Identity and Access Management (IAM) is crucial for efficient IT operations. It helps organizations control access to resources. This streamlines processes and enhances security.
IAM systems manage digital identities and ensure that only authorized users can access sensitive data. Modern IAM solutions adapt to the cloud and address today’s complex IT environments.
The integration of authentication methods, such as multi-factor authentication and single sign-on, improves user experience. At the same time, it boosts security. IAM also supports key principles like least privilege and the zero trust model, ensuring robust protection.
By managing identity lifecycles and handling user provisioning, IAM simplifies compliance. It also conducts access reviews for better governance. This article will explore IAM’s role, its evolution, and how it supports modern IT operations.
What is Identity and Access Management (IAM)?
Identity and Access Management (IAM) is a vital framework for controlling access to an organization's resources. It manages digital identities and ensures that only the right people have access to specific systems. This is essential for maintaining security and compliance in IT environments.
Key Components of IAM
Identity Management
Identity Management involves creating and maintaining user identities. Each identity includes attributes like usernames, roles, and access rights. It's crucial to keep this database up-to-date as personnel changes occur.
Access Management
Access Management comes into play once a user is authenticated. It defines which resources the user can access based on preset permissions. These permissions are often linked to job roles or security levels.
Authentication and Authorization
Authentication is the process of verifying a user’s identity. This can be done through credentials such as passwords or digital certificates. Once authenticated, the user moves to the next step—access management.
Authorization controls what actions a user can take after authentication. Users are only allowed to perform tasks that fit their role within the organization.
Identity Governance monitors user activity to ensure compliance with security policies. It tracks potential misuse of access and provides audit trails, which are essential for regulatory compliance.
Importance of IAM
With the rise of remote work and cloud services, securing access for employees, contractors, and devices has become more complex. IAM systems help automate user provisioning and enforce security policies. This reduces the risk of data breaches by ensuring that only authorized users access sensitive information.
Benefits of IAM
IAM strengthens security by preventing unauthorized access and limiting the chances of data breaches. It also supports regulatory compliance by keeping detailed records of user activities. Moreover, it enhances operational efficiency by automating identity management tasks, reducing manual errors and time spent on user management.
Evolution of Identity and Access Management
The evolution of Identity and Access Management (IAM) is driven by rapid technology changes and business demands. Traditional IAM focused on managing identities within company boundaries. However, as businesses adopted cloud services, these methods became inefficient.
Cloud-based IAM emerged to address this gap, offering scalable and flexible solutions. This shift aligns with the broader move toward digital transformation, which requires more sophisticated access controls.
Moreover, modern IAM emphasizes security through multi-factor authentication and zero-trust principles. As threats continue to evolve, IAM plays a crucial role in protecting digital ecosystems. It also ensures secure access across diverse environments.
Traditional IAM vs. Modern IAM Solutions
Identity and Access Management (IAM) has changed significantly due to evolving technology and business demands. Traditional IAM methods focused on controlling access within a network perimeter. However, businesses are now moving to the cloud, requiring IAM to adapt.
Modern IAM solutions offer more flexibility, enabling secure access from anywhere. This shift addresses the growing need for managing remote workforces and complex digital environments.
Additionally, advanced IAM includes features like multi-factor authentication and AI-driven threat detection. These innovations provide stronger security and better user experiences. Furthermore, they streamline compliance with regulations. Thus, businesses can effectively meet security challenges.
