Data leaking: What it is, why it matters, and how it impacts your business
Effective data leaking prevention is the cornerstone of modern enterprise cybersecurity. This issue, also known as information leakage, represents a critical vulnerability for organizations. It exposes sensitive data to unauthorized parties.
A single incident can trigger devastating financial and reputational consequences. Many leaders mistakenly view this as solely an external threat. However, the reality is far more complex.
It involves internal errors, process gaps, and sophisticated attack vectors. The risk of a severe data breach has never been higher.
This guide moves beyond basic cybersecurity advice. It provides a strategic framework for Chief Information Security Officers (CISOs). We will also offer insights for security architects and IT leaders.
We delve into the technical root causes of information leakage. Furthermore, we present actionable solutions based on proven industry frameworks. You will gain a clear understanding of the threat landscape.
This article equips you with the knowledge to build a resilient defense. You can protect your company’s most valuable digital assets.
This is not just about compliance. It is about ensuring business continuity and competitive advantage.
The Challenge of Data Leaking and Information Leakage
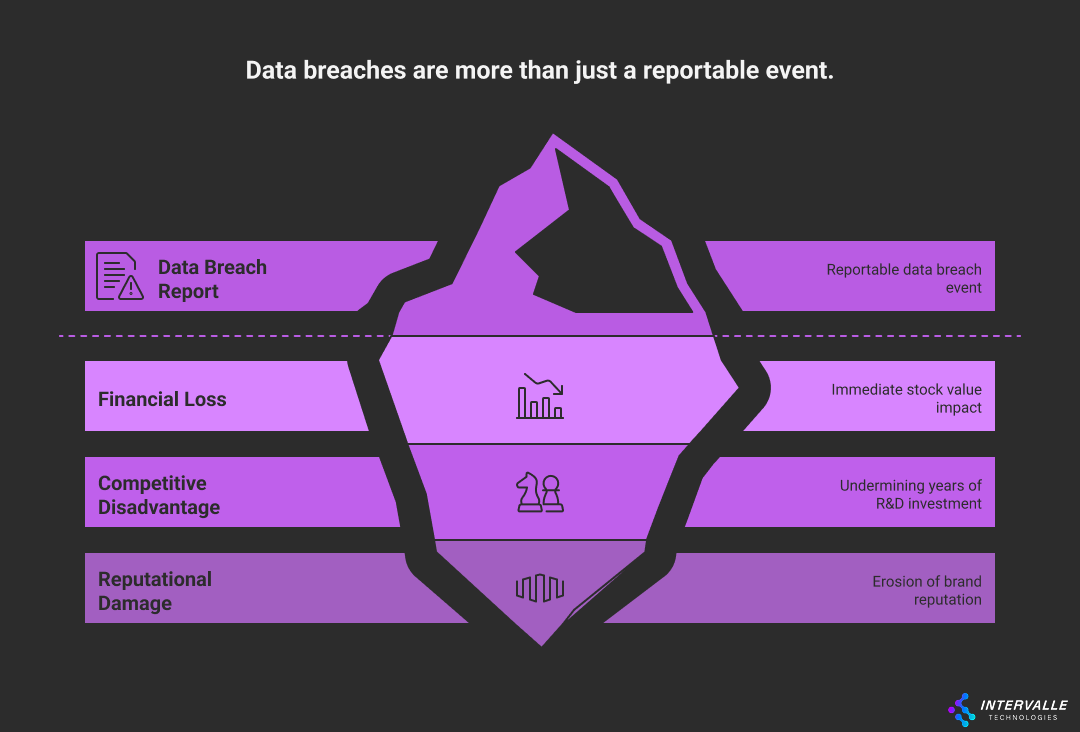
Understanding the full impact of data leaking is essential. The consequences extend far beyond immediate remediation costs. They permeate every facet of the business.
This includes financial stability, customer loyalty, and market position. A significant data breach can become an existential threat. It erodes trust built over years in a matter of hours.
The threat landscape is dynamic. Attackers constantly evolve their tactics to exploit new vulnerabilities.
