Introduction to the SWIFT Customer Security Controls Framework (CSCF)
SWIFT CSCF has undergone significant evolution from 2017 to 2024, tightening security standards for financial institutions worldwide. With escalating cyber threats, financial organizations face increasing regulatory demands, driving the need for robust cybersecurity measures. The continuous updates to SWIFT's Customer Security Controls Framework (CSCF) reflect the sector’s commitment to safeguarding transaction integrity. These changes not only address emerging vulnerabilities but also anticipate future risks. Understanding this evolution is critical for cybersecurity professionals managing compliance and securing critical financial infrastructure.
The Genesis of SWIFT CSCF
The SWIFT Customer Security Controls Framework (CSCF) emerged in response to escalating cyber threats targeting SWIFT’s network. Following major incidents like the 2016 Bangladesh Bank heist, which resulted in the loss of $81 million, SWIFT launched its Customer Security Programme (CSP) that same year. The CSCF was introduced in 2017 to establish a common security foundation across the SWIFT community. It includes both mandatory and advisory controls based on recognized security standards such as NIST and PCI-DSS. The framework focuses on securing environments, managing access, and detecting/responding to threats, ensuring financial institutions are better protected from cyberattacks.
Key Objectives and Principles of SWIFT CSCF
The SWIFT Customer Security Controls Framework (CSCF) outlines essential security principles for financial institutions using the SWIFT network. Its main objectives focus on three critical areas:
- Secure the environment:
- Limit internet exposure and secure critical systems.
- Reduce the attack surface and eliminate vulnerabilities.
- Safeguard physical infrastructure to ensure protection.
- Manage access and limit exposure:
- Prevent credential compromise and tightly control identity management.
- Limit access to sensitive information with strict privilege management.
- Detect and respond effectively:
- Monitor systems for unusual activity or suspicious transactions.
- Establish incident response plans and share information to address potential breaches.
By adhering to these principles, institutions can enhance their cybersecurity posture, protect financial transactions, and strengthen resilience against growing digital threats. Regular assessments and staff training ensure continued alignment with these objectives, promoting a proactive security stance.
Impact on Financial Institutions' Cybersecurity Posture
The SWIFT CSCF has transformed financial institutions' cybersecurity strategies since its introduction. Institutions now implement mandatory controls to secure their networks, minimizing the risk of breaches. This includes strengthening access controls, improving data protection, and establishing effective incident response protocols.
Financial institutions benefit from the CSCF’s comprehensive approach, which mandates:
- Enhanced access control and monitoring systems
- Structured risk management and threat detection
- Regular security training for employees
The framework also boosts stakeholder confidence, increasing trust between customers, partners, and regulators. Institutions that adhere to CSCF standards are perceived as more reliable and secure, which directly enhances their reputation.
However, challenges persist, such as:
- Keeping up with evolving threats
- Implementing new controls amid budgetary or system constraints
Overall, the CSCF enables continuous improvement in cybersecurity posture, ensuring institutions remain resilient against emerging cyber risks.
SWIFT CSCF v2017: The Foundation of Global Financial Cybersecurity
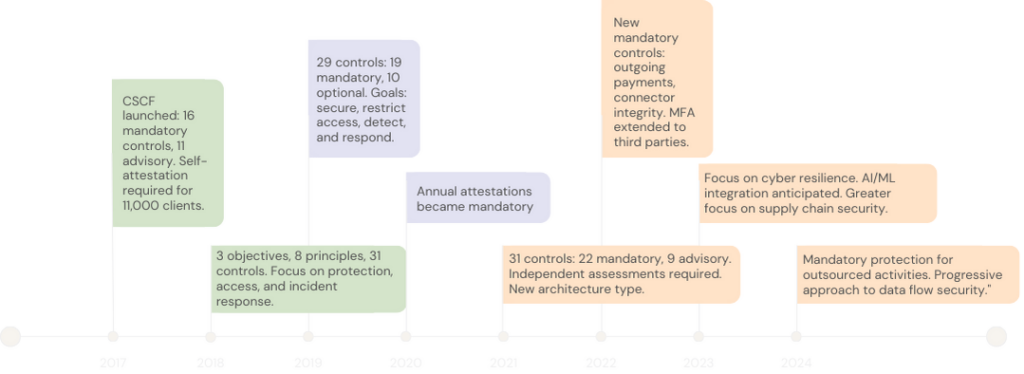
SWIFT CSCF v2017 marked the launch of the Customer Security Controls Framework, introduced in response to cyber incidents in 2016. This initial version included 16 mandatory and 11 advisory security controls. Notably, all 11,000 SWIFT customers were required to self-attest their compliance by December 31, 2017. The results of these attestations were then shared with their counterparts and relevant regulators.