| Feature | Traditional IAM | Modern IAM Solutions |
| Context Awareness | Limited contextual awareness; decisions based on predefined rules and roles. | Advanced context-based controls, considering factors like behavior, location, and device type. |
| Administrative Overhead | High administrative effort; requires significant IT support for tasks like password resets and access requests. | Reduced overhead through automation and AI, minimizing manual tasks such as identity provisioning. |
| Scalability | Struggles to scale efficiently in growing or complex environments. | Cloud-based scalability; easily adapts to growing organizations and modern user demands. |
| Integration | Rigid architecture, requiring manual configuration and maintenance for integration with various applications. | Seamless integration with modern apps via standard protocols like OpenID Connect and SAML. |
| Security Features | Basic security controls with limited features. | Incorporates advanced security features such as MFA, SSO, and adaptive access controls. |
| Automation | Manual processes dominate identity management, leading to inefficiencies. | Automation through AI and ML for provisioning, de-provisioning, and lifecycle management. |
| Platform Centralization | Lacks centralization, making auditing and administration complex. | Centralized platform simplifying workflows, administration, and user experience across applications. |
| Performance | Struggles to meet the demands of modern, globally distributed environments. | Designed for high performance, with horizontal scaling to handle global identity services efficiently. |
| Flexibility | Limited flexibility due to on-premise infrastructure. | Cloud-based flexibility, supporting remote workforces and offering integration with top cloud providers. |
| Cost Efficiency | High infrastructure and administrative costs as the organization grows. | Reduced costs due to cloud-based architecture and automated identity management processes. |
Cloud-Based Identity and Access Management
Cloud-Based Identity and Access Management (IAM) is essential for organizations that want to secure their digital environments. It also ensures efficient access for users.
Cloud IAM centralizes control over user identities and access across platforms. Consequently, it streamlines operations and enhances security.
As a Software as a Service (SaaS), it eliminates the need for on-premise infrastructure. Key features include Single Sign-On (SSO), which simplifies access through a single login for multiple apps. Additionally, Multi-Factor Authentication (MFA) adds another layer of security.
Administrators can easily manage users, permissions, and security policies from one dashboard. Furthermore, Cloud IAM integrates with existing platforms using standard protocols.
It also scales with growing business needs. The benefits include cost savings, flexibility, improved security, and easier compliance management. Thus, it becomes a critical tool for modern organizations that aim to protect sensitive information.
AWS identity and access management iam
AWS Identity and Access Management (IAM) is integral to Cloud-Based Identity and Access Management. This service enables organizations to securely manage access to their cloud resources. AWS IAM allows users to control access to AWS services and resources under specific conditions. It also enables the creation and management of AWS users and groups. Moreover, administrators can set permissions to allow or deny resource access effectively.
Key Features AWS identity and access management iam
- Fine-Grained Access Control:
IAM policies specify permissions for users, groups, and roles. These policies define access rights to resources and the actions users can perform. Written in JSON format, these policies can include conditions for access based on various parameters. - User and Group Management:
Individual identities represent users with specific permissions. Groups simplify the administration of permissions by applying policies collectively. This approach streamlines permission management across the organization. - Roles and Temporary Credentials:
IAM roles enable users or services to assume temporary security credentials for specific tasks. This capability is useful for applications accessing other AWS services without embedding long-term credentials. - Multi-Factor Authentication (MFA):
To enhance security, IAM supports MFA, requiring additional verification along with usernames and passwords. This extra layer of security helps protect user accounts. - Identity Federation:
IAM integrates with external identity providers, allowing users to log in with existing credentials. This integration eliminates the need for separate AWS-specific accounts. - Access Analyzer:
The Access Analyzer feature identifies resources shared with external entities. This ensures compliance with least-privilege principles by analyzing permissions granted across the organization.
Components of AWS Identity and Access Management
- Users: Individual accounts that represent people or applications accessing AWS resources.
- Groups: Collections of users sharing the same permissions, which simplifies management.
- Policies: Documents defining permissions; they can be reusable or specific to a user or group.
- Roles: Temporary access credentials that users or services can assume for specific tasks.
Benefits of AWS Identity and Access Management
- Cost-Effective: IAM incurs no additional charges; users only pay for AWS resources utilized.
- Centralized Control: IAM provides a single interface for managing user access across AWS services. This improves security and compliance significantly.
- Scalability: As organizations grow, IAM scales effortlessly to accommodate more users, roles, and resources.
