ISMS: A Comprehensive Guide for Successful and Compliant Implementation
By deploying a robust and compliant Information Security Management System (ISMS), you'll contribute to safeguarding your organisation's vital information assets. Are you ready to become the true ambassadors of security within your organisations? With the rapid surge in cyber threats, your role has never been more crucial.
ISMS: The Key to Demonstrating Risk Management and IT Governance Expertise
This strategic approach will enable you to showcase your competencies in risk management and IT governance. A major asset for taking on new challenges and advancing your career. But beyond that, it's the very future of your organisations that you'll secure by offering them a decisive competitive advantage: the reinforced trust of their stakeholders.
What Are You Waiting For? Propel Your Enterprise Towards Information Security Excellence
What are you waiting for to propel your enterprise towards information security excellence? Discover in this guide the 8 essential steps to deploy a high-performing ISMS, certified to ISO 27001 and compliant with the Algerian National Information Security Framework (RNSI 2020).
ISMS Definition
An Information Security Management System (ISMS) is a set of policies, processes, tools, and strategies aimed at ensuring the confidentiality, integrity, and availability of an organisation's data. By clearly defining responsibilities and deploying appropriate security measures, the ISMS allows for the control of risks related to data.
The Three Pillars of ISMS: Availability, Integrity, and Confidentiality
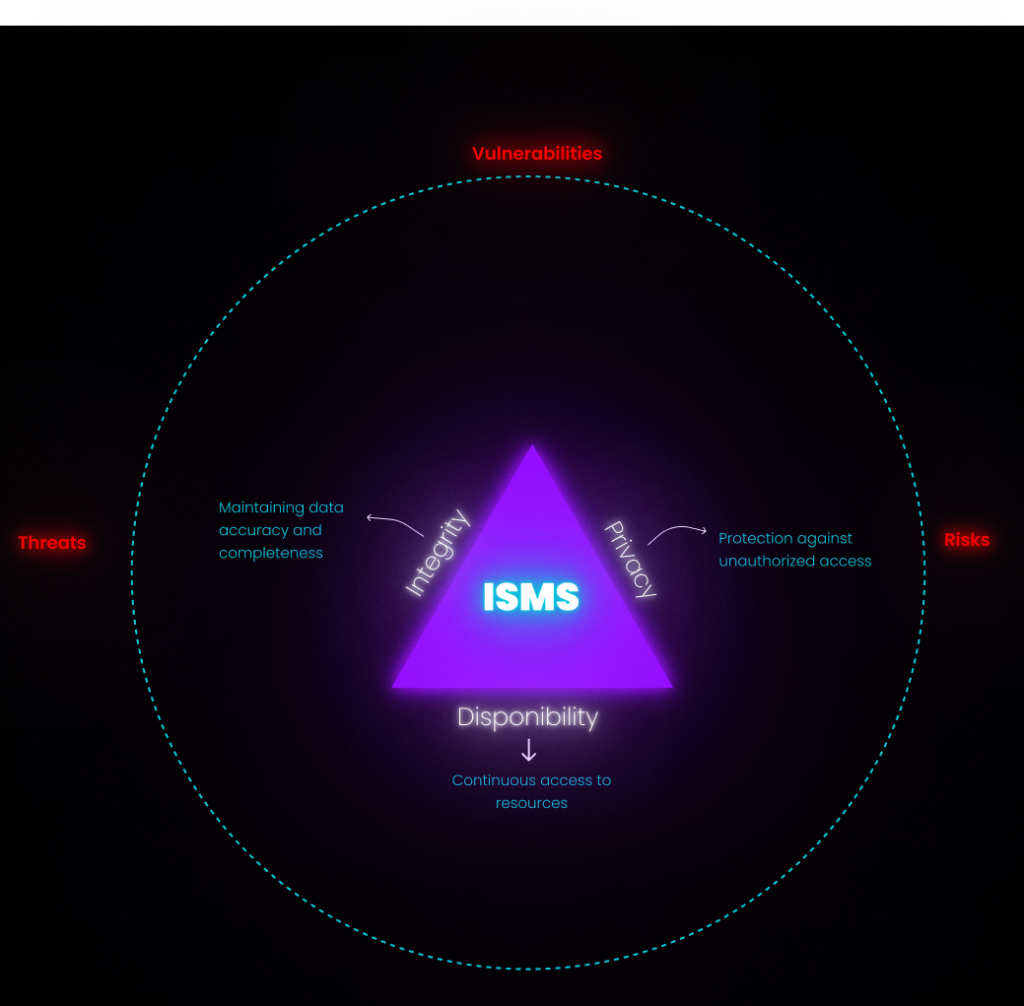
This comprehensive approach takes into account human factors, technological aspects, and the organisation's business processes. The effectiveness of an ISMS relies on the harmonious combination of technical and organisational controls.
