionable intelligence rather than alert fatigue.
SOC Services: Incident Response and Remediation
Effective incident response represents the difference between a contained security event and a catastrophic breach. Professional SOC services provide structured incident response workflows that ensure rapid containment, thorough investigation, and complete remediation.
Typical Incident Response Timeline:
| Phase | Description | Approximate Average Duration (based on studies) |
|---|---|---|
| 1. Preparation | Establishing tools, procedures, training, and response plans. Team readiness. | Ongoing, continuous phase before incidents |
| 2. Identification | Incident detection via SIEM, EDR, alerts, logs. Incident confirmation. | ~3 days on average to discover an incident (USA, 2023) |
| 3. Containment | Limiting the impact and spread (e.g., isolating systems, blocking IPs). | Immediate response; lasts hours to days |
| 4. Eradication | Removing malware, fixing root causes (e.g., patching vulnerabilities). | Several days to weeks depending on complexity |
| 5. Recovery | Restoring systems, validating integrity, returning to normal operations. | Variable, typically days to weeks |
| 6. Lessons Learned | Post-incident review, documentation, process improvement, and training. | Days to weeks after resolution |
Security Orchestration, Automation and Response (SOAR) platforms play a crucial role in accelerating response times. Tools like IBM QRadar SOAR and Palo Alto Cortex XSOAR enable automated playbooks that can execute immediate containment actions while human analysts conduct deeper investigations.
Vulnerability Management Services
Proactive vulnerability management forms a critical component of comprehensive SOC services. This involves continuous asset discovery, vulnerability scanning, risk assessment, and remediation tracking across the enterprise environment.
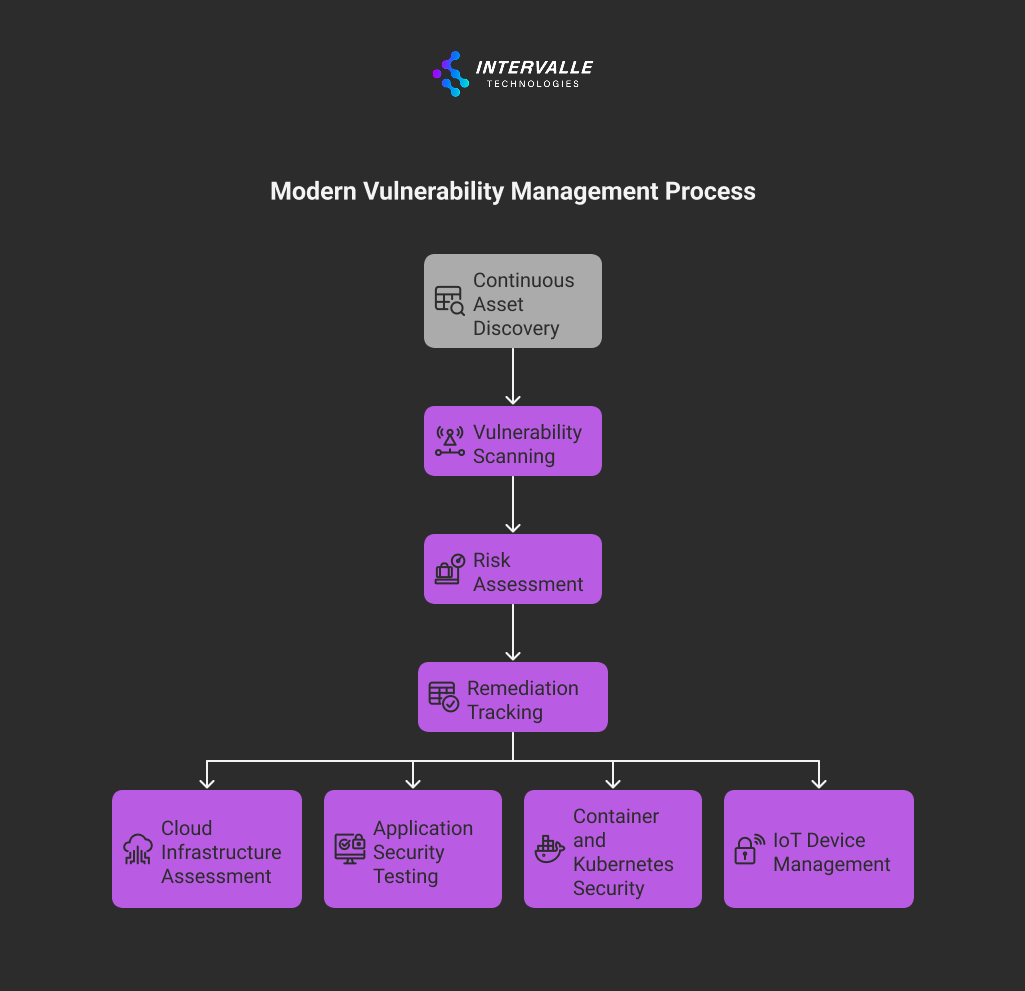
Modern vulnerability management extends beyond traditional network scanning to include:
- Cloud Infrastructure Assessment: Identifying misconfigurations in AWS, Azure, and Google Cloud environments
- Application Security Testing: Both static and dynamic analysis of custom applications
- Container and Kubernetes Security: Scanning container images and orchestration platforms for vulnerabilities
- Internet of Things (IoT) Device Management: Discovering and securing connected devices throughout the organization
Internal vs. Outsourced Security Operations Center Solutions
Organizations face a fundamental decision when implementing SOC capabilities: building internal resources or partnering with a managed security services provider (MSSP). This decision involves multiple considerations beyond simple cost calculations.