Importantly, the mandatory controls set a foundational security standard across the SWIFT community. Every user, therefore, had to implement these controls on their local SWIFT infrastructure. On the other hand, advisory controls were based on recommended practices, which users were encouraged to adopt. Over time, some advisory controls could eventually become mandatory, depending on future risks, emerging technologies, or regulatory updates.
In addition, SWIFT CSCF v2017 laid the groundwork for the broader Customer Security Programme (CSP). Through this initiative, SWIFT aimed to improve security, prevent fraud, and enhance threat detection. Moreover, the CSP prioritized sharing information across the financial community, which, in turn, would help defend against future cyber threats. Overall, this version of the framework was a critical first step toward building a more secure global financial ecosystem.
SWIFT CSCF v2018: Structured Approach to Cybersecurity for Financial Institutions
The SWIFT Customer Security Controls Framework (CSCF) v2018 introduced a structured approach to safeguarding financial institutions against cyber threats. It established three core objectives: securing critical systems, managing access, and improving incident detection and response. These objectives were divided into eight principles and covered 31 security controls, including 16 mandatory and several advisory ones.
The CSCF v2018 focused on helping institutions protect their environments, restrict access, and quickly respond to anomalies. It required all SWIFT users to comply with the mandatory controls and submit annual attestations to confirm adherence. This process ensured that organizations maintained a minimum level of cybersecurity, protecting the SWIFT network.
Since its launch, the CSCF has been regularly updated to address the evolving cybersecurity landscape. The mandatory controls gradually increased, reflecting a stronger emphasis on proactive defense mechanisms. Independent assessments of compliance became mandatory in 2021, further enhancing the framework's rigor.
CSCF v2018 marked the beginning of a structured, systematic approach to cybersecurity for financial institutions. It laid the foundation for more advanced versions of the framework that have adapted to meet new and emerging threats in the financial sector.
SWIFT CSCF 2019-2020: Laying the Groundwork
SWIFT's Customer Security Controls Framework (CSCF) for 2019-2020 sets essential standards for safeguarding financial institutions. Focused on improving cybersecurity resilience, the framework outlines mandatory and advisory controls to protect against evolving threats.
Compliance with these controls is critical for financial organizations, helping them mitigate risk and ensure secure transactions. Furthermore, adherence to the CSCF demonstrates a commitment to global security standards, fostering trust across the SWIFT network. Implementing these guidelines strengthens overall defense strategies within financial cybersecurity departments.
Establishing Mandatory Controls
The establishment of mandatory controls has become a cornerstone in enhancing cybersecurity for financial institutions. This process began with the introduction of the SWIFT CSCF between 2019 and 2020.
| Control ID | Control Description | 2019 Status | 2020 Status | Key Changes |
|---|---|---|---|---|
| 1.1 | Secure your environment | Mandatory | Mandatory | No change |
| 1.2 | Protect your virtual environments | Advisory | Mandatory | Upgraded from advisory to mandatory |
| 1.3 | Security updates | Mandatory | Mandatory | No change |
| 1.4 | Restrict Internet access | Advisory | Advisory | No change |
| 2.1 | User access management | Mandatory | Mandatory | No change |
| 2.2 | Confidentiality and integrity of user sessions | Mandatory | Mandatory | No change |
| 2.3 | Multi-factor authentication | Mandatory | Mandatory | No change |
| 2.4 | Secure your applications | Advisory | Advisory | No change |
| 2.5 | Logging and monitoring | Mandatory | Mandatory | No change |
| 2.6 | Incident response | Mandatory | Mandatory | No change |
| 3.1 | Secure your infrastructure | Mandatory | Mandatory | No change |
| 3.2 | Protect against malware | Mandatory | Mandatory | No change |
| 3.3 | Secure your communications | Mandatory | Mandatory | No change |
| 3.4 | Secure your data | Advisory | Advisory | No change |
| 4.1 | Risk assessment | Mandatory | Mandatory | No change |
| 4.2 | Security awareness training | Mandatory | Mandatory | No change |
| 4.3 | Third-party risk management | Advisory | Advisory | No change |
| 4.4 | Compliance with regulations | Mandatory | Mandatory | No change |
Key Milestones
- 2019: Introduction of Controls: The 2019 version of the CSCF introduced 29 controls. Of these, 19 were mandatory, and 10 were optional. Compliance was required by December 31, 2019. The primary goal was to set a common security baseline for all SWIFT users, aiming for immediate security benefits and risk reduction.