International and National Standards for ISMS
The ISO/IEC 27001 standard establishes an internationally recognised framework specifying the requirements for ISMS. It provides detailed guidelines for the implementation, operation, monitoring, review, and continuous improvement of the system. The ISMS generally follows the Plan-Do-Check-Act (PDCA) cycle to ensure ongoing optimisation.
At the national level in Algeria, the National Information Security Framework (RNSI 2020) aims to establish a common and harmonised approach to information security management. It applies, in particular, to government agencies, public sectors, and infrastructures hosting sensitive data within the national territory.
The History of Information Security Management Systems
Concern for the security of information systems is not new. For a long time, the protection of strategic and military data has been a crucial issue.
Early Developments in the United States
As a forerunner in this field, the United States Department of Defense (DoD) published the Trusted Computer System Evaluation Criteria (TCSEC) in 1983, a seminal work that laid the foundations for information security. Concepts such as multi-level security and defence in depth, inspired by ancient military practices, remain highly relevant today. They aim to secure each component of a system by establishing robust defensive barriers.
Pioneering Legislation in France and the European Union
In the 1990s, the serious consequences of poor personal data security led to the adoption of pioneering legislation, such as the French Data Protection Act (Loi Informatique et Libertés). A growing awareness emerged. Continuing these efforts, the French National Cybersecurity Agency (ANSSI) promoted the structuring principles of defence in depth to strengthen cybersecurity in 2001.
In 2016, the European Union adopted the NIS Directive, aimed at harmonising and improving the security of critical information systems within its territory.
The Rise of ISO 27001 and the Algerian RNSI 2020
Published in 2005, the ISO/IEC 27001 standard quickly became the international reference for information security management. This standard establishes a rigorous framework of requirements for the implementation and ongoing operation of an Information Security Management System (ISMS) within organisations.
In this context, the Algerian government developed and ratified its own National Information Security Framework (RNSI 2020). Driven by the Ministry of Post, Telecommunications, Technologies, and Digital, the RNSI 2020 establishes a harmonised approach to security management in public administration and infrastructures hosting sensitive data within the national territory.
Today, the security of information systems is a major issue for organisations, which must mobilise a range of technical, organisational, legal, and human measures. Implementing an ISMS has become essential to prevent cyber attacks and ensure the trust of users and customers.
Conducting an ISMS Opportunity Study
Before implementing an ISMS, it is essential to conduct a thorough opportunity study. This will lay the solid foundations for the project. First, create an exhaustive inventory of the existing security mechanisms within your organisation. Then, identify all stakeholders involved in the ISMS, whether internal departments or external partners. Analyse their specific needs, expectations, and issues related to information security.
To ensure strategic alignment from the outset, formally validate this opportunity study with top management. Their support and commitment will be key success factors.
Choosing the Right Scope for Your Information Security Management System
Once the opportunity has been validated, the second crucial step is to precisely determine the scope of the ISMS. In other words, clearly define the activities, business processes, and domains that will be covered by the management system. However, some exclusions may be justified depending on the context and priorities of your organisation. In this case, rigorously document the reasons for these exclusions. An overly broad or ill-defined scope will increase the risk of project failure.