- Security Compliance: IAM assists organizations in meeting regulatory requirements by logging user activities and access rights.
AWS Identity and Access Management is essential for securely managing access to AWS resources. With features like fine-grained access control, role-based permissions, multi-factor authentication, and identity federation, IAM equips organizations with the tools to protect their cloud environments effectively.
Core Principles of Identity and Access Management
Understanding the foundational principles guiding IAM can significantly enhance your organization's security posture.
First, consider how limiting user access based on necessity can reduce risks. Additionally, dividing responsibilities helps mitigate potential threats that arise from conflicting roles.
Lastly, adopting a security framework that emphasizes continuous verification can fundamentally shift your approach to identity management. By embracing these essential concepts, you can establish a more robust IAM strategy, ultimately fostering trust and resilience within your organization. Let’s explore these principles in detail.
Least Privilege Principle in IAM
The Principle of Least Privilege (PoLP) is essential in Identity and Access Management (IAM). It focuses on granting users only the access they need for their job functions. This approach is vital for enhancing security, minimizing risks, and ensuring compliance within organizations.
Key Aspects of the Principle of Least Privilege
Minimal Access Rights
Users should receive only the permissions necessary for their roles. This avoids unnecessary access, which can create security vulnerabilities. For example, a marketing manager should not access software development environments.
Reduction of Risk
Limiting permissions helps organizations contain the potential impact of security breaches. If an account with minimal privileges is compromised, the damage is much less severe than that from an account with extensive access rights.
Prevention of Privilege Creep
Over time, users may accumulate excessive permissions due to promotions or role changes. This phenomenon, known as "privilege creep," can lead to security issues. Regular audits and reviews are crucial for ensuring that access rights stay relevant as users transition within the organization.
Compliance and Regulatory Requirements
Many regulatory frameworks, including the Loi 18-07 on the protection of personal data, require strict access controls. Following the least privilege principle enables organizations to meet these compliance demands and simplifies the audit process.
Implementation Strategies for PoLP
Organizations can adopt several strategies to implement PoLP:
Role-Based Access Control (RBAC): This assigns permissions based on user roles, ensuring that only necessary access is granted.
Just-in-Time Access: This provides temporary elevated permissions for specific tasks, which are revoked afterward to maintain security.
Regular Access Reviews: Conducting periodic audits of user permissions ensures alignment with current job functions.
Integration with Zero Trust Models:
The least privilege principle aligns effectively with Zero Trust security models. These models promote continuous verification and minimal access rights, emphasizing that no user or device should be trusted by default.
The Principle of Least Privilege is vital for a secure and efficient IAM framework. By ensuring users have only the necessary permissions for their roles, organizations can mitigate risks associated with unauthorized access. This principle enhances compliance efforts and streamlines operational processes. Regular audits and adherence to PoLP help organizations protect sensitive data while enabling productivity.
Separation of Duties in Identity and Access Management
Separation of Duties (SoD) is essential for effective Identity and Access Management (IAM). It involves dividing responsibilities among multiple individuals. This division prevents fraud, errors, and conflicts of interest, especially in sensitive operations. One person should never control all aspects of a process.
Key Concepts of Separation of Duties
Definition:
SoD ensures that no single individual has authority over conflicting tasks. For instance, the person initiating a financial transaction should not approve it. This separation creates a system of checks and balances within the organization.
Categories of Duties:
SoD typically divides tasks into four main categories:
- Authorization: Approving transactions or operations.
- Custody: Managing access to physical and digital assets.
- Reconciliation: Verifying the accuracy and completeness of transactions.
- Recordkeeping: Maintaining accurate records of transactions.
Importance in Compliance:
Regulatory frameworks, like the Sarbanes-Oxley Act (SOX), require SoD to prevent fraud. Organizations must implement SoD policies to comply and avoid penalties.
