The Definitive CISO's Guide to SOC Implementation

A successful SOC implementation is the cornerstone of any modern cybersecurity strategy. For CISOs, IT directors, and compliance officers, it represents the shift from a reactive to a proactive defense posture. This centralized command center unifies people, processes, and technology to defend against an ever-expanding digital threat landscape.
Yet, building a Security Operations Center (SOC) is a complex undertaking, fraught with potential pitfalls that can undermine its effectiveness and waste significant investment.
Many organizations struggle with a clear roadmap for this critical initiative. They often focus too heavily on technology, underestimating the intricate requirements of process engineering and talent acquisition. This article provides a comprehensive blueprint for your SOC implementation.
We will move beyond a basic definition of what a SOC exactly is and dive deep into the technical and strategic layers. You will gain actionable insights into designing a resilient framework, avoiding common failures, and building a center of excellence that delivers measurable security value. This guide is your strategic partner in this crucial endeavor.
The Evolving Threat Landscape: Why SOC Implementation is Critical
The urgency for a robust SOC implementation is driven by a digital environment defined by volatility and aggression. Cyber threats are no longer random, opportunistic attacks. They are sophisticated, multi-stage campaigns executed by well-funded adversaries.
This new reality demands a centralized, intelligence-driven defense mechanism capable of 24/7 vigilance. Without it, organizations remain vulnerable to attacks that can cause catastrophic financial and reputational damage.
The modern attack surface has expanded exponentially. Cloud adoption, remote workforces, and interconnected IoT devices have dissolved the traditional network perimeter. Consequently, security teams face a deluge of data from disparate sources, making it nearly impossible to distinguish real threats from background noise.
A formal SOC implementation is the only viable way to centralize visibility, correlate threat data across the entire IT ecosystem, and enable a coordinated response. The primary goal is strengthening an organization’s threat detection and response capabilities to a level that matches the adversary’s sophistication.
The Escalation of Advanced Persistent Threats (APTs)
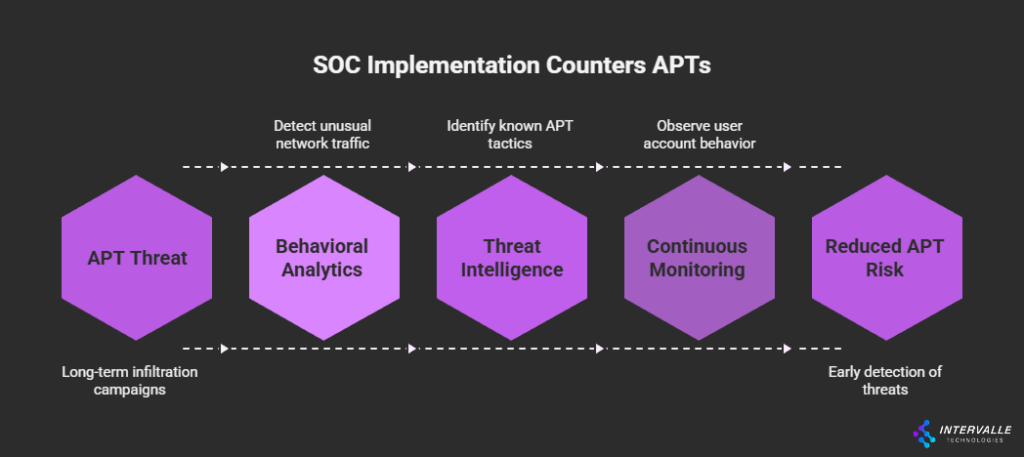
Advanced Persistent Threats (APTs) represent a formidable challenge. These state-sponsored or highly organized criminal groups have the resources and patience to conduct long-term infiltration campaigns. Their methods often involve custom malware, zero-day exploits, and sophisticated social engineering tactics designed to bypass traditional signature-based defenses. An effective SOC implementation is specifically designed to counter these threats.