- Control Objectives:
- Secure Your Environment: Ensures robust protection against threats.
- Know and Limit Access: Restricts and manages access to sensitive information.
- Detect and Respond: Enhances the ability to identify and address security incidents.
- 2020: Reinforcement and Transition: The 2020 version was delayed to 2021 due to the COVID-19 pandemic. It included minor improvements to facilitate user adaptation. Annual compliance attestations became mandatory, enhancing accountability and transparency within the SWIFT community.
Optional Controls and Their Significance
Between 2019 and 2020, the SWIFT Customer Security Controls Framework (CSCF) laid important groundwork for enhancing cybersecurity among financial institutions. This period marked a significant evolution in the framework, particularly concerning the introduction and significance of optional controls.
What are Optional Controls?
In the SWIFT CSCF, optional controls are recommended practices that extend beyond the foundational security measures. While mandatory controls set a necessary baseline, optional controls offer enhanced protection and adaptability to emerging threats.
Key Optional Controls Introduced by SWIFT CSCF
- Control 1.3A: Virtualization Platform Security
Ensures the security of virtual environments, addressing the growing reliance on virtualization within financial systems. - Control 2.10A: Application Hardening
Focuses on securing applications by minimizing vulnerabilities, crucial for maintaining software integrity. - Control 2.4A: Back Office Data Flow Security
Highlights the importance of securing data flows in back-office operations, essential for maintaining transaction accuracy.
Why Optional Controls Matter
- Enhanced Security Posture:
Optional controls provide additional layers of security, reinforcing defenses beyond the minimum requirements. - Adaptability to Evolving Threats:
They allow institutions to stay ahead of new vulnerabilities and attack vectors, adapting their security measures proactively. - Facilitating Compliance:
By implementing optional controls, institutions position themselves to meet future regulations and standards more effectively. - Promoting a Culture of Security:
Encourages a security-focused mindset across organizations, driving ongoing improvements in cybersecurity practices.
Incorporating optional controls from the SWIFT CSCF enhances the overall security framework of financial institutions. These measures not only provide advanced protection but also prepare institutions for future challenges, ensuring a robust response to the ever-evolving cyber threat landscape.
Industry Response to Initial Implementation
The launch of the SWIFT Customer Security Controls Framework (CSCF) triggered a substantial reaction across the financial sector. This response highlighted the pressing need for improved cybersecurity measures following a series of high-profile cyber incidents.

Key Industry Reactions:
- Adoption of Security Controls:
Financial institutions swiftly recognized the necessity to implement the CSCF’s mandatory controls. This framework set a fundamental standard for security measures, resulting in widespread upgrades in protecting sensitive data, managing access controls, and monitoring suspicious activities. - Independent Assessments:
Institutions are now required to undergo mandatory independent assessments conducted by SWIFT CSP Assessment Experts for Financial Security, such as those from Intervalle Technologies, to confirm their adherence to CSCF requirements. This shift towards third-party evaluations highlights a renewed commitment to transparency and accountability in cybersecurity practices, addressing the growing demands of the technology landscape. - Increased Collaboration:
The CSCF spurred greater cooperation among financial institutions. Organizations began exchanging best practices and implementation experiences, fostering a more secure financial ecosystem through collective security enhancements. - Investment in Cybersecurity:
The framework drove many institutions to boost their investments in cybersecurity technologies and resources. Compliance necessitated policy adjustments and technological upgrades, including advanced firewalls, intrusion detection systems, and enhanced employee training programs. - Focus on Continuous Improvement:
Regular updates to the CSCF encouraged a culture of ongoing improvement. Institutions adopted a perspective of continuous compliance, establishing stronger security cultures. - Regulatory Alignment:
CSCF’s alignment with standards like NIST and ISO 27001 eased the compliance process for institutions familiar with these frameworks. This integration streamlined the adoption of CSCF into existing risk management programs.
