Zero Day Attack: The Ultimate Guide to Defense
A zero day attack is a cyber intrusion that exploits a previously unknown software vulnerability. The term "zero-day" signifies a critical reality. Vendors have zero days to release a patch before attackers can act.
This creates a dangerous window of opportunity for threat actors. Organizations are left exposed and unprepared for the ensuing breach.
For CISOs, SOC managers, and IT directors, this threat is a top concern. It bypasses traditional, signature-based security controls with ease.
The financial and reputational damage from such an attack can be immense. Attackers can deploy ransomware, exfiltrate sensitive data, or disrupt critical operations. Because the vulnerability is unknown, standard defenses often fail.
This makes detection and response incredibly challenging. Security teams must shift their focus from prevention alone.
They need a more resilient and proactive security posture. This requires a deep understanding of the threat.
This comprehensive guide provides that understanding. We will explore the technical mechanics of a zero day attack. We will also analyze the modern threat landscape.
Most importantly, this article offers actionable frameworks for defense. You will learn strategies for proactive vulnerability discovery.
We will also cover real-time threat detection and architectural resilience. This information will empower you to fortify your organization against these advanced threats.
The Challenge of the Zero Day Attack

The modern zero day attack landscape is more dangerous than ever. Threat actors are better funded and more sophisticated. The digital transformation of businesses has also expanded the attack surface.
This creates more potential entry points for attackers to exploit. Security leaders face a constant battle against these unknown threats. Understanding this environment is the first step toward building a robust defense.
The frequency of these attacks is increasing at an alarming rate. Google's Threat Analysis Group (TAG) reported 97 zero-day vulnerabilities exploited in the wild in 2023. While this was a drop from 2021's record high, it was still the second-highest number ever recorded.
This trend highlights a persistent and growing danger. Attackers are actively searching for and weaponizing new flaws.
This escalation is driven by several factors. Software complexity has grown exponentially. More code means more potential for hidden bugs.
The proliferation of IoT devices and cloud services also introduces new vectors. Many of these systems are not built with security as a priority.
This makes them fertile ground for undiscovered vulnerabilities. Consequently, security teams must defend a larger, more fragmented perimeter.
The Escalating Frequency of Zero-Day Exploits

The rise in zero-day exploits is not a random occurrence. It is a direct result of market dynamics and technological shifts. The value of a reliable zero-day exploit has skyrocketed.
This has created a lucrative market on the dark web. Cybercriminal groups and nation-state actors are willing to pay millions for exclusive access. This financial incentive fuels a global industry of vulnerability research and exploit development.
Furthermore, the rise of "exploit-as-a-service" platforms has democratized these attacks. Less sophisticated actors can now purchase or lease the tools needed to launch a zero day attack. This lowers the barrier to entry for high-impact cybercrime.
It also increases the volume of threats organizations must face. The same vulnerability can be used by multiple groups for different motives.
The interconnectedness of modern supply chains presents another major risk. A single zero-day vulnerability in a widely used software library can have a cascading effect. The Log4Shell incident is a prime example.
A flaw in a popular Java logging tool exposed millions of applications worldwide. This supply chain risk means organizations can be vulnerable. They are at risk even if their own code is secure.
High-Profile Actors and the Zero-Day Marketplace
The actors behind the modern zero day attack are diverse. They range from organized cybercrime syndicates to state-sponsored hacking groups. Nation-state actors often stockpile zero-day vulnerabilities.
They use them for espionage, intelligence gathering, and cyber warfare. The Stuxnet worm, which targeted Iranian nuclear facilities, famously used four separate zero-day exploits. This demonstrated the strategic value of these undisclosed flaws.
Cybercrime groups use zero-day exploits for financial gain. They are often the first step in a ransomware attack or a major data breach. For example, a zero day attack on a file transfer application can lead to massive data exfiltration.
The attackers then extort their victims for money. These groups are highly professional. They operate like legitimate businesses with development teams and customer support.
A gray market also exists where private companies develop and sell exploits. These firms, known as vulnerability brokers, sell their findings to government agencies. This practice is controversial.
Critics argue that it keeps vulnerabilities secret from the vendors who could fix them. This leaves the public exposed.
Proponents claim it is a necessary tool for national security. Regardless, it contributes to the proliferation of powerful cyber weapons.