Risk Mitigation:
Enforcing SoD significantly reduces insider threats, such as fraud or unauthorized access. It also lowers the risk of accidental errors, as multiple individuals oversee critical processes.
Implementation Challenges:
While vital for security, SoD can complicate business processes and increase operational costs. Organizations must balance security with efficiency to maintain productivity and employee satisfaction.
Managing Separation of Duties
Policy Development:
Organizations should define and document responsibilities related to SoD clearly. Specify who is accountable for each task to ensure roles are well understood.
Monitoring and Compliance:
Regular audits and reviews are necessary for compliance with SoD policies. Automated tools can identify potential violations in real-time, allowing organizations to address issues proactively.
Identity Governance:
Implementing Identity Governance and Administration (IGA) solutions can streamline SoD management. These solutions provide visibility into user access, helping detect conflicts during access requests.
Training and Awareness:
Educating employees about the importance of SoD fosters a culture of compliance and security within the organization. Understanding individual responsibilities enhances overall security.
Separation of Duties is a fundamental principle in IAM. It enhances security by preventing excessive control over critical processes. Effective SoD policies mitigate risks associated with fraud and errors while ensuring compliance with regulations. Balancing these controls with operational efficiency is vital for maintaining productivity and safeguarding sensitive information.
Zero Trust Security Model and its Impact on IAM
The Zero Trust Security Model reshapes cybersecurity by changing how organizations manage security. Its core principle is "never trust, always verify," meaning no user or device is trusted by default, whether inside or outside the corporate network. This approach greatly affects Identity and Access Management (IAM).
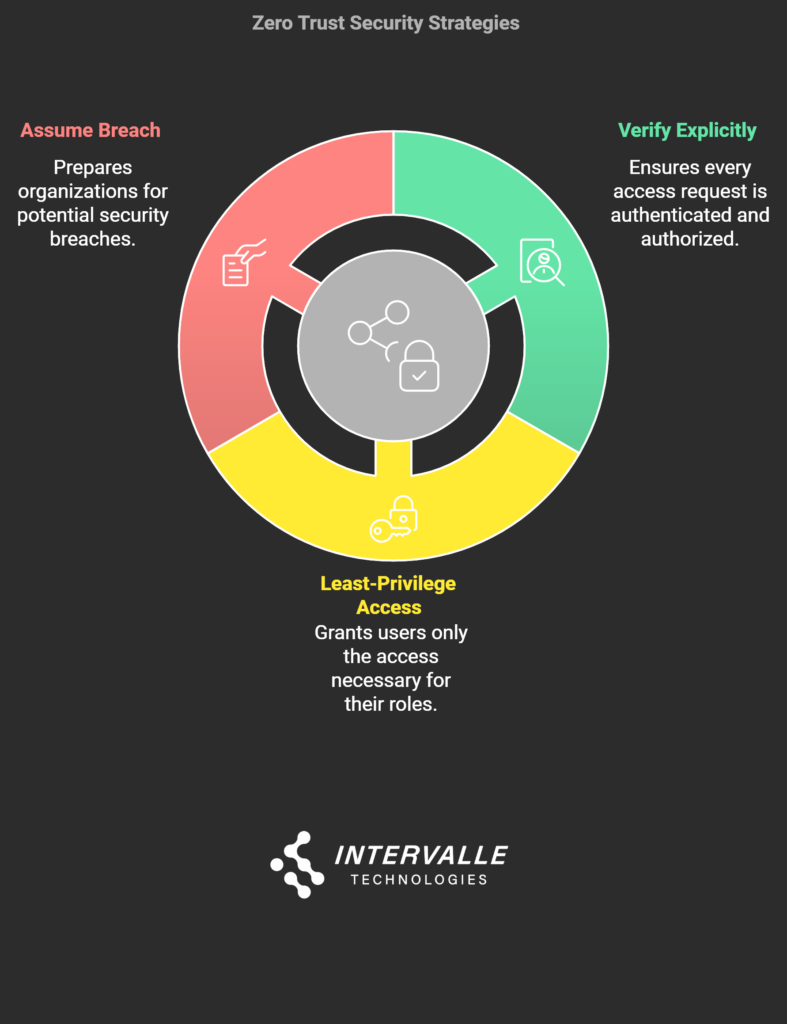
Key Principles of Zero Trust
- Verify Explicitly:
Each access request must be authenticated and authorized using all available data, such as user identity, location, device health, and service classification. Continuous verification ensures that only legitimate users can access resources. - Least-Privilege Access:
Users receive the minimum access necessary for their roles. This practice reduces the risk of unauthorized access and limits damage from compromised accounts. - Assume Breach:
Organizations must act as if breaches can happen at any moment. This perspective encourages proactive measures to contain threats and minimize their impact through segmentation and monitoring.