APTs typically follow a "low and slow" approach. They gain an initial foothold and then move laterally across the network over weeks or months, escalating privileges and exfiltrating data discreetly. A mature SOC uses behavioral analytics, threat intelligence, and continuous monitoring to detect the subtle indicators of compromise (IOCs) associated with APT activity.
This includes unusual network traffic patterns, anomalous user account behavior, or access to sensitive files at odd hours. Without a dedicated SOC, these faint signals are almost always missed until it is too late. The investment in a structured security operations setup is a direct countermeasure to this persistent, high-stakes threat category.
Navigating the Complexities of a Modern SOC Implementation

The complexity of today's IT environments adds another layer of difficulty. A typical enterprise uses dozens of security tools from various vendors. This includes firewalls, endpoint detection and response (EDR), cloud security posture management (CSPM), and identity and access management (IAM) solutions.
While each tool provides value, they often operate in silos, creating visibility gaps and overwhelming security teams with uncontextualized alerts.
A core function of any SOC implementation is to break down these silos. By integrating these disparate data sources into a central Security Information and Event Management (SIEM) platform, analysts can gain a unified view of the security posture. This correlation is what transforms raw data into actionable intelligence.
However, this integration itself is a significant technical challenge. It requires careful planning, robust engineering, and standardized processes to ensure data is properly parsed, normalized, and enriched. A failed SOC implementation often stems from an underestimation of this integration effort, leading to an ineffective and noisy system.
Root Causes of SOC Implementation Failures
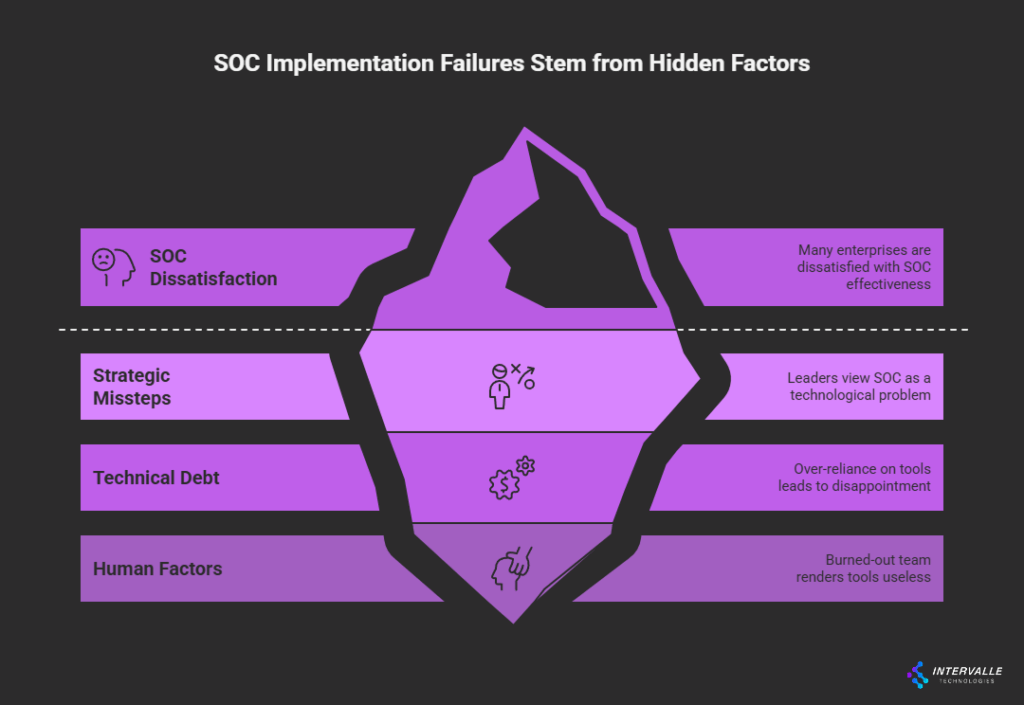
Despite significant investment, many SOCs fail to deliver on their promise. A recent study found that nearly half of all enterprises are dissatisfied with their SOC's effectiveness. These failures are rarely due to a single cause.