Root Causes and Technical Factors
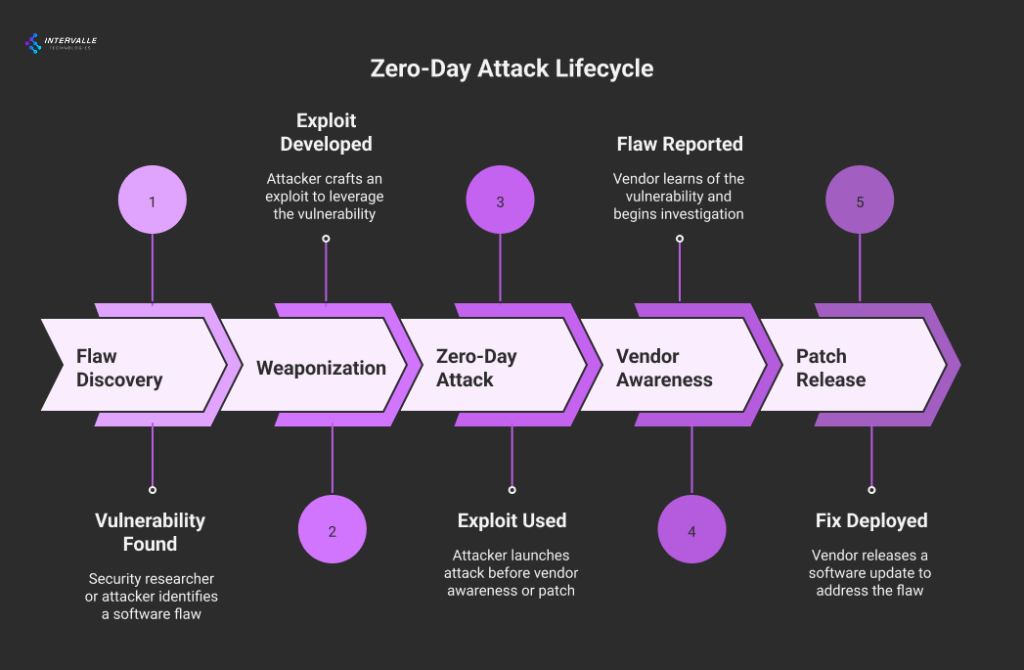
To defend against a zero day attack, one must understand its technical underpinnings. These attacks do not materialize out of thin air. They are the result of a specific lifecycle.
It begins with the discovery of a flaw and ends with its weaponization. The vulnerabilities themselves also fall into common categories. Understanding these patterns helps security teams anticipate and mitigate potential threats more effectively.
The core issue is inherent human error in software development. No complex piece of software is perfect. Developers, under pressure to meet deadlines, can make mistakes.
These mistakes can create security flaws. Common errors include improper input validation, memory management issues, or weak access controls.
Threat actors are experts at finding and exploiting these subtle errors. They use advanced tools and techniques to analyze code for weaknesses.
A zero-day vulnerability represents a gap in a vendor's security knowledge. The vendor is unaware the flaw exists. Therefore, no patch or mitigation advice is available.
This information asymmetry gives the attacker a significant advantage. The defender is always playing catch-up.
This is the fundamental challenge that makes a zero day attack so difficult to stop. The focus must be on resilience rather than perfect prevention.
The Vulnerability Lifecycle: From Discovery to Weaponization
Every zero day attack follows a predictable lifecycle. The first stage is discovery. A security researcher, a hacker, or an internal developer finds a new vulnerability.
If a "white hat" researcher finds it, they will typically report it to the vendor. This is known as responsible disclosure. This allows the vendor to develop a patch before the flaw becomes public knowledge.
The second stage is exploit development. If a malicious actor discovers the flaw, they will try to write code to exploit it. This "exploit" is a program designed to trigger the vulnerability.
It allows the attacker to gain control, escalate privileges, or exfiltrate data. Developing a reliable exploit can be a complex and time-consuming process. It often requires deep technical expertise.
The final stage is weaponization and deployment. The attacker packages the exploit into a delivery mechanism. This could be a malicious email attachment, a compromised website, or a network worm.
Once deployed, the zero day attack begins. The time between discovery and weaponization can vary. It can be months, weeks, or even just days.
Security teams have no visibility into this process until the attack is already underway. This makes early detection critical.
Common Vulnerability Types Exploited in Zero-Day Attacks
While zero-day vulnerabilities can be unique, many fall into well-known categories. Understanding these types helps in designing better defenses. One of the most dangerous is Remote Code Execution (RCE).