This environment demands constant vigilance from security leaders. The average cost of a data breach reached a record high of $4.45 million in 2023. This figu re underscores the immense financial risk. Yet, the
numbers only tell part of the story. The intan gible costs are equally damaging. These inc lude loss of intellectual property and diminished brand equity. Effective
ly countering information leakage requires a deep appreciation of these multifaceted challenges. It’s a ba ttle fought on technical, financial, and reputational fronts. Your stra tegy must address all three with equal focus.
The Staggering Financial Cost of a Data Breach
The financial fallout from information leakage is severe. IBM's 2023 report highlights this stark reality. The global average cost of a data breach rose 15% over three years.
For critical infrastructure organizations, the costs are even higher. These sectors averaged $5.04 million per incident. These dir ect costs include several key components. They cove
r incident response, forensic investigations, and regulatory fines. Legal fee s and settlement costs can also escalate rapidly.
However, the direct expenses are just the beginning. The long-tail financial impact can be more damaging. This includes increased insurance premiums and the cost of customer notifications.
Offering credit monitoring services to affected individuals adds another layer of expense. Lost business is the single largest cost category. It accounts for nearly 40% of the total financial impact.
Customers leave due to diminished trust. Potential clients choose competitors. This sustained revenue loss cripples long-term growth.
Preventing data leaking is not a cost center. It is an investment in financial preservation.
Reputational Damage and Loss of Customer Trust
Reputation is a priceless corporate asset. A significant data leaking incident can destroy it overnight. The subsequent loss of customer trust is difficult to quantify but profoundly impactful.
News of a data breach spreads instantly through social media and news outlets. This creates a public relations crisis that can spiral out of control.
Your company’s name becomes synonymous with insecurity. This perception is incredibly difficult to reverse.
Customers are increasingly aware of data privacy issues. They entrust their personal and financial information to you. A breach of that trust feels like a personal violation.
A recent survey showed that 81% of consumers would stop engaging with a brand online following a data breach. This mass exodus directly impacts revenue streams. Moreover, it creates a negative feedback loop.
Negative reviews and word-of-mouth warnings deter new customers. Rebuilding that trust requires transparency, time, and significant investment.
It is a long, arduous process that many companies never fully complete. The best strategy is to avoid the damage in the first place.
Root Causes and Technical Factors Behind a Data Breach
To effectively prevent data leaking, one must first understand its origins. The root causes are often a mix of technical vulnerabilities and human error. Attackers exploit the weakest link in the security chain.
This is frequently not a sophisticated zero-day exploit. Instead, it is a simple misconfiguration or a compromised credential.
Examining these technical factors provides a clear roadmap for remediation. It allows security teams to focus resources where they matter most.
A successful defense strategy requires deep visibility into your entire technology stack. This includes on-premises infrastructure, cloud environments, and third-party services. The modern enterprise is a complex, interconnected ecosystem.
Each connection point represents a potential vector for information leakage. Understanding cybersecurity basics is not enough. Leaders must grasp the nuanced technical failures that lead to a major data breach.
This knowledge empowers proactive threat hunting and robust architectural design. It is the foundation of a truly resilient security posture.
Cloud Misconfigurations and Exposed Infrastructure
The rapid adoption of cloud computing has introduced new attack surfaces. Cloud misconfigurations are now a leading cause of data leaking. Security teams often struggle to keep pace with agile development cycles.
This can lead to critical errors. Publicly accessible Amazon S3 buckets are a classic example. Developers may inadvertently leave storage buckets open to the internet.
This exposes vast quantities of sensitive data with no hacking required. Similarly, misconfigured security groups can expose virtual machines and databases.
These issues are not limited to storage. Unsecured databases, open remote desktop protocol (RDP) ports, and default credentials create easy entry points. Attackers constantly scan the internet for these low-hanging fruit.
Automated tools can identify and exploit these vulnerabilities within minutes of their creation. Proper cloud security posture management (CSPM) is essential.
It provides automated monitoring and remediation of these misconfigurations. Without it, your cloud environment remains a primary source of risk for a devastating data breach.
The Insider Threat: Malicious and Accidental Leakage
Not all threats originate from outside the organization. The insider threat is a significant and often overlooked cause of information leakage. This threat can be categorized into two main types: malicious and accidental.