Comparison of SOC Service Models:
| SOC Model | Description | Advantages | Drawbacks |
|---|---|---|---|
| Fully Insourced SOC | SOC built and operated entirely in-house by the organization using its own team and infrastructure. | Full control, deep integration, complete customization. | High costs (CAPEX + OPEX), talent recruitment and retention challenges, complex to manage. |
| Fully Outsourced SOC / SOC-as-a-Service | SOC managed by a third-party provider, typically through a cloud platform with remote access. | Lower cost, fast deployment, access to advanced expertise, no hardware investment needed. | Varying quality between providers, potential confidentiality risks, reliance on external vendors. |
| Hybrid SOC | A mix of internal and external teams sharing responsibility for SOC operations. | Greater flexibility, 24/7 coverage, reduced cost vs fully insourced model. | Requires strong coordination, more complex to govern. |
| Virtual SOC (vSOC) | Fully cloud-based SOC operated remotely with no on-premises infrastructure. | High flexibility, reduced infrastructure cost, access to advanced tech. | Less direct control, dependent on connectivity and provider reliability. |
| Command SOC (Dedicated Physical Center) | Physical facility with on-site teams and advanced technologies. | Direct collaboration, centralized management, suited for complex environments. | High cost, heavy infrastructure, less agility. |
However, the decision involves more than financial considerations. Organizations must evaluate their internal capabilities, regulatory requirements, and strategic objectives. For instance, highly regulated industries like financial services or healthcare may require additional compliance oversight that influences the SOC service model selection.
At Intervalle Technologies, we've observed that many organizations benefit from a hybrid approach, maintaining internal security teams for strategic planning and policy development while leveraging our SOC services for 24/7 monitoring and response capabilities. This model provides the best of both worlds: internal control and external expertise.
Advanced SOC Services: Beyond Basic Monitoring
Threat Intelligence and Analytics
Modern SOC services incorporate sophisticated threat intelligence capabilities that go beyond basic indicator consumption. Advanced threat intelligence involves the collection, analysis, and application of actionable intelligence to enhance detection capabilities and inform strategic security decisions.
