PCI DSS: Everything You Need to Know in 2026

Mastering PCI DSS requires a strategic mindset, not just a compliance checklist. This standard is the global bedrock of modern payment security. However, many organizations view it as a burdensome annual audit.
They consequently miss its true value as a security framework. This limited perspective creates dangerous gaps in their defense posture. Indeed, treating compliance as a mere checkbox exercise is a recipe for a data breach.
This guide reframes the conversation around the Payment Card Industry Data Security Standard (PCI DSS). It moves beyond basic requirements and into strategic implementation. We will explore the technical root causes of compliance failures.
Furthermore, we will provide actionable solutions tailored for security leaders. You will learn how to build a resilient, threat-informed PCI DSS program. Ultimately, this article equips you to transform your compliance obligations into a true competitive advantage.
The Evolving Threat Landscape for Payment Security
The threat landscape targeting payment data is both relentless and sophisticated. Cybercriminals continuously devise new methods to bypass security controls. As a result, organizations face unprecedented risks.
Understanding these threats is the first step toward building a robust defense. A reactive posture is no longer sufficient; therefore, proactive threat intelligence is essential for survival.
The Staggering Financial Cost of Non-Compliance with PCI DSS

Non-compliance with PCI DSS carries severe financial penalties. These extend far beyond regulatory fines. A single data breach can cost millions in investigation and remediation.
For instance, the average cost of a data breach reached $4.45 million in 2023. This figu re does not include reputational damage or customer churn.
Furthermore, acquiring banks can levy their own fines for non-compliance. These penalties can range from $5,000 to $100,000 per month. They continue until the organization achieves compliance.
In severe cases, a business may even lose its ability to process credit card payments altogether. This can be a death sentence for e-commerce and retail companies.
What's more, the legal costs from class-action lawsuits can be astronomical. All in all, the financial argument for maintaining a strong PCI DSS posture is undeniable.
Modern Attack Vectors Threatening PCI DSS Environments
Attackers are constantly refining their tactics to steal cardholder data. Digital skimming, also known as Magecart attacks, remains a primary threat. These attacks inject malicious JavaScript into e-commerce payment pages.
Consequently, they capture credit card details in real time as customers type them. The data is then sent directly to attacker-controlled servers.
In addition, attacks on APIs are growing more common. Many businesses use APIs to connect payment processing systems. If these APIs are not properly secured, they offer a direct pathway into the cardholder data environment (CDE).
Another critical vector involves exploiting vulnerabilities in third-party software. For example, a flaw in a widely used plugin can expose thousands of merchants. Therefore, a comprehensive vulnerability management program is crucial for defending against these modern threats to your PCI DSS framework.
The Insider Threat and Its Impact on Your PCI DSS Scope
The threat is not always external. In fact, insider threats pose a significant risk to payment security. These can be malicious employees seeking financial gain.
They can also be negligent workers who unintentionally expose data. A disgruntled employee with access to the CDE can exfiltrate vast amounts of cardholder data. This can happen with minimal chance of immediate detection.
Similarly, a well-meaning employee might misconfigure a cloud storage bucket. This action could inadvertently expose sensitive payment information to the public internet. This highlights the importance of strong access controls and the principle of least privilege.
Above all, PCI DSS compliance requires strict monitoring of all access to cardholder data. Regular security awareness training is also essential. It helps employees recognize and avoid actions that could compromise your payment security posture.