Malicious insiders intentionally steal data for financial gain or revenge. They abuse their legitimate access privileges to exfiltrate sensitive information. This could include customer lists, intellectual property, or financial records.
Detecting this activity is challenging. Their behavior may initially appear as normal job function.
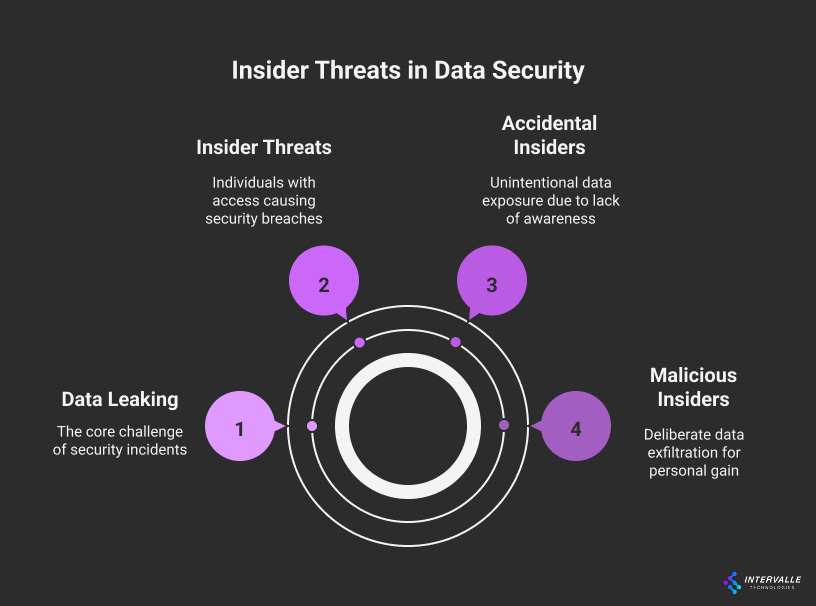
Conversely, accidental data leaking is more common. A well-intentioned employee might inadvertently email a sensitive file to the wrong recipient. They might upload corporate data to a personal cloud storage account.
These actions often violate policy but lack malicious intent. Phishing attacks also play a role here. An employee who falls for a phishing scam can unknowingly provide an attacker with their credentials.
This effectively turns an external attacker into an insider. Both types of insider threats require a combination of technical controls and security awareness training.
Insecure APIs and Third-Party Risks
Modern applications are built on Application Programming Interfaces (APIs). APIs allow different systems and services to communicate with each other. They are the connective tissue of the digital economy.
However, insecure APIs present a massive risk for data leaking. The OWASP API Security Top 10 list highlights common vulnerabilities.
These include broken object-level authorization, excessive data exposure, and lack of rate limiting. An attacker can exploit these flaws to extract large volumes of data.
Your organization’s security is also dependent on your partners and suppliers. This supply chain risk is a growing concern. A data breach at a third-party vendor can directly impact your own data.
If a vendor has access to your systems or data, their vulnerabilities become your vulnerabilities. Vetting the security posture of all third parties is critical. This requires rigorous due diligence and contractual security obligations.
Your defense must extend beyond your own perimeter to your entire digital ecosystem. This is a crucial part of preventing information leakage.
Actionable Solutions and Frameworks to Stop Data Leaking
Preventing data leaking requires a multi-layered, proactive approach. Simply reacting to threats is a losing strategy. CISOs must implement robust frameworks and technical controls.
These measures should be designed to detect, prevent, and respond to information leakage attempts. The goal is to build a resilient security architecture.
This architecture can adapt to evolving threats. It should be deeply integrated into business processes.

This section outlines practical, high-impact solutions. These are not theoretical concepts. They are proven strategies used by leading organizations to protect their data.
We will explore the principles of Zero Trust. We will also discuss the role of Data Loss Prevention (DLP) tools. We’ll also cover leveraging threat intelligence through frameworks like MITRE ATT&CK.
Finally, we will emphasize the importance of strong Identity and Access Management (IAM). Implementing these solutions transforms your security from a defensive cost center into a strategic business enabler.
Implementing a Zero Trust Architecture
Zero Trust is a fundamental shift in security philosophy. The traditional "castle-and-moat" model is no longer effective. Zero Trust operates on a simple but powerful principle: never trust, always verify.