An RCE flaw allows an attacker to run arbitrary code on a target machine over a network. This effectively gives them complete control of the system without needing physical access.
Another common type is Privilege Escalation. Here, an attacker first gains a foothold with low-level access. They then exploit a second vulnerability to gain higher privileges, such as administrator or root access.
This allows them to disable security software, create new user accounts, and move laterally across the network. These attacks are often multi-staged and harder to detect.
Other prevalent types include SQL Injection (SQLi) and Cross-Site Scripting (XSS). These target web applications. SQLi allows an attacker to manipulate a backend database.
XSS lets them inject malicious scripts into a website viewed by other users. Buffer overflows, a classic memory corruption bug, are also still common.
They occur when a program writes more data to a buffer than it can hold. This can overwrite adjacent memory and lead to arbitrary code execution.
Actionable Solutions and Frameworks
Defending against a threat you cannot see requires a strategic shift. Traditional security models based on known signatures are insufficient for a zero day attack. Modern defense demands a proactive, multi-layered approach.
It must focus on reducing the attack surface, detecting anomalous behavior, and containing breaches when they occur. This section outlines key frameworks and solutions for CISOs and security leaders.
The foundation of this modern approach is the assumption of breach. Security teams must operate as if an attacker is already inside the network. This mindset changes the focus from building an impenetrable wall to ensuring resilience.
It prioritizes rapid detection, swift response, and damage limitation. It is about making the attacker's job as difficult as possible. This approach minimizes the impact of a successful exploit.
Implementing these frameworks requires a combination of technology, processes, and people. It is not about buying a single "silver bullet" solution. It is about integrating various capabilities into a cohesive security architecture.
From proactive threat hunting to implementing zero trust principles, each layer adds to the overall defensive posture. This comprehensive strategy is the only way to effectively manage the risk of a zero day attack.
Proactive Defense: Vulnerability and Attack Surface Management
You cannot protect what you do not know you have. The first step is to gain complete visibility into your entire attack surface. Attack Surface Management (ASM) platforms help achieve this.
They continuously discover and map all internet-facing assets. This includes servers, cloud instances, IoT devices, and SaaS applications. ASM tools identify potential exposures before attackers do.
Once you have visibility, a robust Vulnerability management program is essential. This goes beyond simple periodic scanning. It involves continuous monitoring and risk-based prioritization.
Not all vulnerabilities are created equal. Your team should focus on fixing the flaws that pose the greatest risk. This requires intelligence on which vulnerabilities are being actively exploited in the wild.
Furthermore, offensive security exercises are invaluable. Regularly scheduled penetration tests can uncover hidden weaknesses. These simulated attacks mimic the techniques used by real-world adversaries.
They can identify complex attack paths that automated scanners might miss. A mature program also includes "red team" exercises. These goal-oriented campaigns test your detection and response capabilities against a simulated zero day attack.
Real-Time Detection and Response Mechanisms
Since prevention of a zero day attack is not always possible, detection is paramount. Modern security tools have moved beyond static signatures. They use behavioral analysis and machine learning to identify suspicious activity.
Endpoint Detection and Response (EDR) solutions monitor activity on laptops and servers. They can detect abnormal processes or network connections that may indicate an exploit.
Network Detection and Response (NDR) tools perform a similar function for network traffic. They analyze data flows in real-time to spot anomalies. For example, an NDR solution might flag a server that suddenly starts communicating with a known malicious domain.
Extended Detection and Response (XDR) platforms combine data from multiple sources. They correlate alerts from endpoints, networks, and cloud environments. This provides a more complete picture of a potential attack.
These technologies enable effective threat detection. They are designed to find the "unknown unknowns." Instead of looking for a specific virus, they look for behaviors that deviate from a normal baseline. This is crucial for identifying a novel zero day attack.
It allows the SOC team to investigate and respond before significant damage occurs. A strong detection capability reduces attacker dwell time.
Architectural Resilience: Zero Trust and Micro-segmentation
A Zero Trust security model is a powerful defense against a zero day attack. Its core principle is "never trust, always verify." It assumes that any user or device could be compromised. Access to resources is granted on a per-session basis.
It requires strict identity verification and device posture checks for every request. This happens regardless of where the request originates from.
If an attacker exploits a zero-day vulnerability on one machine, Zero Trust can contain the breach. The attacker cannot easily move laterally to other systems. Their access is restricted to only what is absolutely necessary for that machine's function.