Technical Root Causes of PCI DSS Failures
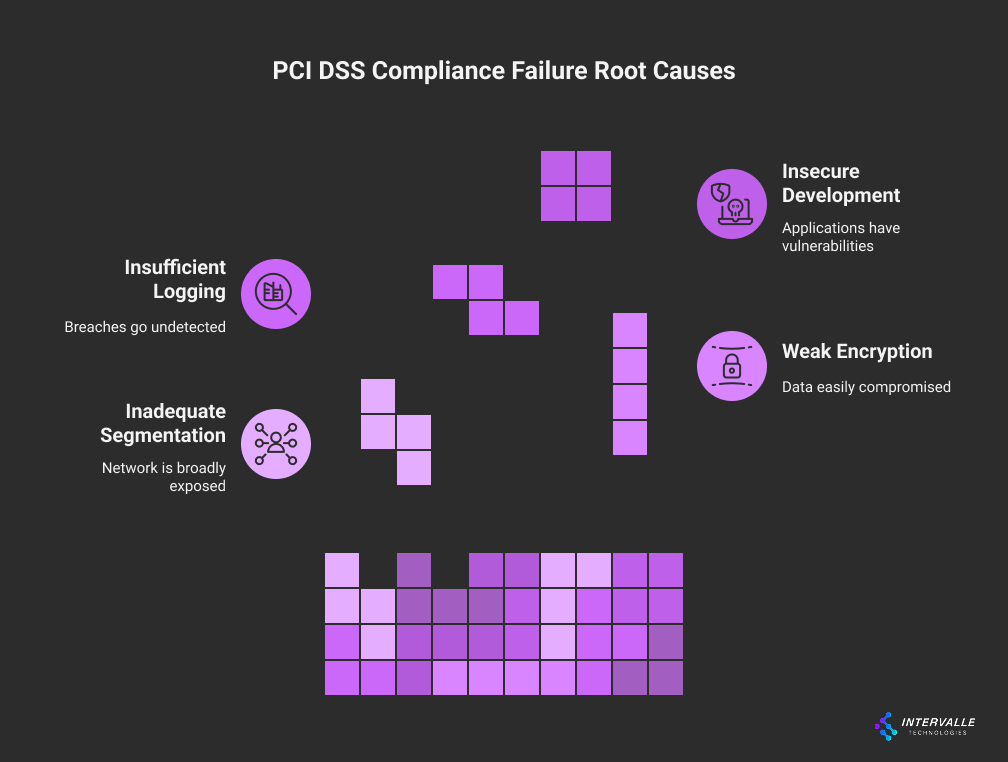
Achieving and maintaining PCI DSS compliance is a complex technical challenge. Failures often stem from deep-seated architectural and procedural flaws. Simply deploying security tools is not enough.
Organizations must address the underlying causes of non-compliance. Otherwise, they remain vulnerable despite passing an annual audit. Let's explore the most common technical root causes.
Inadequate Network Segmentation and Scope Creep in PCI DSS
Poor network segmentation is a primary reason for PCI DSS compliance failures. The cardholder data environment (CDE) must be isolated from the rest of the corporate network. When segmentation is weak or non-existent, the entire network falls into scope.
This dramatically increases the complexity and cost of the audit. Consequently, it expands the attack surface for potential breaches.
Scope creep occurs when systems not essential for payment processing can communicate with the CDE. For example, a marketing server should never have a direct path to a database storing cardholder data. Proper segmentation uses firewalls and access control lists (ACLs) to enforce strict boundaries.
This ensures that only authorized systems can interact with the CDE. Thus, effective segmentation is a foundational control for any successful PCI DSS program. It simplifies compliance and enhances overall security.
Weak Encryption and Key Management Protocols
Encryption is a core requirement of PCI DSS. It protects cardholder data both at rest (stored) and in transit (transmitted over networks). However, many organizations fail in its implementation.
Using outdated encryption algorithms like SSL or early TLS is a common mistake. These protocols contain known vulnerabilities that attackers can exploit. Therefore, strong, modern cryptography such as TLS 1.2 or higher is mandatory.
Equally important is robust cryptographic key management. The keys used to encrypt and decrypt data are as sensitive as the data itself. If an attacker gains access to your encryption keys, your encrypted data is worthless.
Common failures include storing keys on the same server as the data. Another is not rotating keys regularly. A comprehensive key management strategy, detailed in your Payment Card Industry (PCI) Compliance plan, is essential for protecting your most critical assets.
Insufficient Logging and Monitoring: The Silent PCI DSS Killer
You cannot protect what you cannot see. Insufficient logging and monitoring is a silent but deadly threat to PCI DSS compliance. Requirement 10 of the standard mandates tracking and monitoring all access to network resources and cardholder data.
Yet, many organizations collect logs without effectively analyzing them. Logs are often stored without any process for regular review.
As a result, a breach could go undetected for months. Attackers rely on this lack of visibility to move laterally within a network. A robust Security Information and Event Management (SIEM) solution is vital.
It centralizes logs from all in-scope systems. Moreover, it uses correlation rules to detect suspicious activity in real time.
For instance, it can flag multiple failed login attempts from a single IP address. This proactive monitoring is the difference between a minor incident and a catastrophic breach under the PCI DSS framework.
Insecure Software Development and PCI DSS Requirement 6
Vulnerabilities in custom applications are a leading cause of payment data breaches. PCI DSS Requirement 6 specifically addresses the need to develop and maintain secure systems and applications. This means integrating security into the entire software development lifecycle (SDLC).