It assumes that a data breach is inevitable or has likely already occurred. Therefore, it eliminates the concept of a trusted internal network. Every access request must be authenticated, authorized, and encrypted.
This applies regardless of where the request originates. This model significantly reduces the risk of data leaking.
Principle of Least Privilege Access
A core tenet of Zero Trust is the principle of least privilege. Users and systems should only have access to the data and resources they absolutely need. This access should only be for the minimum time required to perform their tasks.
Implementing this principle minimizes the potential damage from a compromised account. If an attacker gains access, their movement is severely restricted.
They cannot easily pivot to other systems or access sensitive data repositories. Granular role-based access control (RBAC) policies are essential for enforcement.
Continuous Verification and Micro-segmentation
Zero Trust demands continuous verification of identity and device health. A user who is trusted one moment may not be trusted the next. Factors like location, device posture, and behavior are constantly evaluated.
This dynamic approach allows for real-time risk assessment and response. Furthermore, micro-segmentation is a key technical control. It involves breaking the network into small, isolated zones.
Secure gateways control traffic between these segments. If one segment is compromised, the breach is contained. It cannot easily spread across the entire network, preventing widespread information leakage.
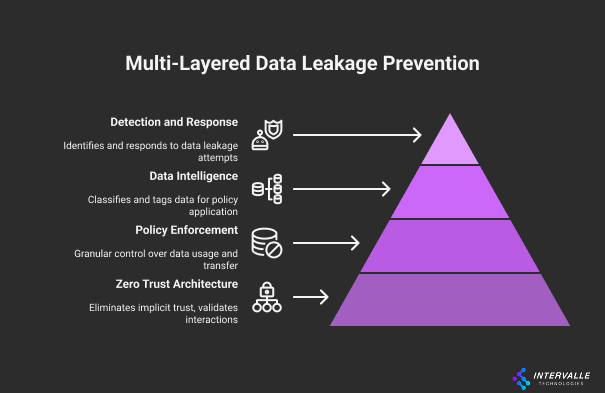
Deploying Advanced Data Loss Prevention (DLP)
Data Loss Prevention (DLP) solutions are critical for preventing data leaking. These tools identify, monitor, and protect data in use, in motion, and at rest. Modern DLP systems use sophisticated techniques.
They apply content inspection and contextual analysis. This helps classify sensitive data. It also enforces policies to prevent its unauthorized transmission.
For example, a DLP policy could block an email containing credit card numbers. It could also prevent files with "confidential" tags from being uploaded to a personal cloud drive.
Effective DLP implementation requires a clear data classification policy. You must first identify what your sensitive data is and where it resides. This includes PII, PHI, intellectual property, and financial data.
Once classified, you can create specific policies for each data type. DLP solutions can be deployed at multiple points. Network DLP monitors traffic leaving the corporate network.
Endpoint DLP runs on individual workstations and servers. Cloud DLP integrates with SaaS applications and cloud platforms.
A comprehensive DLP strategy combines all three. It provides holistic protection against a potential data breach.
Leveraging Threat Intelligence and the MITRE ATT&CK Framework
A proactive defense relies on high-quality threat intelligence. This intelligence provides insights into attacker tactics, techniques, and procedures (TTPs). The MITRE ATT&CK framework is an invaluable resource.
It is a globally accessible knowledge base of adversary behaviors. It is based on real-world observations. Security teams can use ATT&CK to understand how attackers operate.
This knowledge informs threat modeling and detection engineering. It helps you anticipate attacker moves.
You can map your existing security controls to the ATT&CK matrix. This exercise reveals gaps in your defenses. For example, you might have strong controls for initial access.
However, you may lack visibility into credential dumping or lateral movement techniques. This insight allows you to prioritize security investments. You can build detection rules in your SIEM.
These rules can be specifically designed to spot the TTPs most relevant to your organization. Using ATT&CK transforms your security operations from reactive to proactive. It is a cornerstone of preventing sophisticated information leakage.
Strengthening Identity and Access Management (IAM)
Identity is the new security perimeter. Compromised credentials are a primary vector for almost every data breach. Therefore, robust Identity and Access Management (IAM) is non-negotiable.