Instead, they result from a combination of strategic missteps, technical debt, and human factors. Understanding these common pitfalls is the first step toward a successful SOC implementation.
Many leaders mistakenly view their SOC implementation as a purely technological problem. They believe purchasing a best-in-class SIEM or a sophisticated Security Orchestration, Automation, and Response (SOAR) platform will solve their security challenges. This "tool-first" approach almost always leads to disappointment.
Technology is merely an enabler; the true value of a SOC lies in the synergy between its people, processes, and the technology that supports them. A misaligned strategy or a burned-out team can render the most advanced tools useless.
The Technology Trap: SIEM Misconfiguration and Tool Sprawl
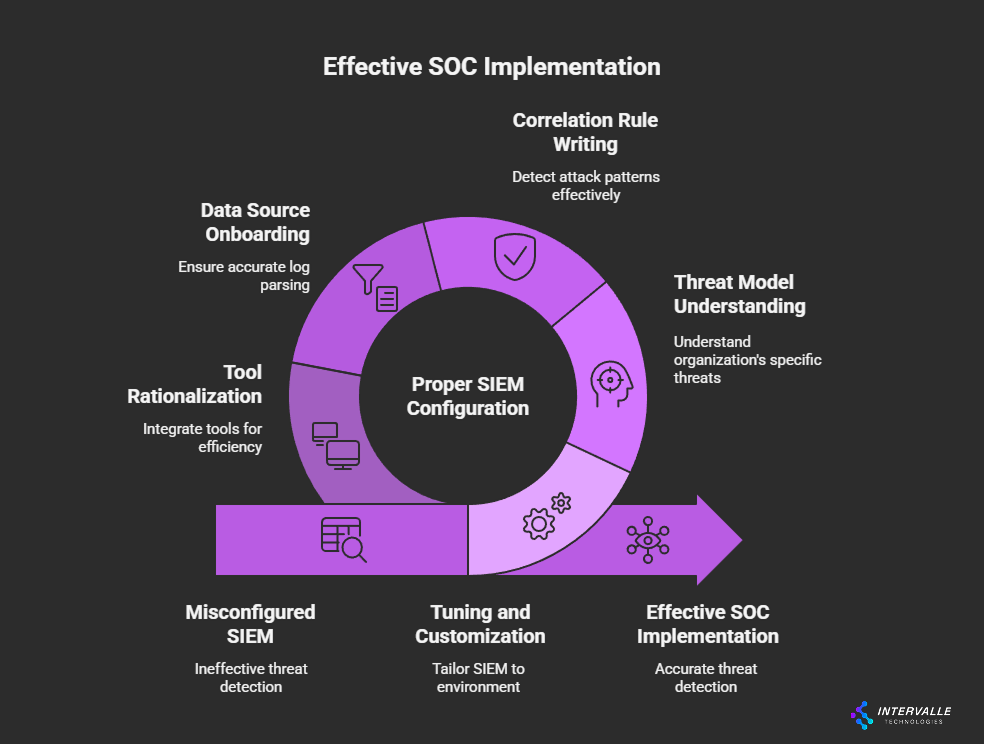
One of the most common technical failures in a SOC implementation is the misconfiguration of the SIEM. A SIEM is the heart of the SOC, but it is not a "plug-and-play" solution. It requires extensive tuning and customization to be effective.
Without proper configuration, the SIEM will either generate a flood of false positives, leading to alert fatigue, or fail to detect real threats, creating a false sense of security.
Effective SIEM deployment requires a deep understanding of the organization's specific threat model and IT environment. Correlation rules must be written to detect attack patterns relevant to the business. Data sources must be onboarded correctly, ensuring logs are parsed accurately.
Furthermore, the problem of tool sprawl exacerbates this issue. When a SOC is burdened with too many unintegrated tools, analysts waste precious time pivoting between different consoles instead of investigating threats. A successful SOC implementation plan must include a strategy for tool rationalization and deep integration, ensuring every component of the tech stack serves a clear purpose and communicates effectively.