In conclusion, the initial CSCF implementation marked a critical shift for the financial industry. It led to advanced security measures, enhanced collaboration, and a reinforced focus on accountability and continuous improvement. This evolution not only strengthened defenses against cyber threats but also contributed to a more secure financial environment.
The Transformation of SWIFT CSCF 2021
In 2021, the SWIFT Customer Security Controls Framework (CSCF) underwent a substantial transformation, aimed at enhancing cybersecurity for financial institutions. This update was critical in addressing rising cyber threats and fortifying the security posture of SWIFT users. The cyber landscape has become increasingly hostile, with a 238% increase in attacks on financial institutions reported in early 2020. The average cost of a data breach in this sector was $5.72 million in 2021, according to IBM and the Ponemon Institute.
| Control ID | Control Name | 2020 Status | 2021 Status | Description of Change |
|---|---|---|---|---|
| 1.1 | Internet Access Restriction | Advisory | Mandatory | Promoted to mandatory control. |
| 1.2 | Multi-Factor Authentication | Mandatory | Mandatory | No change. |
| 1.3 | Secure Configuration of SWIFT Infrastructure | Mandatory | Mandatory | No change. |
| 1.4 | Restricted Internet Access | Advisory | Mandatory | Newly introduced mandatory control. |
| 2.1 | Internal Data Flow Security | Mandatory | Mandatory | No change. |
| 2.2 | Security Updates | Mandatory | Mandatory | No change. |
| 2.3 | System Hardening | Mandatory | Mandatory | No change. |
| 2.4 | Back Office Data Flow Security | Advisory | Advisory | No change. |
| 2.5 | Data Protection | Mandatory | Mandatory | No change. |
| 2.6 | Access Control | Mandatory | Mandatory | No change. |
| 2.7 | Monitoring and Logging | Mandatory | Mandatory | No change. |
| 2.8 | Outsourced Critical Activity Protection | Advisory | Advisory | No change. |
| 2.9 | Transaction Business Controls | Mandatory | Mandatory | No change. |
| 3.1 | Physical Security | Mandatory | Mandatory | No change. |
| 3.2 | Secure Token Management | Mandatory | Mandatory | No change. |
| 4.1 | Incident Response Management | Mandatory | Mandatory | No change. |
| 5.1 | Security Awareness Training | Mandatory | Mandatory | No change. |
| 5.2 | Token Management | Mandatory | Mandatory | No change. |
| 6.1 | Software Integrity | Mandatory | Mandatory | No change. |
| 6.2 | Software Updates | Mandatory | Mandatory | No change. |
| 6.3 | Vulnerability Management | Mandatory | Mandatory | No change. |
| 6.4 | Logging and Monitoring | Mandatory | Mandatory | No change. |
| 7.1 | Risk Assessment | Mandatory | Mandatory | No change. |
| 7.2 | Scenario-based Risk Assessment | Advisory | Advisory | No change. |
| 7.3 | Independent Assessment | Not applicable | Mandatory | New requirement for independent assessment introduced. |
Key Changes in SWIFT CSCF 2021
- Increase in Control Count:
The 2021 version expanded the framework to 31 controls, comprising 22 mandatory and 9 advisory controls. This increase underscores SWIFT's commitment to addressing emerging security challenges and ensuring comprehensive protection for its users.
- Mandatory Independent Assessments:
A significant change was the requirement for institutions to undergo annual independent assessments to validate compliance with the CSCF. This shift from self-attestation to independent evaluation enhances accountability and ensures that institutions are genuinely adhering to the required security measures.
- Promotion of Advisory Control to Mandatory:
Control 1.4, which focuses on the restriction of internet access, was promoted from advisory to mandatory. This control mandates that internet access is limited to only what is necessary for business functions, thereby reducing potential attack surfaces.