Threat Intelligence Sources and Applications:
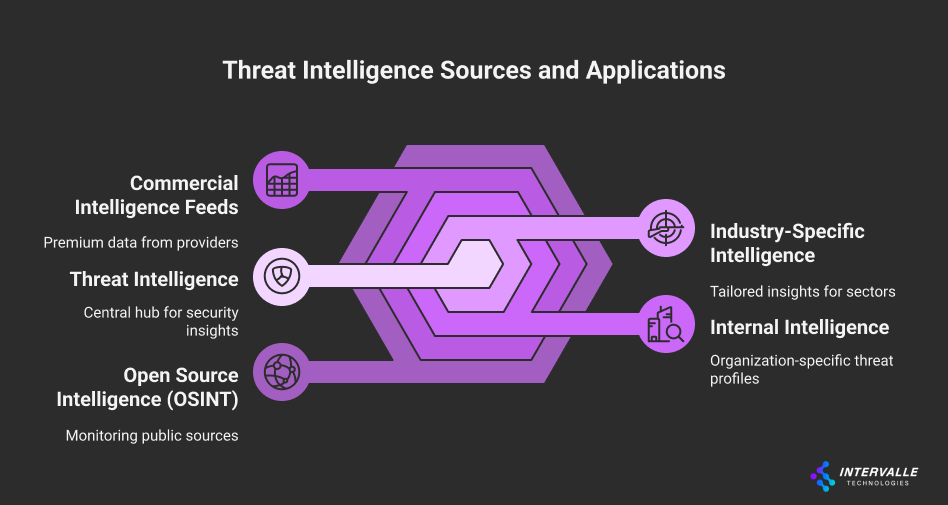
- Open Source Intelligence (OSINT): Monitoring dark web forums, social media, and public breach databases
- Commercial Intelligence Feeds: Integrating premium threat data from providers like Recorded Future and Anomali
- Internal Intelligence: Developing organization-specific threat profiles based on historical incidents
- Industry-Specific Intelligence: Focusing on threats targeting specific sectors or technologies
For example, our threat intelligence team recently identified a new malware family targeting manufacturing companies in the Midwest. By proactively sharing this intelligence with our manufacturing clients and updating our detection rules, we prevented three potential breaches before they could impact operations.
Digital Forensics and Investigation
When incidents occur, thorough forensic analysis becomes essential for understanding the full scope of compromise and preventing future occurrences. Professional SOC services include digital forensics capabilities that can preserve evidence, reconstruct attack timelines, and support legal proceedings if necessary.
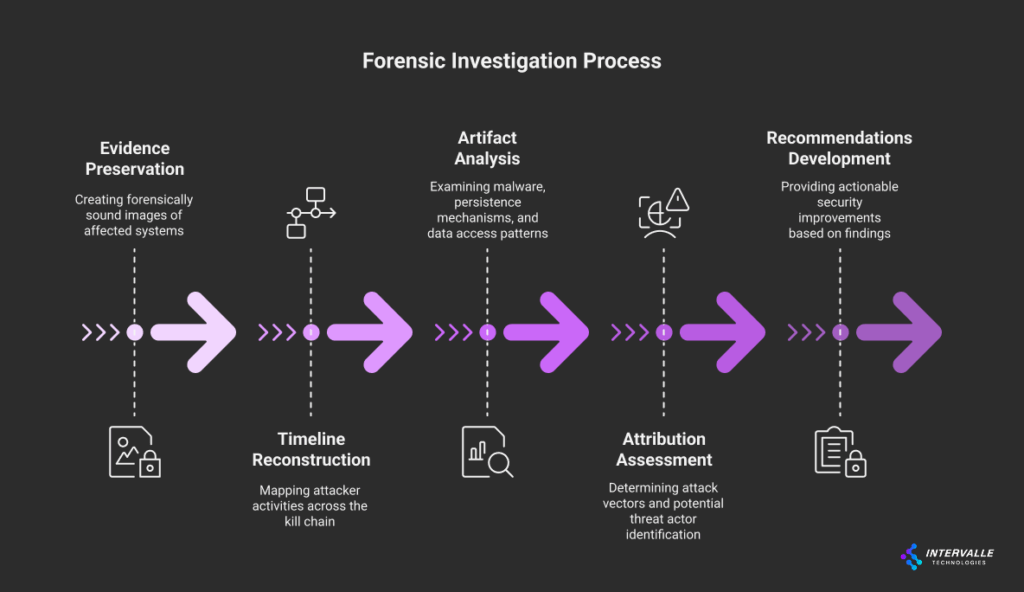
Forensic Investigation Process:
- Evidence Preservation: Creating forensically sound images of affected systems
- Timeline Reconstruction: Mapping attacker activities across the kill chain
- Artifact Analysis: Examining malware, persistence mechanisms, and data access patterns
- Attribution Assessment: Determining attack vectors and potential threat actor identification
- Recommendations Development: Providing actionable security improvements based on findings
Cloud Security Monitoring Solutions
As organizations accelerate cloud adoption, SOC services must extend visibility into multi-cloud environments. This requires specialized tools and expertise to monitor cloud-native services, infrastructure as code, and serverless computing platforms.