Adopt a step-by-step approach, addressing first the priority issues related to your core business and critical information assets.
Defining the ISMS Security Strategy
The third step is to formally establish the security strategy in a statement of intent. This strategic document should clarify the directions, guiding principles, and objectives for information security within your organisation. Additionally, an approved and signed Information Systems Security Policy (PSSI) by top management should be established. This policy defines the overall framework for security management.
The statement of intent and the PSSI will formalise your organisation's commitment to information security at all levels.
Conducting a Risk Analysis
Risk analysis represents the fourth step, at the heart of successful ISMS deployment. Its objective is to identify, assess, and prioritise all potential risks related to information security within the defined scope. Begin by comprehensively identifying risk sources such as security flaws, human errors, cyber attacks, unauthorised access, etc.
Subsequently, examine their underlying causes as well as potential consequences and impacts. Choose a recognised and context-appropriate risk analysis methodology, such as EBIOS, MEHARI, or ISO 27005. These proven frameworks will guide you through the analysis.
Estimating Risk Impact and Probability
Once the risks have been identified, you must proceed with their precise evaluation. For each risk, analyse its potential impact on the confidentiality, integrity, and availability of information assets. Then, estimate its probability of occurrence by considering factors such as threats, vulnerabilities, and existing protection levels. A risk assessment matrix will allow you to classify each risk according to predefined criticality levels to prioritise them.
Do not omit involving business stakeholders and subject matter experts during this crucial phase. Their vision and experience will provide a comprehensive perspective.
Defining Security Objectives
Based on the analysed and prioritised risks, you can now establish specific security objectives to be achieved within the ISMS framework. These objectives will define the priorities and guide the treatment plan to reduce major risks to an acceptable level.
Formulate SMART (Specific, Measurable, Achievable, Realistic, and Time-bound) objectives. Furthermore, to ensure monitoring, establish a dedicated committee with all relevant stakeholders. Regular committee meetings will allow for progress evaluation, resolution of potential roadblocks, and optimisation of the implementation of security measures.
Implementing ISMS Security Measures
The definition and deployment of concrete security measures to address identified risks. These measures combine technical controls (firewalls, antivirus, encryption, etc.) and organisational controls (policies, procedures, training).
Prioritise measures based on objectives and following the best practices outlined in Annex A of ISO 27001, which covers 14 domains ranging from physical security to incident management, as well as the 20 domains covered by the RNSI 2020.
In parallel, formalise all ISMS-related documentation (PSSI, policies, procedures, contingency/recovery plans, registers, etc.) in accordance with the requirements.
The 20 Domains of the RNSI 2020 for a Robust ISMS
The RNSI 2020 in Algeria defines 20 key domains of information security. For each domain, specific requirements and best practices are detailed. Here are the 20 domains and their definitions for a thorough understanding of the national framework:
Asset Management
Identify, classify and protect information assets.
Personal Data Protection
Ensure the confidentiality and integrity of personal data.
Access Control and Management
Control and monitor access to systems and data.
Communications Security
Secure information exchanges.
Cryptography
Apply encryption measures to protect sensitive data.
Information Systems Security
Protect systems against cyber threats.
Cloud Security
Secure information stored and processed via cloud services.
Security Incident Management
Detect, respond to and report security incidents.
Business Continuity
Ensure the availability of critical systems in case of an incident.
Compliance
Comply with legal and regulatory security requirements.
Industrial Information Systems Security
Protect industrial control systems.
Mobile Information Systems Security
Secure the use of mobile devices.
Embedded Information Systems Security
Secure embedded systems.
Telemedicine Information Systems Security
Secure telemedicine systems.
Internet of Things Information Systems Security
Secure connected objects.
Artificial Intelligence Information Systems Security
Secure AI systems.
Cloud Usage Governance
Define a strategy for the use of cloud services.
Cloud Services Security
Ensure that cybersecurity risks related to cloud services are controlled.