- Expanded Scope of Multi-Factor Authentication (MFA):
Control 4.2 was updated to require MFA not only for internal applications but also for SWIFT-related applications and components operated by third-party service providers. This change emphasizes the importance of securing access points across all environments.
- Introduction of a New Architecture Type:
The 2021 framework introduced a fifth architecture type, A4 – Customer Connector, which allows institutions to utilize application programming interfaces (APIs) for direct connections to SWIFT services. This addition reflects the growing trend towards integration and digitalization within the financial sector.
- Emphasis on Data Flow Security:
Control 2.4A, concerning back-office data flow security, remains advisory but is highlighted for future mandatory implementation. This control encourages institutions to assess and secure their internal data flows, recognizing the criticality of data integrity in financial transactions.
Industry Reception
The financial industry responded positively to the CSCF 2021 changes:
- Enhanced Compliance Efforts:
Institutions increased their compliance activities, investing in technology and resources to meet the new standards. - Increased Collaboration:
The need for independent assessments fostered greater industry collaboration, with organizations sharing best practices. - Commitment to Continuous Improvement:
The evolving framework encouraged institutions to view compliance as an ongoing process rather than a one-time effort.
The 2021 transformation of the SWIFT CSCF represents a significant advancement in cybersecurity for financial institutions. By introducing new controls, emphasizing independent assessments, and adapting to technological changes, SWIFT aims to enhance the security of financial transactions and address emerging cyber threats.
SWIFT CSP Controls: Evolving Security Measures in 2022
The SWIFT Customer Security Programme (CSP) and its Customer Security Controls Framework (CSCF) have significantly evolved in 2022. This evolution addresses the dynamic cybersecurity landscape and strengthens the security of financial institutions. The updated controls aim to enhance protection against emerging threats and ensure compliance within the SWIFT ecosystem. Consequently, financial institutions must adapt to these changes to maintain robust security measures and effectively counteract potential risks in their operations.
| Control Number | Control Description | CSCF 2021 Status | CSCF 2022 Status | Key Changes/Notes |
|---|---|---|---|---|
| 1.1 | Secure your environment | Mandatory | Mandatory | No change. |
| 1.2 | Know and limit access | Mandatory | Mandatory | No change. |
| 1.3 | Detect and respond | Mandatory | Mandatory | No change. |
| 2.1 | Access control policy | Mandatory | Mandatory | No change. |
| 2.9 | User access management | Mandatory | Mandatory | Updated to include more detailed requirements for user access management. |
| 3.1 | Security awareness training | Mandatory | Mandatory | No change. |
| 3.2 | Security incident management | Mandatory | Mandatory | No change. |
| 4.1 | Vulnerability management | Mandatory | Mandatory | No change. |
| 5.1 | Security testing and assessment | Mandatory | Mandatory | No change. |
| 6.1 | Incident response planning | Mandatory | Mandatory | No change. |
| 6.2 | Incident response team | Mandatory | Advisory | Changed from mandatory to advisory, suggesting flexibility in team structure. |
| 6.3 | Information sharing | Mandatory | Advisory | Changed from mandatory to advisory, allowing for more discretion in practices. |
| 7.1 | Security policies and procedures | Mandatory | Mandatory | No change. |
| 7.2 | Compliance with regulatory requirements | Mandatory | Mandatory | No change. |
Key Updates in the SWIFT CSP 2022 Controls
The SWIFT Customer Security Controls Framework (CSCF) 2022 introduces significant updates to enhance security for financial institutions. Here are the key updates:
New Mandatory Controls:
- Control 2.11: Outbound Payment Controls
This control focuses on detecting and preventing fraudulent outbound transactions. It aims to reduce financial losses by tightening transaction monitoring. - Control 2.12: Customer Connector Integrity
This update strengthens the security of file transfer solutions and middleware systems used in SWIFT communication, ensuring data integrity and confidentiality.
Promotion of Advisory Controls to Mandatory:
- Control 1.4: Restriction of Internet Access
This control restricts internet access to only what is essential for business functions. It reduces potential attack surfaces by limiting unnecessary exposure.
Expanded Scope of Existing Controls:
- Control 4.2: Multi-Factor Authentication (MFA)
MFA is now required for accessing SWIFT-related applications or components managed by third-party service providers. This enhances security by adding an additional layer of verification.