The Human Element in Your Security Operations Setup
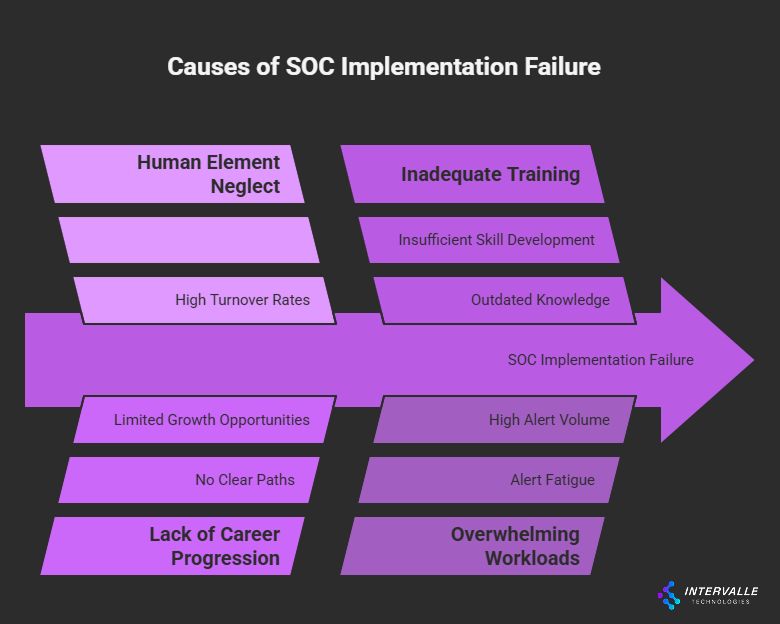
The second major cause of failure is neglecting the human element. Running a 24/7 SOC is a high-stress, demanding job that can quickly lead to analyst burnout. Many organizations struggle with high turnover rates, losing valuable institutional knowledge and technical expertise.
This is often caused by a lack of clear career progression, inadequate training, and overwhelming workloads due to the aforementioned alert fatigue.
Building a resilient team is a critical pillar of your security operations setup. This involves more than just hiring skilled individuals. It requires creating a culture of continuous learning and providing the right tools and processes to empower analysts, not overwhelm them.
A successful SOC implementation must include a detailed staffing plan with well-defined roles and responsibilities, a structured training program, and clear key performance indicators (KPIs) that focus on meaningful outcomes, not just the volume of alerts closed. Neglecting the well-being and professional development of your SOC team is a direct path to failure.
A Strategic Blueprint for Your SOC Implementation
A successful SOC implementation is not an accident. It is the result of meticulous planning and a phased, strategic approach. This blueprint breaks the process down into three core phases: Strategy and Design, Technology Stack Construction, and Team Assembly.
Following this structured methodology ensures that your SOC is built on a solid foundation, aligned with business objectives, and equipped to evolve with the threat landscape. This is one of the key best practices for SOC implementation.
Before a single piece of technology is purchased, a clear vision and mission for the SOC must be established. This initial phase is the most critical for long-term success. It involves engaging with business stakeholders to understand key risks, defining the scope of the SOC's responsibilities, and establishing the metrics that will be used to measure its effectiveness.
This strategic alignment ensures the SOC is not viewed as a cost center but as a vital business enabler. When you are implementing a SOC, this foundational work prevents costly course corrections later in the project.
Phase 1: Strategy and Design for Your SOC Implementation
This foundational phase sets the direction for the entire SOC implementation project. It's where you define what the SOC will protect and how you will measure success. Rushing this stage often leads to a SOC that is misaligned with the organization's actual risk profile.
Defining Scope, Mission, and Key Metrics
The first step is to create a formal SOC charter. This document should articulate the SOC's mission, its scope of authority, and the specific assets it is responsible for protecting. Will the SOC monitor only on-premises infrastructure, or will it also cover cloud environments, SaaS applications, and operational technology (OT)?