Cryptographic Services Management
Apply cryptographic security measures to protect the organisation's assets.
Encrypted Content Analysis
Consider the impact of information encryption on content analysis.
Annex A Domains of ISO 27001
Annex A of the ISO 27001 standard defines 14 key domains to cover for comprehensive information security management. Each domain includes a series of security controls to implement. Here is an overview of these 14 domains with some examples of associated controls:
Information Security Policies
PSSI, regular reviews, regulatory compliance.
Information Security Organisation
Protect systems against cyber threats.
Human Resources Security
Employee screening, awareness, definition of roles and responsibilities.
Asset Management
Asset inventory, rules for asset use and handling.
Access Control
Access control policies, access rights management, strong authentication.
Cryptography
Policies for using cryptographic controls, key management.
Physical and Environmental Security
Physical access controls, protection against external threats.
Operational Security
Operational documentation, malware protection, backup.
Communications Security
Secure networks, transfer policies, confidentiality agreements.
Acquisition, Development and Maintenance
Secure development, test data, secure environments.
Supplier Relationships
Supplier security policy, secure supply chain.
Information Security Incident Management
Incident management procedures, evidence collection.
Business Continuity Management
Continuity plan, regular testing.
Compliance
Compliance review, intellectual property.
Carefully analyse each domain and select appropriate controls based on your risk analysis and defined objectives. Then, define how to implement them with detailed action plans.
ISMS Training and Awareness
An essential component for the success of an ISMS is training and raising awareness among all stakeholders, especially employees. Indeed, human errors often represent the weakest link in security.
Organise tailored training sessions to explain the stakes, policies, and procedures to follow for different levels and roles. Regularly raise awareness about risks such as social engineering, malicious web browsing, or information leaks.
Involve teams on an ongoing basis by appointing ISMS ambassadors and organising challenges to stimulate their vigilance.
Communicating About the ISMS
Beyond training, regular communication about the ISMS is essential to maintain an adequate level of awareness. Use various channels to disseminate key messages, promote best practices, and share lessons learned.
Dedicated newsletters, information meetings, an intranet page, or awareness campaigns will keep all employees sustainably informed.
In conclusion, communication should also target relevant external partners such as suppliers and subcontractors to involve them in the process.
Monitoring and Continuous Improvement
The ultimate step to ensuring the ISMS's effectiveness over time is to establish a cycle of monitoring and continuous improvement.
Start by defining Key Performance Indicators (KPIs) related to security. These metrics will allow you to monitor, measure, and analyse the results obtained. Some examples of KPIs include policy compliance rate, number of incidents detected, incident resolution times, number of vulnerabilities identified, etc.
Schedule internal and external security audits at regular intervals to detect non-conformities and opportunities for optimisation.
Continuous Improvement Process
Based on the analysis of KPIs and audit results, you can then define and implement corrective actions to resolve identified issues, as well as preventive actions to avoid their recurrence. Regularly review the ISMS policies, procedures, and controls to optimise them and keep up with evolving threats and regulatory requirements.
ISO 27001 Certification
While the RNSI introduces specific domains related to the Algerian context and provides more details, it remains closely aligned with ISO 27001. An organisation seeking to comply with the RNSI can build upon the solid foundations of ISO 27001 while integrating the national framework's specificities.
Finally, once all steps have been completed, you can also consider pursuing ISO 27001 certification. Although not mandatory, this internationally recognised standard will bring numerous benefits, such as credibility, enhanced stakeholder trust, and facilitated access to certain markets.
An accredited certification body will conduct an in-depth audit to validate the compliance of your ISMS before issuing the coveted certification.
Keep in mind that certification is not an end in itself but rather a milestone in the continuous process of improving security.
By rigorously following these 8 detailed steps and relying on best practices, you will be able to successfully deploy a robust, compliant, and sustainable ISMS within your organisation. Do not hesitate to seek our experts' assistance if needed to guide you through this strategic endeavour.