Impact on IAM
- Enhanced Identity Verification:
Zero Trust emphasizes robust identity verification methods, including Multi-Factor Authentication (MFA). IAM systems need to continuously validate user identities before granting access to sensitive resources. - Dynamic Access Controls:
IAM solutions must implement dynamic access controls that adjust permissions based on real-time risk assessments. For example, if a user tries to access resources from an unusual location, additional authentication may be required. - Granular Access Policies:
The Zero Trust model demands more specific access control policies in IAM systems. Organizations should define permissions for each user based on their roles, responsibilities, and context. - Continuous Monitoring and Analytics:
IAM solutions need continuous monitoring capabilities to detect unusual user behavior. Real-time analytics help identify potential threats and allow for immediate responses. - Integration with Other Security Measures:
Zero Trust requires IAM systems to integrate with other security measures, such as endpoint security and network segmentation. This holistic approach ensures comprehensive protection across all IT layers. - Support for Remote Workforces:
As remote work becomes more common, Zero Trust principles are increasingly relevant. IAM systems must secure access for users connecting from various locations and devices while maintaining strict security protocols.
The Zero Trust Security Model profoundly impacts Identity and Access Management by requiring stronger identity verification, dynamic access controls, and continuous monitoring. As organizations adopt this model to address evolving cybersecurity threats, IAM will be vital in ensuring secure access to resources while minimizing risks from unauthorized access and data breaches. By implementing Zero Trust principles, organizations can improve their overall security posture in a complex digital environment.
Identity and Access Management Lifecycle
Managing user identities and access is crucial for organizational security. Understanding the identity and access management (IAM) lifecycle can significantly enhance your security posture. First, user provisioning and deprovisioning ensure that individuals have the right access at the right time. Next, effective access request and approval workflows streamline the process while maintaining security integrity. Continuous monitoring and access reviews provide insights into user behavior and system vulnerabilities. Finally, implementing role-based access control (RBAC) simplifies permissions management, ensuring users only access necessary resources. Let’s explore these key components for a comprehensive IAM strategy.