Cloud Security Monitoring Capabilities:
- Configuration Drift Detection: Monitoring for unauthorized changes to cloud resources
- Identity and Access Management (IAM) Oversight: Tracking privilege escalations and access anomalies
- Data Loss Prevention (DLP): Monitoring data flows and preventing unauthorized exfiltration
- Compliance Monitoring: Ensuring adherence to frameworks like SOC 2, ISO 27001, and industry-specific regulations
Managed Detection and Response Services: The Evolution of SOC Capabilities
Managed Detection and Response (MDR) services represent the next evolution in SOC capabilities, combining advanced technology with human expertise to deliver proactive, comprehensive cybersecurity operations. Unlike traditional managed security service providers (MSSPs) that focus primarily on monitoring and alerting, MDR services actively engage in threat hunting, investigation, and response activities.
The distinction between conventional SOC services and MDR lies in the depth of engagement and response capabilities. While traditional SOC services might identify and alert on suspicious activities, MDR services take ownership of the entire threat lifecycle—from initial detection through complete remediation.
Core MDR Service Components
Proactive Threat Hunting MDR services go beyond reactive monitoring by actively searching for hidden threats that automated tools might miss. This involves skilled security analysts who understand attacker tactics, techniques, and procedures (TTPs) and can identify subtle indicators of compromise that might otherwise go unnoticed.
Comprehensive Investigation and Analysis When threats are detected, MDR services conduct deep forensic analysis to understand the full scope and impact of security incidents. This includes examining logs, correlating events across multiple data sources, and leveraging threat intelligence to provide context and attribution.
Active Response and Remediation Perhaps most importantly, MDR services take direct action to contain and neutralize threats. This might include isolating compromised endpoints, blocking malicious network traffic, or implementing emergency access controls. Many MDR providers can perform these actions autonomously, significantly reducing response times.
Continuous Improvement and Optimization MDR services include regular security health assessments and recommendations for improving defensive capabilities. This proactive approach helps organizations strengthen their security posture over time rather than simply responding to incidents as they occur.
Technology Integration in MDR Services
Modern MDR services leverage advanced technologies to enhance their capabilities:
- Endpoint Detection and Response (EDR): Providing deep visibility into endpoint activities and enabling rapid response actions
- Extended Detection and Response (XDR): Correlating data across endpoints, networks, cloud environments, and applications for comprehensive threat visibility
- User and Entity Behavior Analytics (UEBA): Identifying anomalous behaviors that might indicate compromise or insider threats
- Threat Intelligence Integration: Incorporating global threat intelligence feeds to enhance detection capabilities and provide context for security events
At Intervalle Technologies, our MDR services combine cutting-edge technology with seasoned security professionals who understand the evolving threat landscape. Our approach focuses on outcomes rather than just outputs—we measure success by prevented breaches, reduced dwell time, and improved security posture rather than simply the number of alerts processed.
Measuring the ROI of Managed Detection and Response Services
Calculating the return on investment for SOC services requires a comprehensive approach that considers both cost avoidance and operational efficiency improvements. Traditional cost-benefit analyses often underestimate the true value of professional security operations.