Answering these questions is fundamental.
Next, define your key performance indicators (KPIs) and key risk indicators (KRIs). Instead of vanity metrics like "alerts processed," focus on metrics that demonstrate tangible value. Essential SOC metrics include:
- Mean Time to Detect (MTTD): How long does it take to identify a potential security incident?
- Mean Time to Respond (MTTR): How long does it take to contain and neutralize a confirmed threat?
- Dwell Time: The duration an attacker remains undetected within the network.
- Incident Response Success Rate: The percentage of incidents resolved without significant business impact.
These metrics provide a clear, data-driven way to measure the SOC's performance and justify its ongoing investment to the board.
Choosing a SOC Model: In-House, Hybrid, or MSSP
With a clear charter, you must decide on an operational model for your SOC implementation. Each model has distinct advantages and disadvantages related to cost, control, and expertise.
- In-House SOC: Offers maximum control and deep integration with the business. However, it is the most expensive and complex model to build and maintain, requiring significant upfront investment in technology and a continuous effort to recruit and retain talent.
- Managed Security Service Provider (MSSP): An outsourced model where a third party provides 24/7 monitoring and response. This is often the most cost-effective option, providing access to a large team of experts and advanced technology without the capital expenditure. The primary drawback is a potential lack of contextual understanding of your specific business environment.
- Hybrid SOC: A blended model that combines an in-house team with services from an MSSP or a Managed Detection and Response (MDR) provider. The in-house team (often Tier 2/3 analysts) handles high-level investigation and threat hunting, while the MSSP manages 24/7 alert monitoring and initial triage. This model often provides the best balance of control, cost, and expertise for most mid-to-large enterprises.
The choice of model will fundamentally shape your SOC implementation process and budget.

Phase 2: Building Your Cyber Defense Center Technology Stack
Once the strategy is set, you can begin designing the technology stack. The goal is to create an integrated ecosystem where data flows seamlessly, and automation handles repetitive tasks, freeing up analysts for high-value work. Avoid the temptation to buy the "best" tool in every category; instead, focus on tools that integrate well and support your defined processes.
SIEM and SOAR: The Core of Your Operations
The SIEM remains the central nervous system of the SOC. It aggregates log data from across the enterprise, normalizes it, and uses correlation rules to detect suspicious activity. When selecting a SIEM, consider its scalability, its ability to ingest data from all your required sources (including cloud and SaaS), and the quality of its built-in detection logic.
Modern, next-gen SIEMs often include User and Entity Behavior Analytics (UEBA) capabilities to detect insider threats and compromised accounts.
A SOAR platform is the perfect complement to a SIEM. It automates and orchestrates incident response workflows. When the SIEM generates a high-fidelity alert, the SOAR platform can automatically execute a pre-defined playbook.
For example, it could enrich the alert with threat intelligence, quarantine an affected endpoint via an EDR agent, and open a ticket in the IT service management system—all before a human analyst even sees it. This dramatically reduces MTTR and allows the SOC to scale its operations effectively.
Integrating Threat Intelligence and EDR/XDR
A SOC cannot operate in a vacuum. It needs external context to understand the threats it faces. A Threat Intelligence Platform (TIP) provides this context by ingesting feeds of IOCs, threat actor tactics, techniques, and procedures (TTPs), and vulnerability data.
This intelligence is used to enrich alerts, prioritize incidents, and power proactive threat hunting. Integrating the TIP with your SIEM and SOAR is essential for a successful SOC implementation.
Endpoint Detection and Response (EDR) and its evolution, Extended Detection and Response (XDR), are also critical components. EDR provides deep visibility into activity on endpoints (laptops, servers) and allows analysts to remotely investigate and contain threats. XDR extends this capability across other security layers, such as email, network, and cloud, providing a more holistic view of an attack chain.
The data from EDR/XDR is a vital log source for the SIEM, and the response capabilities are a key integration point for the SOAR.