Alignment with Industry Standards:
- The CSCF continues to align with established security standards such as NIST, ISO 27001, and PCI-DSS. This ensures that SWIFT’s controls remain consistent with best practices in the industry.
These updates reflect a commitment to improving security and staying aligned with evolving industry standards.
SWIFT CSCF 2023: Preparing for the Future
The SWIFT Customer Security Controls Framework (CSCF) 2023 introduces key updates to strengthen financial institutions' cybersecurity. With evolving threats, these enhancements aim to protect the SWIFT infrastructure. Mandatory and advisory controls help financial organizations stay compliant and prepared for emerging risks. By implementing the CSCF 2023, institutions enhance their security posture and maintain regulatory adherence. This proactive approach is crucial in securing the financial ecosystem and preparing for future challenges in cybersecurity. Stay ahead, adapt, and protect your organization's SWIFT environment.
| Control Number | Control Name | 2022 Status | 2023 Status | Key Changes/Notes |
|---|---|---|---|---|
| 1.1 | Secure Your Environment | Mandatory | Mandatory | No significant changes noted. |
| 1.2 | Know and Limit Access | Mandatory | Mandatory | No significant changes noted. |
| 1.3 | Detect and Respond | Mandatory | Mandatory | No significant changes noted. |
| 2.1 | Internal Data Flow Security | Mandatory | Mandatory | Clarifications added regarding risk drivers shared with control 2.4. |
| 2.2 | Security Updates | Mandatory | Mandatory | Wording regarding software integrity checks aligned with control 6.2. |
| 2.3 | System Hardening | Mandatory | Mandatory | USB protection guidance fully incorporated; application allowlisting moved from controls 1.1, 1.5, and 6.2. |
| 2.4 | Back Office Data Flow Security | Advisory | Advisory | Control remains advisory; recommendations to identify security posture of data flows introduced. |
| 2.4A | Back Office Data Flow Security | N/A | Advisory | New control introduced with recommendations for securing data flow exchange. |
| 2.8 | Outsourced Critical Activity Protection | Advisory | Mandatory | Control promoted to mandatory status, with clarifications provided. |
| 2.9 | Transaction Business Controls | Advisory | Advisory | Explicit mention that business controls can be performed outside the secure zone. |
| 3.1 | Physical Security | Mandatory | Mandatory | Recommendations on sanitization of disposed or reassigned equipment added. |
| 5.2 | Token Management | Mandatory | Mandatory | Wording on supervision and secure storage of tokens aligned with control 3.1. |
| 6.2 | Software Integrity | Mandatory | Mandatory | Alignment of wording with control 2.2 regarding software integrity checks. |
| 6.4 | Logging and Monitoring | Mandatory | Mandatory | References to control 6.4 included in other relevant controls requiring log monitoring. |
| 7.4 | Scenario-based Risk Assessment | Advisory | Advisory | Explicit mention of reliance on external assessments included. |
Anticipating Cybersecurity Trends
By understanding emerging risks, organizations can strengthen their defenses and protect critical assets. Regular threat assessments, paired with real-time data analysis, enable proactive responses to potential attacks. Moreover, keeping up with the latest trends helps cybersecurity teams to adjust strategies, ensuring long-term resilience.
Increased Focus on Cyber Resilience
The 2023 updates emphasize the need for financial institutions to build resilience against cyber threats. This includes not only preventing attacks but also ensuring that institutions can quickly recover and maintain operations in the event of a security breach.
Integration of Advanced Technologies
The framework anticipates the integration of advanced technologies such as artificial intelligence (AI) and machine learning (ML) in threat detection and response mechanisms. These technologies can enhance the ability to identify anomalies and respond to incidents more effectively.
Emphasis on Supply Chain Security
With the rise in third-party services and outsourcing, there is a growing focus on securing supply chains. The 2023 CSCF includes controls aimed at ensuring that third-party vendors adhere to the same security standards as the financial institutions themselves.