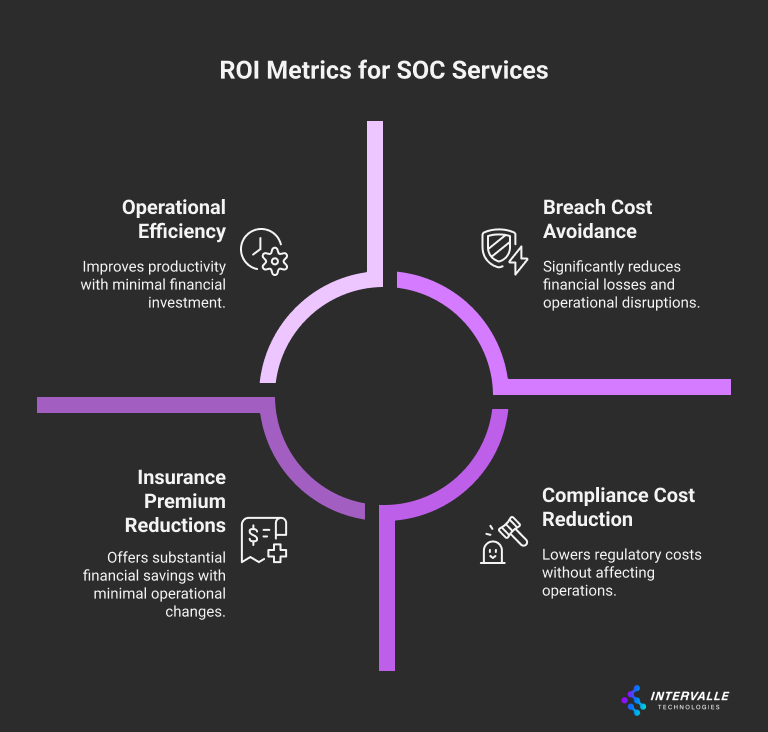
Primary ROI Metrics:
- Breach Cost Avoidance: Based on industry averages and organization-specific risk assessments
- Compliance Cost Reduction: Avoiding regulatory fines and audit remediation costs
- Operational Efficiency: Reducing internal security team workload and improving productivity
- Insurance Premium Reductions: Many insurers offer discounts for comprehensive SOC services
- Business Continuity: Minimizing disruption from security incidents
A recent analysis of our client base revealed that organizations using our SOC services experienced 67% fewer security incidents requiring business disruption compared to industry averages. Additionally, when incidents did occur, our clients averaged 89% faster resolution times, significantly reducing the impact on operations and revenue.
Selecting the Right SOC Services Provider
Choosing a SOC services provider represents a critical decision that will impact an organization's security posture for years to come. The selection process should evaluate multiple factors beyond cost and basic capabilities.
Key Evaluation Criteria:
1. Technical Capabilities
- Breadth and depth of security tool integration
- Threat detection accuracy and false positive rates
- Incident response time commitments and escalation procedures
- Forensics and investigation capabilities
2. Operational Excellence
- Staff certifications and experience levels
- Geographic coverage and time zone considerations
- Escalation procedures and communication protocols
- Reporting and dashboard capabilities
3. Industry Expertise
- Sector-specific threat intelligence and compliance knowledge
- Regulatory framework expertise
- Reference clients in similar industries
- Customization capabilities for unique requirements
4. Partnership Approach
- Commitment to long-term relationship building
- Transparency in operations and pricing
- Flexibility in service customization
- Integration with existing security teams
At Intervalle Technologies, we differentiate ourselves through our consultative approach to SOC services. Rather than offering one-size-fits-all solutions, we work closely with each client to understand their unique risk profile, regulatory requirements, and business objectives. This partnership approach ensures that our SOC services align with strategic business goals while providing comprehensive security coverage.
The Future of Security Operations Center Technologies
The evolution of SOC services continues to accelerate, driven by advances in artificial intelligence, automation, and cloud technologies. Understanding these trends helps organizations make informed decisions about their long-term security strategy.