This containment strategy is critical. It turns a potentially catastrophic network-wide breach into a limited, manageable incident.
Micro-segmentation is a key enabling technology for Zero Trust. It involves dividing the network into small, isolated zones. Security policies are then applied to control traffic between these zones.
For example, a web server should only be able to communicate with its database server. It should not be able to connect to the HR department's file server. This granular control severely limits an attacker's ability to explore the network after an initial compromise.
Strategic Patch and Configuration Management
Even with proactive defenses, patching remains a fundamental security control. When a zero-day vulnerability is publicly disclosed, vendors race to release a patch. Organizations must have a process to deploy these critical patches quickly.
A formal patch management program is not optional. It should include asset inventory, risk assessment, patch testing, and deployment automation.
The goal is to shrink the window of exposure as much as possible. Attackers often reverse-engineer patches to create exploits. They know many organizations are slow to update their systems.
A rapid, efficient patching process can thwart these opportunistic attacks. This is especially true for the period immediately following the disclosure of a new zero day attack.
In situations where a patch cannot be immediately deployed, virtual patching can be a temporary solution. An Intrusion Prevention System (IPS) or a Web Application Firewall (WAF) can be configured to block traffic that attempts to exploit the vulnerability. This provides a shield for the vulnerable system.
It gives the IT team time to test and deploy the official patch without leaving the asset exposed. This risk-based approach is a hallmark of mature security operations.
Real-World Implementation
Theoretical frameworks are useful, but their real-world application is what matters. Examining a major historical zero day attack provides invaluable lessons for security leaders. It moves the discussion from abstract concepts to concrete actions and consequences.
The Log4Shell incident is a perfect case study. It was one of the most widespread and severe vulnerabilities in recent history. Its impact was felt across every industry.
The incident began in late 2021. A security researcher discovered a critical RCE vulnerability in Log4j. Log4j is a popular open-source logging library for Java applications.
The flaw, dubbed "Log4Shell" (CVE-2021-44228), was incredibly easy to exploit. An attacker simply needed to send a malicious text string. If a vulnerable application logged that string, the attacker could take full control of the server.
Because Log4j is used in countless applications, the impact was immediate and global. Everything from cloud services to enterprise software and web servers was at risk. Security teams scrambled to identify their exposure.
They had to determine which of their thousands of applications used the vulnerable library. It was a monumental task. The Log4Shell incident became a stark reminder of the risks hidden within the software supply chain.
Case Study: Deconstructing the Log4Shell Zero-Day Attack
The Log4Shell zero day attack unfolded rapidly. Within hours of the public disclosure, attackers began scanning the internet for vulnerable systems. They quickly automated the exploitation process.
Early attacks involved cryptocurrency miners and botnet recruitment. Soon after, more sophisticated actors, including ransomware gangs and nation-states, began leveraging the exploit for more destructive purposes.
The defensive response was a global effort. Security vendors updated their products to detect and block Log4Shell exploit attempts. The open-source community worked tirelessly to release patched versions of Log4j.
However, the responsibility for remediation fell on individual organizations. Their first challenge was discovery.
Many teams did not have an accurate Software Bill of Materials (SBOM). They did not know where Log4j was running in their environment.
Teams used a variety of methods to hunt for the vulnerability. They used network scanners, EDR queries, and code analysis tools. Once identified, the next step was patching.
This was also complex. Some applications could be updated easily.
Others were legacy systems or third-party products that required a vendor patch. Where patching was not possible, teams implemented workarounds or used virtual patching via WAFs and IPSs.
Lessons for Security Leadership
The Log4Shell crisis offers several critical lessons for CISOs. First, software supply chain security is paramount. You must have a clear inventory of all open-source components in your software.
An SBOM is no longer a "nice to have." It is a fundamental requirement for effective cybersecurity risk management. Without it, you cannot assess your exposure during a crisis.
Second, the incident highlighted the need for a layered defense. Organizations that fared best had multiple controls in place. They had egress filtering on their firewalls, which blocked some outbound connections from compromised servers.
They had EDR tools that detected the post-exploit activity, even if the initial exploit was missed. This reinforces the idea that relying on a single defensive layer is a recipe for failure. Effective cybersecurity is about resilience.
Finally, the incident underscored the value of a well-practiced incident response plan. Teams that had clear communication channels and defined roles were able to respond much faster. A partner can be crucial in these moments.