Phase 3: Assembling Your Elite SOC Team
Technology and processes are inanimate without a skilled team to operate them. This phase of your SOC implementation focuses on building the human capability of your cyber defense center. This is often the most challenging aspect, given the global cybersecurity skills shortage.
Defining Roles, Responsibilities, and Skill Sets
A mature SOC typically uses a tiered analyst model. This structure provides a clear path for incident escalation and career progression.
- Tier 1 Analyst (Triage Specialist): The first line of defense. They monitor the alert queue, perform initial investigation to weed out false positives, and escalate legitimate incidents to Tier 2.
- Tier 2 Analyst (Incident Responder): Conducts deep-dive investigations into escalated incidents. They perform forensics, analyze malware, and determine the full scope of a compromise.
- Tier 3 Analyst (Threat Hunter / SME): The most senior technical experts. They proactively hunt for threats that have bypassed automated defenses, develop new detection rules, and serve as subject matter experts (SMEs) on complex threats.
Beyond analysts, a SOC also needs SOC Engineers to maintain the technology stack and SOC Managers to oversee operations and report to leadership. The skills and expertise of these SOC professionals are the lifeblood of an effective security program.
Training, Drills, and Continuous Improvement
A SOC is a living entity that must constantly adapt. A continuous training program is essential to keep the team's skills sharp and up-to-date with the latest TTPs. This should include both formal certifications and hands-on training using cyber ranges or tabletop exercises.
Regularly conducting incident response drills is also crucial. These exercises simulate real-world attack scenarios, allowing the team to practice their playbooks and identify gaps in their processes or technology. Metrics from these drills, such as MTTD and MTTR, should be tracked over time to demonstrate improvement.
This commitment to continuous learning and practice is a hallmark of a successful SOC implementation.
Real-World SOC Implementation: A Case Study
To illustrate these principles in action, let's consider a real-world scenario. A mid-sized financial services firm was facing increasing pressure from regulators and a rising tide of sophisticated phishing and ransomware attacks. Their existing security was a patchwork of disconnected tools managed by a small, overworked IT team.
They knew they needed a formal SOC implementation but were unsure where to start.
The firm's primary challenges were a lack of centralized visibility, no formal incident response process, and an inability to provide auditors with clear evidence of their security posture. Alerts from their various tools were often ignored due to a lack of context and overwhelming volume. Dwell time for threats was estimated to be over 100 days, leaving them exposed to significant risk.
The Challenge: A Financial Services Firm's Patchwork Security
The firm's initial state was reactive. Security was an afterthought, with the IT team only responding after a security event caused a noticeable disruption. Their technology stack consisted of a traditional firewall, a legacy antivirus solution, and a basic log collector that was rarely used for proactive analysis.
They had no EDR, no threat intelligence, and no defined process for handling a security incident.
This lack of a structured security operations setup made it impossible to meet compliance requirements for regulations like PCI DSS and NYDFS. Auditors repeatedly flagged the absence of continuous monitoring and incident response capabilities. The board recognized that this situation was untenable and approved the budget for a comprehensive SOC implementation project.
The Solution: A Phased SOC Implementation Journey
The firm wisely opted for a phased, hybrid approach to their SOC implementation. They partnered with a trusted cybersecurity provider, Intervalle Technologies, to guide them through the process and provide co-managed services.
Phase 1 (Strategy): The first six months were dedicated to strategy and design. They worked with stakeholders to define a SOC charter focused on protecting customer financial data and ensuring regulatory compliance. They established clear MTTD and MTTR targets and decided on a hybrid model.
An in-house team would be built to handle incident response and business context, while a 24/7 MDR service would provide initial alert triage and monitoring.
Phase 2 (Technology): The firm deployed a modern, cloud-native SIEM and an XDR platform. The XDR agent was rolled out to all endpoints and servers, providing instant visibility and response capabilities. Log sources from their cloud environment (Azure) and critical applications were integrated into the SIEM.
A SOAR solution was implemented to automate the initial response to common threats like phishing emails and malware infections.