It is a foundational element of cybersecurity basics and advanced defense. The goal is to ensure only the right people have the right access. They must have access to the right resources at the right time.
This starts with strong authentication. Multi-factor authentication (MFA) should be mandatory for all users. This includes employees, contractors, and partners.
Beyond MFA, advanced IAM includes several other components. Privileged Access Management (PAM) solutions are crucial. They secure and monitor the accounts of administrators and other high-privilege users.
These accounts are prime targets for attackers. Centralized identity governance ensures that access rights are regularly reviewed. They should also be revoked when no longer needed.
This prevents "privilege creep" and reduces the overall attack surface. A mature IAM program is a powerful deterrent against data leaking. It makes it significantly harder for attackers to gain and maintain a foothold.
Real-World Implementation: A Data Leakage Prevention Blueprint
Theory and frameworks are valuable. However, their true worth is demonstrated through real-world application. Let's consider a hypothetical case study.
FinSecure, a mid-sized financial services firm, faced a growing threat of data leaking. Their legacy security model was perimeter-based and reactive. They recognized the need for a strategic overhaul to protect sensitive client data.
This required moving from basic controls to a comprehensive, proactive security posture. The CISO initiated a major project to prevent a future data breach.
The firm understood that an internal effort alone would be insufficient. They needed specialized expertise in modern security architectures. They partnered with an external consultancy to guide their transformation.
This partnership brought in fresh perspectives and deep technical knowledge. The process was structured into clear, manageable phases. It began with a thorough assessment and ended with continuous monitoring.
This blueprint illustrates a practical path for any organization. It shows how to translate strategic goals into tangible security outcomes.
Step 1: Comprehensive Risk Assessment and Threat Modeling
The project began with a deep-dive risk assessment. The goal was to understand FinSecure's unique threat landscape. This was not a simple compliance audit.
It was a comprehensive analysis of their technology, people, and processes. The team mapped all critical data assets. They identified where sensitive client financial data was stored, processed, and transmitted.
This process uncovered several previously unknown "shadow IT" applications. It also found data stored in unsanctioned cloud services.
Next, the team conducted threat modeling exercises using the MITRE ATT&CK framework. They simulated various attack scenarios relevant to the financial sector. This included scenarios like ransomware attacks and insider data exfiltration.
This process highlighted critical vulnerabilities in their existing architecture. They discovered a lack of network segmentation and weak access controls for key databases. The assessment provided a clear, data-driven baseline.
It quantified their risk exposure and created a compelling business case for investment. This detailed analysis was critical for getting executive buy-in.
Step 2: Architecting a Defense-in-Depth Strategy
With a clear understanding of the risks, the next phase was architecture design. The team, including experts from a firm like Intervalle Technologies, designed a new security architecture. This architecture was based on Zero Trust principles.
The design abandoned the old trusted internal network concept. It focused on securing data at its source. Key components of the new architecture included micro-segmentation.
This isolated critical applications and databases from the general corporate network. It severely limited an attacker's ability to move laterally.
The design also incorporated a robust IAM solution with mandatory MFA. It integrated a next-generation DLP system. This sys tem was configured with policies based on FinSecure's data classification scheme. The arch itecture was designed for visibility. All logs
from firewalls, endpoints, and cloud services were centralized in a SIEM. This cre ated a single pane of glass for security monitoring and incident response. The goal was to build multiple layers of defense. If one l
ayer failed, another would be in place to stop the attack. This def ense-in-depth approach is vital for preventing information leakage.
Step 3: Deployment, Monitoring, and Continuous Improvement
The final phase was implementation and operationalization. The new architecture was deployed in a phased approach. This minimized disruption to business operations.
The team started with the most critical assets first. They implemented micro-segmentation around the core client database. Then, they rolled out MFA across the entire organization.
The DLP solution was initially deployed in monitoring-only mode. This allowed the security team to fine-tune policies and reduce false positives.
Once deployed, the focus shifted to continuous monitoring. The Security Operations Center (SOC) used the new SIEM to hunt for threats. They developed playbooks for responding to various types of alerts.
This included alerts for potential data leaking activities. The security posture was not static. The team, with ongoing support from Intervalle Technologies, conducted regular vulnerability scans and penetration tests.