Unfortunately, many development teams prioritize speed over security. They often release code with known vulnerabilities.
Common issues include SQL injection, cross-site scripting (XSS), and insecure direct object references. These flaws can allow an attacker to bypass authentication and access sensitive data. To comply with PCI DSS, organizations must implement secure coding training for developers.
They also need to perform regular code reviews and use static and dynamic application security testing (SAST/DAST) tools. Building security in from the start is far more effective than trying to patch it in later.
Actionable Solutions for a Robust PCI DSS Framework
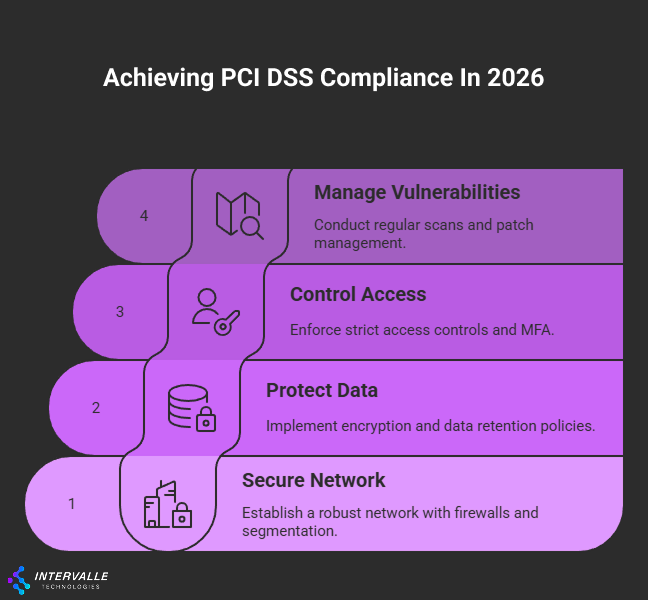
A successful PCI DSS program is built on a foundation of proactive, layered security controls. It is not about a single product or a one-time fix. Instead, it involves creating a sustainable framework of policies, processes, and technologies.
This section provides actionable solutions organized by the core pillars of the PCI DSS. Security leaders can use these to build a defensible and compliant environment.
Building and Maintaining a Secure Network for PCI DSS
A secure network is the first line of defense for your cardholder data environment. This involves more than just a perimeter firewall. It requires a defense-in-depth strategy that protects data at every layer.
Firewall Configuration and Network Segmentation Best Practices
Your firewall ruleset should be your most scrutinized document. The default rule must be "deny all" traffic. You should then create specific "allow" rules only for traffic that is absolutely necessary for business.
All rules must be documented with a business justification. What's more, these rules should be reviewed at least every six months.
Effective network segmentation isolates the CDE from all other networks. This can be achieved physically or logically using VLANs. The goal is to ensure that a compromise on the corporate network cannot spread to the CDE.
For guidance on achieving this, understanding the principles of a PCI DSS Certification is a great starting point. Consequently, this drastically reduces your audit scope and strengthens your security posture.
Securing System Configurations Beyond Default Settings
Never deploy any system with its default vendor-supplied passwords and settings. These are publicly known and are the first thing an attacker will try.
You must develop secure configuration hardening standards for all system components. These standards should cover operating systems, databases, and network devices.
For example, your standards should mandate disabling unnecessary ports and services. They should also require changing all default credentials before a system is put into production.
These hardening guides should be part of your formal change control process. Thus, any new system deployed in your environment will be secure from day one, which is a core tenet for any PCI DSS Service Provider.
Protecting Cardholder Data: The Core of PCI DSS
The ultimate goal of PCI DSS is to protect cardholder data. This involves multiple layers of defense, including strong encryption and strict data retention policies.
Advanced Encryption for Data-in-Transit and Data-at-Rest
All cardholder data transmitted over open, public networks must be encrypted. Use strong cryptographic protocols like TLS 1.2 or 1.3. Avoid all versions of SSL and early TLS. For data stored at
rest, you must render the primary account number (PAN) unreadable. This can be done th rough encryption, truncation, tokenization, or hashing.
Encryption of data at rest should be implemented at the database, file, or disk level. Your choice depends on your specific architecture.
However, the key management practices discussed earlier are paramount. Without secure key management, your encryption is merely a fragile illusion of security.