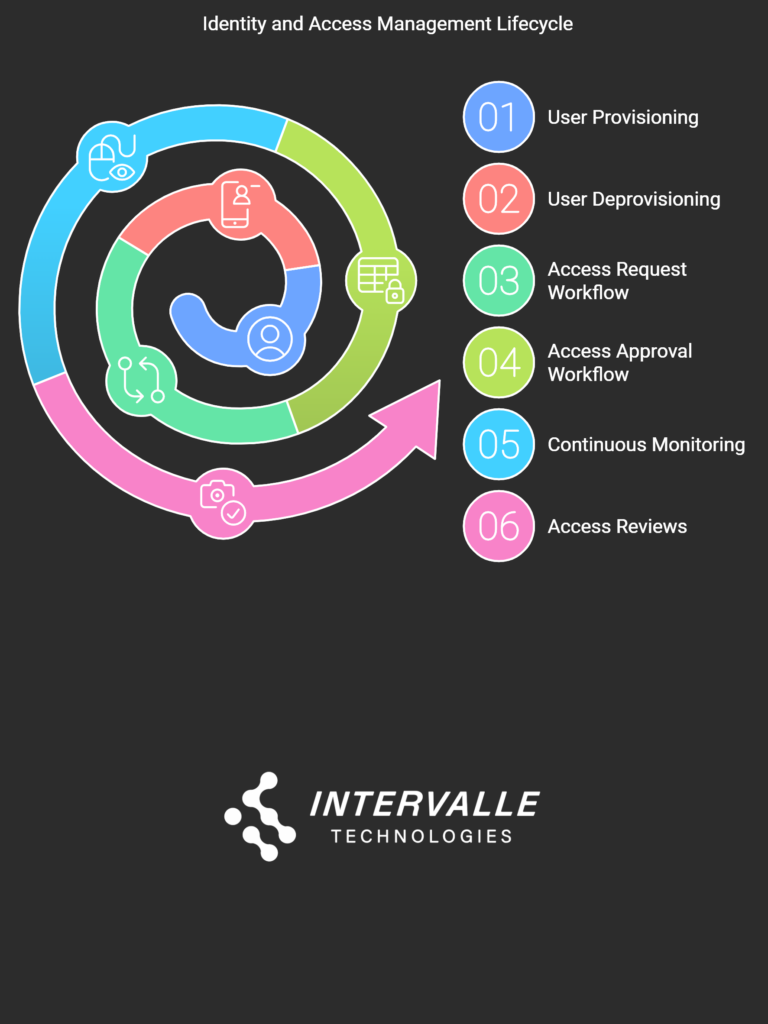
User Provisioning and Deprovisioning in IAM
User provisioning and deprovisioning are essential for effective Identity and Access Management (IAM). They ensure secure management of user identities and access rights in an organization. This overview outlines their significance and functions.
Definition and Importance of User Provisioning
User provisioning involves creating, maintaining, and disposing of a user's digital identity and access across various resources and applications. The main goal is to protect systems and data while enabling users to perform tasks that align with business objectives.
Types of User Provisioning
- Self-Service: Users manage aspects like password updates independently.
- Discretionary: Administrators grant access based on specific needs.
- Workflow: Access follows predefined workflows and requires mandatory approvals.
- Automated: Software solutions manage accounts based on set rules, improving efficiency for administrators.
User Deprovisioning
Deprovisioning means removing or adjusting user access rights when someone leaves the organization or changes roles. This process ensures timely revocation of access during employee offboarding, preventing unauthorized access and protecting sensitive information.
Role of Modern IAM Systems
Historically, user provisioning was a manual process. IT administrators created or updated accounts based on requests via email or paper forms. This method was time-consuming and prone to errors. Modern IAM solutions automate provisioning using predefined policies and workflows, integrating with HR systems and IT infrastructure.
Automated user provisioning streamlines account creation. When a new employee starts, their details entered in an HR platform trigger automated account creation. This includes network accounts, email, and access to necessary tools.
Automated deprovisioning processes quickly remove access for departing staff across all applications. This helps prevent security risks associated with active sessions on personal devices.
Benefits
- Enhanced Security: Automated provisioning grants just enough access without excess. Attribute-based access control aligns permissions with organizational roles, reducing insider threats.
- Improved Efficiency: Automation decreases the workload on IT teams. This speeds up employee onboarding and offboarding while minimizing human errors related to permissions.
- Compliance and Audit Readiness: IAM systems maintain accurate records to ensure compliance with regulations. They also provide detailed logs of access rights and user activities for audits.
- Scalability & Reduced IT Costs: IAM systems manage changes in user volume easily. This scalability helps reduce IT costs associated with manual account management.
By implementing these automated solutions in IAM frameworks, organizations can streamline user lifecycle management. This ensures robust access control that aligns with changing roles and business needs. Ultimately, it enhances operational efficiency and strengthens security posture.