The Latest Iteration: SWIFT CSCF v2024
The SWIFT Customer Security Controls Framework (CSCF) v2024 continues to evolve in response to the changing cybersecurity landscape, incorporating best practices and addressing emerging threats. Here are the key features and updates associated with the 2024 version:
| Control Number | Description | 2023 Status | 2024 Status | Key Changes/Notes |
|---|---|---|---|---|
| 1.1 | Secure your environment | Mandatory | Mandatory | No changes noted. |
| 1.2 | Know and limit access | Mandatory | Mandatory | No changes noted. |
| 1.3 | Detect and respond | Mandatory | Mandatory | No changes noted. |
| 2.1 | Security awareness and training | Mandatory | Mandatory | No changes noted. |
| 2.2 | Access control | Mandatory | Mandatory | No changes noted. |
| 2.3 | Secure configuration | Mandatory | Mandatory | No changes noted. |
| 2.4 | Phased promotion of back office data flow security | Advisory | Advisory | Encouraged early identification and securing of back-office data flows. |
| 2.8 | Outsourced critical activity protection | Advisory | Mandatory | This control has been made mandatory to address the rise in outsourcing and cloud services. |
| 3.1 | Incident management | Mandatory | Mandatory | No changes noted. |
| 3.2 | Logging and monitoring | Mandatory | Mandatory | Enhanced integration with other controls for better monitoring. |
| 6.4 | Logging and monitoring | Advisory | Mandatory | Logging and monitoring are now integrated more explicitly across other controls. |
| 7.4 | Scenario-based risk assessment | Advisory | Mandatory | Acknowledges the use of existing information security risk management processes. |
Key Features of SWIFT CSCF v2024
Incremental Updates of SWIFT CSCF
The 2024 version builds on the previous year's framework, introducing refinements and clarifications to existing controls rather than a complete overhaul. This approach allows institutions to adapt gradually while maintaining compliance with security standards and ensuring they meet the requirements for SWIFT attestation.
Mandatory Control on Outsourced Critical Activity Protection
In response to the increasing trend of outsourcing and cloud services, Control 2.8, which focuses on the protection of outsourced critical activities, has been made mandatory. This control emphasizes the need for institutions to ensure that third-party service providers adhere to the same security standards as the institutions themselves.
Phased Approach for Back Office Data Flow Security
Control 2.4A regarding back-office data flow security remains advisory but is emphasized for institutions to identify and assess their data flows and security postures. This phased approach aims to prepare users for potential future mandatory requirements.
Clarifications and Enhancements
The framework includes various minor updates aimed at improving usability and comprehension, such as:
- Aligning the Scope of Security Controls section with expectations for non-SWIFT systems.
- Corrections and clarifications in the control statements and risk driver summary matrix, ensuring clearer guidance for implementation.
Addressing Emerging Threats and Vulnerabilities
Focus on Cyber Resilience
The updates reflect a broader emphasis on building cyber resilience among financial institutions, ensuring they can withstand and recover from cyber incidents effectively.
Incorporating Feedback from the Industry
The CSCF Working Group has evaluated numerous change requests from the user community, integrating feedback to enhance the framework's relevance and effectiveness in addressing current cybersecurity challenges.
Adaptation to Technological Advancements
The framework continues to adapt to technological changes, ensuring that security controls remain effective against new vulnerabilities associated with advancements such as cloud computing and API integrations.
Aligning with Global Financial Security Standards
Harmonization with Industry Best Practices
The SWIFT CSCF v2024 aligns with international standards and best practices, ensuring that SWIFT users are compliant with recognized security frameworks and regulations, such as those established by the Financial Action Task Force (FATF).
Continuous Improvement
The ongoing refinement process of the CSCF ensures that the framework remains effective against evolving cyber threats, helping institutions stay ahead of cybercriminals.
Training and Awareness
The updates emphasize the importance of ongoing training and awareness programs for employees, fostering a culture of security within organizations.
The SWIFT CSCF v2024 represents a crucial step in enhancing the cybersecurity posture of financial institutions. By introducing mandatory controls, refining existing guidelines, and addressing emerging threats, SWIFT aims to empower its users to navigate the complex landscape of cybersecurity effectively.
The ongoing evolution of the framework underscores the commitment to maintaining a secure and resilient financial ecosystem, ensuring that institutions are well-equipped to protect sensitive data and transactions against cyber threats.