They used the findings to continuously improve their defenses. This iterative process ensures that the security program remains effective against emerging threats. It transforms security into a living, breathing part of the organization.
Future Outlook: The Evolving Landscape of Information Leakage
The fight against data leaking is a continuous journey, not a destination. The threat landscape is constantly evolving. New technologies bring both opportunities and new risks.
Security leaders must look ahead to anticipate future challenges. Staying current on emerging trends is crucial for long-term strategic planning. A security strategy built for today may be obsolete tomorrow.
CISOs must be forward-thinking. They must prepare their organizations for the next wave of cyber threats.
This forward-looking perspective involves two key areas. First, understanding how emerging technologies like AI will be used by both attackers and defenders. Second, preparing for paradigm shifts.
This includes the eventual arrival of quantum computing. This technology threatens to break much of today's encryption. Proactive preparation for these developments is essential.
It will separate the resilient organizations from the vulnerable ones in the years to come. This strategic foresight is a hallmark of effective security leadership. It ensures the long-term protection of sensitive information.
The Double-Edged Sword of Artificial Intelligence
Artificial intelligence (AI) is transforming cybersecurity. It offers powerful new tools for defense. AI-powered security analytics can detect subtle anomalies in user behavior.
It can identify patterns that might indicate a brewing data breach. This enables faster detection and response. AI can automate threat hunting and sift through vast amounts of log data.
This frees up human analysts to focus on more complex investigations. These advancements are making security operations more efficient and effective.
However, AI is also a powerful weapon for attackers. Adversaries are using AI to create highly convincing phishing emails. They can generate deepfake videos and audio for social engineering attacks.
AI can be used to automate vulnerability discovery and exploit development. This arms less-skilled attackers with sophisticated capabilities. The rise of adversarial AI presents a significant challenge.
Security leaders must invest in AI-driven defenses. They must be prepared to combat AI-powered attacks. This new arms race will define the future of information leakage prevention.
Preparing for Post-Quantum Cryptography
Quantum computing poses a long-term, existential threat to data security. A sufficiently powerful quantum computer could break most of the public-key cryptography we rely on today. This includes the algorithms that protect web traffic, financial transactions, and stored data.
An attacker could potentially decrypt vast amounts of previously intercepted encrypted data. This creates a "harvest now, decrypt later" risk. Attackers may already be storing encrypted data, waiting for the day they can break it.
While large-scale quantum computers are still years away, preparation must begin now. The transition to quantum-resistant cryptography will be a massive undertaking. It will require upgrading systems, applications, and infrastructure across the entire organization.
This is not a simple patch. It is a fundamental architectural change. The National Institute of Standards and Technology (NIST) is standardizing new post-quantum cryptographic (PQC) algorithms.
CISOs should begin inventorying their cryptographic systems. They must develop a transition plan. Starting this process early is crucial to avoid a future catastrophic data leaking event.
Conclusion
Preventing data leaking is one of the most critical responsibilities of a modern security leader. The consequences of failure—financial ruin, reputational collapse, and operational disruption—are too severe to ignore. A successful strategy requires moving beyond reactive measures and cybersecurity basics.
It demands a proactive, intelligence-driven, and architecturally sound approach. This means understanding the technical root causes of a data breach.
It also requires implementing robust frameworks like Zero Trust. The goal is to build a resilient organization that protects its data by design.
This guide has outlined the key challenges and actionable solutions. We have explored the financial and reputational impact of information leakage. We examined the technical vulnerabilities in cloud, APIs, and insider threats.
Most importantly, we have provided a blueprint for action. This includes implementing Zero Trust, DLP, and strong IAM. It also means leveraging threat intelligence.
The path to a secure future is clear. It requires strategic investment, technical excellence, and continuous vigilance.
Your organization's data is its lifeblood. Protecting it is not just an IT problem; it is a core business imperative.
Take the first step towards building a truly resilient security posture. Strengthen your defenses against the ever-present threat of data leaking.
Contact the experts at Intervalle Technologies today for a comprehensive risk assessment. Let us help you identify and remediate the hidden vulnerabilities in your environment before they can be exploited.