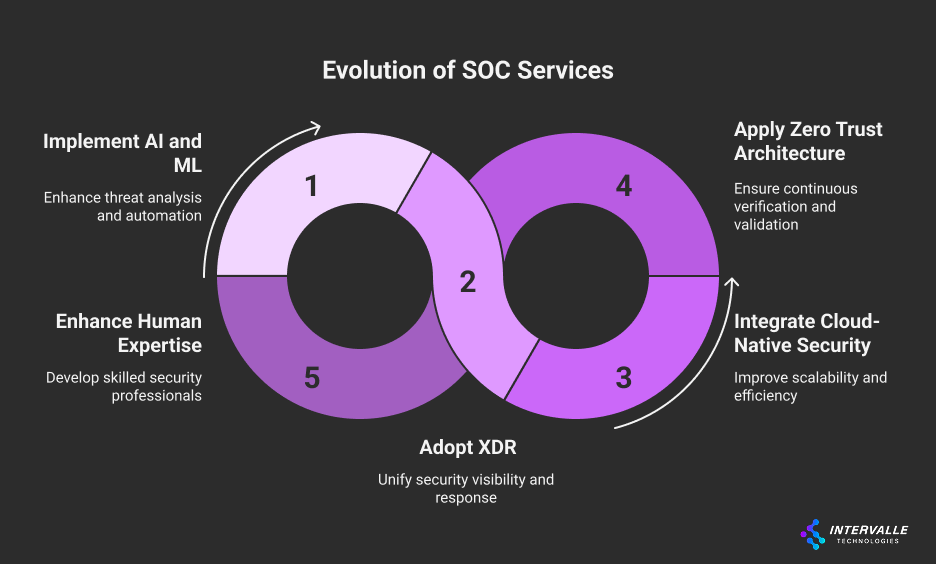
Emerging Technologies and Trends:
Artificial Intelligence and Machine Learning
- Advanced behavioral analytics for user and entity behavior analysis (UEBA)
- Automated threat hunting and investigation workflows
- Predictive analytics for proactive threat identification
- Natural language processing for threat intelligence analysis
Extended Detection and Response (XDR)
- Unified visibility across endpoints, networks, clouds, and applications
- Automated correlation and investigation across multiple security tools
- Simplified management and reduced complexity for security teams
- Enhanced threat context and kill chain reconstruction
Cloud-Native Security Operations
- Serverless SOC architectures for improved scalability and cost efficiency
- Container-based security tool deployment and management
- API-first integration approaches for seamless tool connectivity
- Global threat intelligence sharing and collaboration platforms
Zero Trust Architecture Integration
- Continuous verification and validation of all network communications
- Identity-centric security models that adapt to user behavior
- Micro-segmentation and least-privilege access enforcement
- Real-time risk assessment and adaptive authentication
These technological advances promise to make SOC services more effective, efficient, and accessible to organizations of all sizes. However, the human element remains crucial—skilled security professionals who can interpret complex threat data, make strategic decisions, and communicate effectively with business stakeholders will continue to be essential.
Conclusion
SOC services have shifted from luxury to necessity in today's business environment. The numbers speak clearly: organizations without proper security operations face significantly higher breach costs, longer recovery times, and greater operational disruption. This isn't about fear—it's about pragmatic business planning.
The data we've examined throughout this analysis demonstrates that professional SOC services deliver measurable value. Reduced incident response times, lower breach costs, improved compliance posture, and enhanced operational efficiency all contribute to a compelling business case. However, the real value lies in the expertise and continuous improvement that experienced providers bring to the table.
At Intervalle Technologies, we've built our SOC services around a simple premise: security operations should strengthen your business, not complicate it. Our approach focuses on clear communication, transparent processes, and measurable outcomes. We don't just monitor your systems—we help you understand your risk profile and make informed decisions about security investments.
The cybersecurity market will continue evolving, with new threats emerging alongside new defensive technologies. Organizations that establish strong SOC partnerships today will be better positioned to adapt to future challenges. The question isn't whether you need these services—it's whether you're ready to make the investment in professional security operations that your business strategy demands.
Ready to strengthen your cybersecurity posture with professional SOC services? Contact Intervalle Technologies today to discuss how our Security Operations Center can provide the comprehensive protection your organization needs in today's threat landscape.