Data Retention Policies and Secure Deletion Methods
A simple rule of thumb: you cannot lose data you do not have. Therefore, you must develop a formal data retention policy. This policy defines how long you will store cardholder data.
It must also specify a business justification for keeping it. After the retention period, data must be securely deleted.
Secure deletion means the data is unrecoverable. Simply deleting a file is not enough. You must use techniques like disk wiping or cryptographic erasure.
For paper records, cross-cut shredding or incineration is required. This disciplined approach minimizes the amount of sensitive data you store. As a result, it significantly reduces your risk profile.
Implementing Strong Access Control Measures for PCI DSS
Controlling who can access cardholder data is a critical component of the PCI DSS. This is achieved through strict identity and access management controls.
The Principle of Least Privilege in PCI DSS
Every user should only have the minimum level of access necessary to perform their job. This is the principle of least privilege.
It applies to system administrators as well as regular users. For instance, a customer service representative should not have access to the full credit card number.
To implement this, you must define roles and responsibilities clearly. Each role should have a corresponding set of access permissions. You must review these permissions regularly, at least every six months.
In addition, access should be revoked immediately when an employee leaves the company. This prevents orphaned accounts from becoming a security risk.
Multi-Factor Authentication (MFA) as a Non-Negotiable Control
Multi-factor authentication is one of the most effective security controls. It requires users to provide two or more verification factors to gain access. PCI DSS requires MFA for all remote access into the CDE. It is also required for all non-console administrative access.
You should implement MFA using strong authentication methods. For example, use a mobile authenticator app or a hardware token. Avoid using less secure methods like SMS-based codes if possible.
Implementing MFA across your environment dramatically raises the bar for attackers. It makes stolen credentials much less useful.
Maintaining a Continuous Vulnerability Management Program
A secure environment today may be vulnerable tomorrow. Therefore, a continuous vulnerability management program is essential for maintaining your PCI DSS compliance.
Regular Scanning and Penetration Testing
You must perform regular vulnerability scans of your environment. Internal and external scans must be conducted at least quarterly by an Approved Scanning Vendor (ASV). Any "high" or "critical" vulnerabilities found must be remediated promptly.
In addition to scanning, PCI DSS requires annual penetration testing. This involves simulating a real-world attack to identify weaknesses. Both network-layer and application-layer penetration tests are required.
The results of these tests must be used to improve your security controls. It is a critical feedback loop for your security program.
Patch Management and Secure Coding Standards
You must have a formal process for identifying and applying security patches. All critical patches should be applied within one month of their release. This requires a comprehensive asset inventory and a reliable patch management system.
For in-house developed software, you must follow secure coding standards. These standards help prevent common vulnerabilities from being introduced into your applications.
Developers must be trained on these standards annually. By addressing vulnerabilities at the source, you reduce the likelihood of a successful application-layer attack.
Real-World PCI DSS Implementation: A Case Study
Theoretical knowledge is valuable, but real-world application provides the clearest lessons. Let's examine a common scenario to illustrate the strategic implementation of PCI DSS.
This case study highlights the journey from a reactive, checklist-driven approach to a sustainable, security-focused program. It demonstrates how challenges can be turned into opportunities for strengthening overall security.
The Challenge: A Retailer’s Struggle with PCI DSS Compliance
A mid-sized e-commerce retailer was facing its third consecutive failed PCI DSS audit. Their approach was purely tactical. Each year, a small IT team would scramble weeks before the audit.
They would try to patch systems and fill out the Self-Assessment Questionnaire (SAQ). However, they lacked a cohesive strategy. Their network was flat, with no segmentation between the CDE and the corporate network.
Furthermore, developers were deploying code directly to production without security reviews. Logging was enabled but logs were never reviewed. The company was stuck in a cycle of failing, remediating, and then letting controls degrade over the year.
The board was growing concerned about the mounting risks. They knew they needed a fundamental change in their approach to payment security.
The Strategic Approach to PCI DSS Remediation
The new CISO initiated a complete overhaul of their PCI DSS program. The first step was to secure executive buy-in for a long-term strategy.
lass="yoast-text-mark" />>
The CISO framed it not as a compliance cost but as a business enabler. He demonstrated how a secure environment builds customer trust and reduces breach-related financial risk.
Next, the team engaged a qualified security partner, similar to what a firm like Intervalle Technologies provides, to properly define the CDE scope. They implemented robust network segmentation using VLANs and strict firewall rules. This immediately reduced the number of in-scope systems by over 70%.