Phase 3 (People & Process): The firm hired a SOC Manager and two Tier 2 analysts. They worked with their MDR partner to develop a clear set of incident response playbooks and escalation procedures. The in-house team received extensive training on the new tools and participated in weekly threat briefing calls with the MDR provider.
Within 12 months, the results were transformative. The firm reduced their average MTTD from over 100 days to under 24 hours. Their MTTR for critical incidents dropped from days to just a few hours.
They successfully passed their next audit, providing clear, data-driven evidence of their security controls. This successful SOC implementation turned their security program from a liability into a business enabler.
The Future of Security Operations: Beyond Traditional SOC Implementation
The field of cybersecurity is in constant flux, and the SOC must evolve with it. The traditional, alert-driven model of security operations is becoming unsustainable in the face of AI-powered attacks and an ever-expanding attack surface. The future of a successful SOC implementation lies in greater automation, proactive defense, and a deeper integration with the business.
Security leaders must look beyond the day-to-day firefighting and consider the strategic evolution of their security operations. This means embracing new technologies and methodologies that can augment human capabilities and shift the SOC's focus from reactive incident response to proactive risk reduction. The next generation of SOCs will be defined by their ability to anticipate threats, not just react to them.
This forward-looking perspective is vital for any long-term SOC implementation plan.
AI and Automation in Modern SOCs
Artificial intelligence and machine learning are no longer just buzzwords; they are becoming essential components of a modern SOC. AI can analyze massive datasets far more quickly and accurately than human analysts, identifying subtle patterns and anomalies that might indicate a sophisticated attack. In a modern SOC implementation, AI-driven UEBA can automatically detect compromised credentials or insider threats without relying on pre-defined rules.
Automation, powered by SOAR platforms, will continue to expand. In the future, automation will handle not just initial triage but also complex investigation and remediation tasks. This will free up senior analysts to focus almost exclusively on high-value activities like proactive threat hunting, reverse-engineering malware, and developing novel detection strategies.
The goal is to create an "autonomous SOC" where machines handle the repetitive work, allowing humans to focus on strategic defense.
The Shift Towards Proactive Threat Hunting
Reactive, alert-based monitoring will always be necessary, but it is no longer sufficient. The most mature SOCs are shifting their focus towards proactive threat hunting. This is a hypothesis-driven process where skilled analysts actively search for hidden adversaries within the network, assuming a breach has already occurred.
Threat hunters use their knowledge of attacker TTPs and their deep understanding of the organization's environment to look for signs of compromise that automated systems may have missed.
A successful SOC implementation must build threat hunting into its operational rhythm. This requires providing analysts with the right tools (like EDR/XDR platforms with rich query capabilities) and, more importantly, the time to hunt. Dedicating a percentage of the senior team's time specifically to this activity can dramatically reduce threat dwell time and uncover hidden risks before they escalate into major incidents.
Conclusion: Finalizing Your SOC Implementation Strategy
A successful SOC implementation is a transformative initiative that elevates an organization's entire security posture. It is a complex journey that demands a holistic approach, balancing the critical pillars of people, process, and technology. By moving beyond a simple tool-centric view, CISOs and security leaders can build a resilient, intelligence-driven cyber defense center that provides measurable business value.
The journey from a reactive to a proactive defense is not easy, but it is essential for survival in today's threat landscape.
This guide has provided a strategic blueprint, from initial design and technology selection to building an elite team and looking toward the future. The key takeaway is that a SOC implementation must be a deliberate, phased process, grounded in the specific risks and objectives of your business. It is not a one-time project but a continuous cycle of improvement, adaptation, and learning.
By avoiding common pitfalls like tool sprawl and analyst burnout, and by focusing on strategic metrics like MTTD and MTTR, you can ensure your investment yields a powerful return in the form of enhanced cyber resilience.
Your journey to a state-of-the-art security operations setup begins with a clear plan. If you are ready to fortify your defenses and require expert guidance in your SOC implementation, the team at Intervalle Technologies is here to help you navigate every step of the process. Begin building your resilient cyber defense today.
