PCI Policy: Complete Guide to PCI DSS Compliance and Security Standards
Understanding and implementing a comprehensive PCI policy has become essential for organizations handling payment card data. Whether you're a small business processing occasional transactions or a large enterprise managing thousands of daily payments, establishing robust PCI DSS policies and procedures ensures regulatory compliance. Moreover, these frameworks provide essential customer data protection.
What is a PCI Policy and Why It Matters
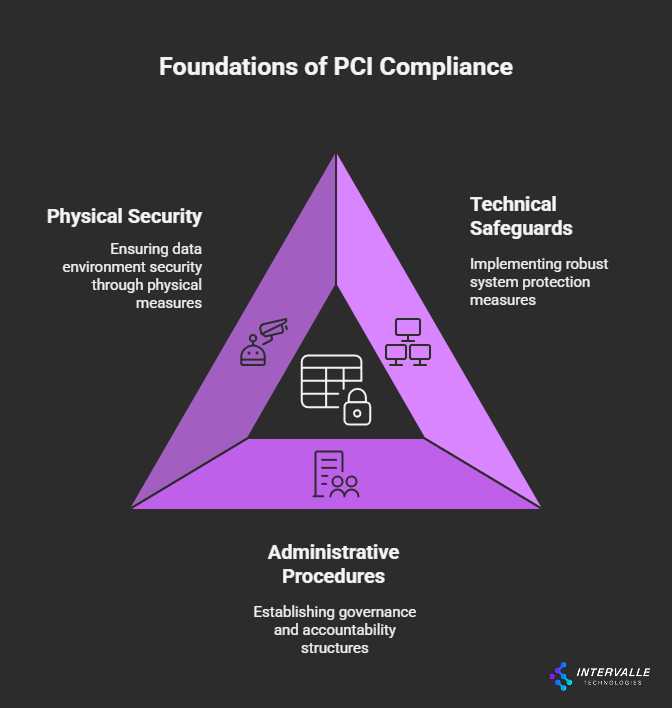
A PCI compliance policy serves as your organization's blueprint for protecting cardholder data. Specifically, this framework covers every stage of payment processing. Furthermore, this comprehensive approach encompasses:
• Technical safeguards for system protection
• Administrative procedures for governance
• Physical security measures for data environments
Consequently, organizations can meet Payment Card Industry Data Security Standard requirements while maintaining operational efficiency.
Modern payment processing environments face increasingly sophisticated cyber threats. Therefore, traditional security measures have become insufficient. However, organizations implementing effective PCI DSS policy frameworks typically experience 60% fewer security incidents. In contrast, those relying on basic compliance measures alone face higher risks. Additionally, comprehensive policy implementation reduces the average cost of a data breach significantly. According to recent industry studies, costs drop from $4.45 million to approximately $3.05 million.
The foundation of any successful PCI information security policy rests on understanding that compliance extends beyond mere technical controls. Instead, effective policies integrate seamlessly with existing business processes. Furthermore, they establish clear accountability structures. As a result, organizations achieve consistent enforcement across all levels.
Evolution of PCI DSS Password Requirements
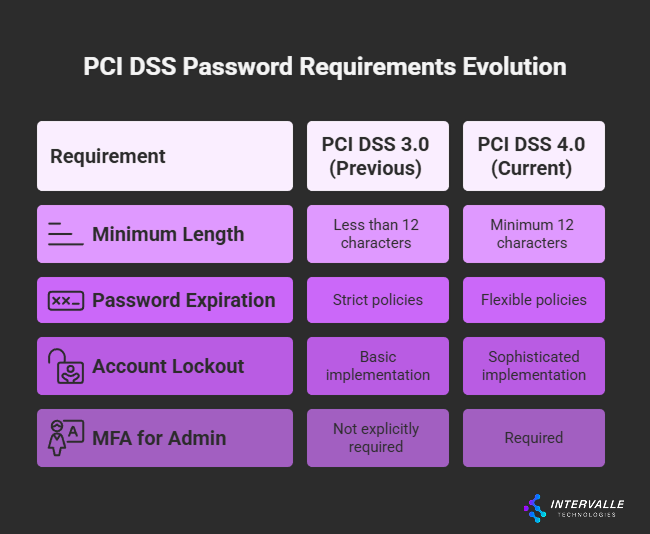
The latest PCI DSS password requirements represent a significant advancement in authentication security standards. Unlike previous versions that emphasized complexity over length, PCI DSS 4.0 now mandates minimum 12-character passwords. Therefore, this change reflects modern understanding of cryptographic strength. Additionally, it addresses user behavior patterns.
These enhanced PCI password requirements address several critical security vulnerabilities:
• Target weaknesses identified in earlier standards
• Require multi-factor authentication for administrative access
• Apply to all cardholder data environments
• Allow flexible password expiration policies
Meanwhile, password expiration policies have become more flexible. As a result, they can accommodate risk-based authentication systems.
Contemporary PCI compliance password requirements recognize that forcing frequent password changes often leads to weaker credentials. Instead, the updated standards emphasize continuous monitoring and risk assessment. Therefore, organizations can determine appropriate password lifecycle management strategies.