Subsequently, they deployed a centralized logging and monitoring solution (SIEM). This provided visibility into all activities within the newly defined CDE. The team also integrated automated security testing tools into their software development pipeline. Understanding and Succeeding in PCI DSS Certification became a key resource for their internal training programs.
The Outcome: Achieving Sustainable Compliance and Security
After a six-month remediation project, the retailer passed its Report on Compliance (ROC) audit with no major findings. More importantly, the new controls were embedded into their daily operations. Security was no longer an annual event; it was a continuous process.
>
/>The SIEM provided daily alerts on suspicious activity. The development team now caught vulnerabilities before code reached production.
The initial investment in segmentation and tools paid off handsomely. Audit costs were reduced due to the smaller scope. The security team was no longer fighting fires.
Instead, they could focus on proactive threat hunting and risk management. The retailer transformed its PCI DSS program from a liability into a strategic asset.
Their experience shows that with the right strategy and expertise, sustainable compliance is achievable. This often involves partnering with a trusted advisor like Intervalle Technologies to navigate complex technical requirements.
Future Outlook: PCI DSS v4.0 and Beyond
<p>
The world of payment security is not static. The Payment Card Industry Data Security Standard (PCI DSS) e
volves to address new technologies and emerging threats. The release of PCI DSS v4.0 marks a significant shift in the compliance landscape. Security
leaders must look ahead to understand these changes. They need to adapt their strategies to ensure their programs remain effective and future-proof.
Key Changes and a New Approach in PCI DSS v4.0
PCI DSS v4.0 introduces a major philosophical change: the customized approach. This allo ws organizations to design their own security controls. They must demonstrate that their custom controls meet the stated objective of a specific requirement. This prov
ides flexibility for mature organizations to innovate. However, it also requires a robust risk analysis and testing process.
Other key changes include updated requirements for multi-factor authentication. Stronger password requirements are also included. Additionally, there is an increased focus on preventing e-commerce skimming attacks.
The transition period for v4.0 ends in March 2025. Therefore , organizations must already be well on their way to implementing these new and updated controls. This shif t emphasizes intent over prescription, a key evolution for the credit card standards.
The Impact of Cloud and Serverless on PCI DSS Scope
The rapid adoption of cloud computing presents new challenges for PCI DSS compliance. Defining the CDE scope in a dynamic, multi-cloud environment can be complex. The shared responsibility model is a critical concept to understand.
>
The cloud provider is responsible for the security <em>of the cloud. The customer is responsible for security in the cloud.
This means your organization is still responsible for configuring cloud services securely. For instance, you must correctly configure identity and access management (IAM) roles. You are also responsible for encrypting data stored in cloud buckets.
The rise of serverless computing and containers further complicates scope definition. Organizations need deep cloud security expertise to ensure their cloud environments meet PCI DSS requirements.
Strategic Recommendations for Future-Proofing Payment Security
To stay ahead, CISOs should adopt a forward-looking security strategy. First, embrace a risk-based approach to compliance.
Focus on the intent behind each PCI DSS control, not just the letter of the requirement. This mindset will serve you well, especially with the flexibility offered by v4.0.
Second, invest heavily in automation. Automate security checks in your CI/CD pipeline. Use infrastructure-as-code to deploy securely configured environments.
Automation reduces human error and ensures controls are consistently applied. Finally, foster a culture of continuous security improvement. Your PCI DSS program should not be a static project.
It must be a living, breathing part of your organization's DNA. It must adapt to new technologies and evolving threats.
Conclusion
The journey to mastering PCI DSS is a continuous strategic endeavor. It extends far beyond the confines of an annual audit checklist. For security leaders, the standard should be viewed as a powerful framework.
It helps build a resilient defense against sophisticated payment card threats. By focusing on technical root causes, you address the core of your security vulnerabilities. This proactive approach transforms compliance from a burden into a significant business advantage.
In summary, effective PCI DSS management hinges on several key pillars. These include robust network segmentation and strong encryption. It also requires diligent logging and a secure development lifecycle.
Adopting this holistic view ensures not only compliance but also a tangible reduction in risk. As the threat landscape and standards like v4.0 evolve, this strategic, forward-looking posture is essential. Ultimatel y, it protects your customers, your brand, and your bottom line.
To elevate your payment security strategy and navigate the complexities of PCI DSS, expert guidance is invaluable. Contact Intervalle Technologies today to learn how our seasoned security professionals can help you build a sustainable and effective compliance program.