For instance, a firm like Intervalle Technologies can provide the expertise needed to navigate a complex incident, from initial discovery to final remediation. Their experience helps organizations manage a crisis effectively, which is key to mitigating the impact of a severe zero day attack. Having a dedicated partner, such as Intervalle Technologies, for support during a major security event can be a critical advantage.
Future Outlook and Strategic Recommendations
The threat from a zero day attack will continue to evolve. As technology changes, so do the tactics of threat actors. Security leaders must look ahead to anticipate future challenges.
They need to build security programs that are adaptable and forward-looking. Staying current with emerging trends is essential for maintaining a strong defensive posture. This proactive stance is the difference between leading and lagging in cybersecurity.
One of the most significant trends is the role of artificial intelligence. AI and machine learning will be a double-edged sword. Attackers will use AI to find new vulnerabilities faster.
They may also use it to generate polymorphic malware that evades signature-based detection. This will make the attacker's job easier and more efficient. The speed and scale of AI-driven attacks will test the limits of traditional security operations.
On the other hand, defenders will also leverage AI. AI-powered security tools can analyze vast amounts of data to detect subtle anomalies. They can help automate threat hunting and incident response.
This can free up human analysts to focus on more strategic tasks. The future of cybersecurity will be a race between offensive and defensive AI. Organizations that embrace AI for defense will have a significant advantage.
Emerging Trends in the Zero-Day Ecosystem
The zero-day marketplace is becoming more professionalized. We are seeing the rise of "exploit-as-a-service" models. These platforms make sophisticated attack tools available to a wider audience.
This trend will likely continue, leading to an increase in the volume of zero-day attacks. The economics of the dark web will continue to fuel vulnerability discovery and exploit development.
Another key area of concern is the Internet of Things (IoT) and Operational Technology (OT). These devices are often designed with functionality, not security, in mind. They frequently contain vulnerabilities that are difficult to patch.
As more of these devices are connected to corporate networks, they represent a growing attack surface. A zero day attack against a critical OT system could have devastating physical consequences.
The shift to the cloud also presents new challenges. While cloud providers offer robust security, the shared responsibility model can cause confusion. Misconfigurations of cloud services are a leading cause of breaches.
A zero-day vulnerability in a widely used cloud service or API could have a massive impact. Security teams must adapt their strategies to cover these new, dynamic environments. This requires specialized skills and tools.
Strategic Imperatives for Modern CISOs
In this evolving landscape, CISOs must adopt several strategic imperatives. First, foster a culture of resilience. This means moving beyond a compliance-driven, checklist-based approach to security.
It involves building a program that can withstand and recover from a sophisticated zero day attack. This requires continuous testing, training, and improvement.
Second, invest in visibility and threat intelligence. You cannot defend against threats you are not aware of. This means investing in tools like ASM, EDR, and NDR.
It also means subscribing to high-quality threat intelligence feeds. This information provides early warnings about new vulnerabilities and attacker campaigns. It allows you to be proactive rather than reactive.
Finally, prioritize strategic partnerships. The cybersecurity skills gap is real. Few organizations have all the expertise they need in-house.
Partnering with a Managed Security Service Provider (MSSP) or a Managed Detection and Response (MDR) provider can be a force multiplier. These partners bring specialized skills and 24/7 monitoring capabilities. They can help you mature your security program and improve your ability to defend against the next zero day attack.
Conclusion
The zero day attack represents one of the most significant challenges in modern cybersecurity. It exploits the element of surprise to bypass conventional defenses. The threat is not theoretical; it is a clear and present danger to organizations of all sizes.
The increasing frequency, sophistication, and commercialization of these attacks demand a new approach to security. The old models are no longer sufficient to protect critical assets and data.
For CISOs and other security leaders, the path forward is clear. It requires a fundamental shift from a reactive, prevention-focused posture to a proactive and resilient one. This involves a multi-layered strategy.
It starts with comprehensive visibility and management of the attack surface. It is reinforced by advanced, behavior-based threat detection.
And it is made resilient by architectural principles like Zero Trust and micro-segmentation. This is how you prepare for an unknown threat.
The time for incremental change is over. The cost of a successful zero day attack is too high to ignore. We urge you to re-evaluate your current security strategy in light of these advanced threats.
Assess your capabilities in proactive discovery, real-time detection, and rapid response. Identify the gaps and develop a roadmap to address them. By embracing a modern, resilient security framework, you can significantly reduce your risk and better protect your organization from its most dangerous adversaries.