Account lockout mechanisms now require more sophisticated implementation. Specifically, systems must automatically lock accounts after ten consecutive failed attempts. Additionally, they must maintain 30-minute minimum lockout periods. This approach balances security needs with operational requirements. Furthermore, it prevents both brute force attacks and excessive user frustration.
Developing Comprehensive PCI DSS Policies and Procedures
Creating effective PCI DSS policies and procedures requires systematic analysis of your organization's specific payment processing environment. Rather than adopting generic templates, successful implementations begin with thorough assessment. Specifically, this includes evaluating:
• Existing systems and infrastructure
• Data flows throughout the organization
• Current business processes
• Security gaps and vulnerabilities
The policy development process should engage stakeholders across multiple departments. For instance, this includes IT security, legal compliance, operations, and executive leadership. This collaborative approach ensures that resulting policies remain both technically sound and practically implementable. Furthermore, it considers your organization's unique operational context.
Documentation standards for PCI policies and procedures must address twelve primary requirement areas. Additionally, they must maintain clarity and accessibility for end users. Each policy section should include:
• Clear purpose statements
• Defined scope boundaries
• Specific implementation procedures
• Measurable compliance indicators
Regular policy review cycles ensure that your PCI DSS security policy framework remains current. Specifically, it stays aligned with evolving threat landscapes and regulatory updates. Organizations typically implement quarterly review processes for high-risk areas. Meanwhile, they conduct comprehensive annual assessments of the entire policy suite.
Essential Components of PCI Information Security Policy
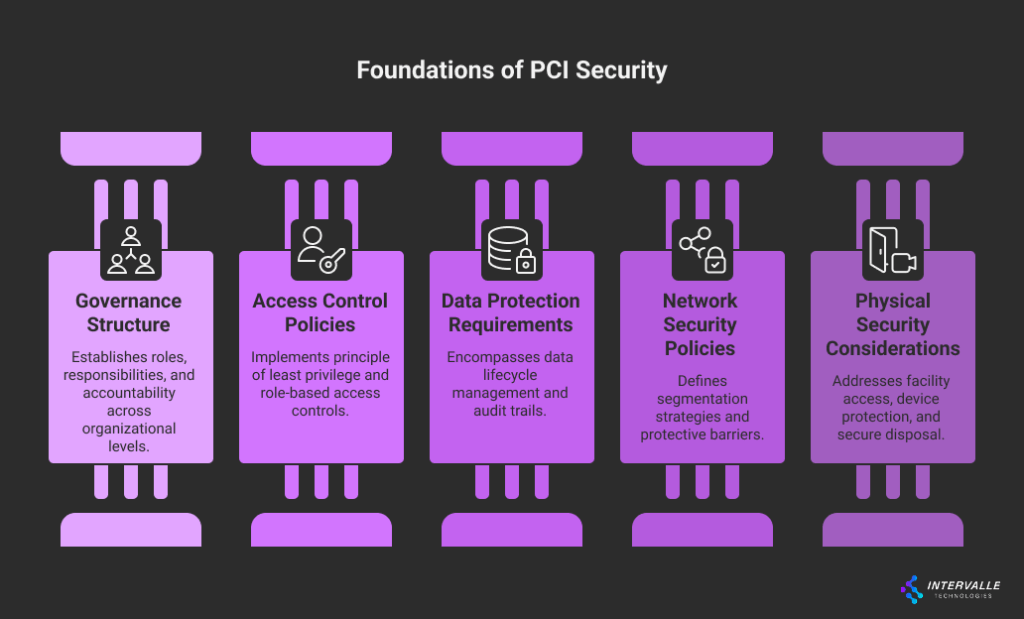
Your PCI information security policy must establish clear governance structures. These define roles, responsibilities, and accountability measures across all organizational levels. Executive leadership commitment remains crucial for successful implementation. This is because policy effectiveness depends heavily on:
• Consistent enforcement throughout the organization
• Adequate resource allocation for implementation
• Regular monitoring and assessment activities
• Ongoing training and awareness programs
Access control policies represent perhaps the most critical component of any comprehensive PCI compliance security policy. These policies must implement principle of least privilege. Simultaneously, they maintain operational efficiency through role-based access controls. Furthermore, they include regular access certification processes.
Data protection requirements extend beyond basic encryption. Instead, they encompass entire data lifecycle management. Your policies should address:
• Data collection procedures and standards • Processing requirements and controls • Storage security measures and encryption • Transmission protocols and safeguards • Secure disposal methods and verification
Additionally, they must maintain clear audit trails for all cardholder data interactions.
Network security policies must define segmentation strategies. These isolate cardholder data environments from general corporate networks. This includes:
• Firewall configuration standards and rules
• Intrusion detection system requirements
• Regular vulnerability assessment procedures
• Network monitoring and logging protocols
Moreover, these measures maintain protective barriers around sensitive data.
Physical security considerations often receive insufficient attention in PCI DSS information security policy development. Nevertheless, they represent significant risk vectors. Comprehensive policies address:
• Facility access controls and monitoring
• Device protection measures and inventory
• Secure disposal procedures for electronic data
• Paper-based cardholder data destruction
Advanced Implementation Strategies for PCI Compliance
Successful PCI policy implementation requires phased approaches that prioritize high-risk areas. Meanwhile, they maintain business continuity throughout the deployment process. Organizations typically begin with critical infrastructure components. Subsequently, they expand to less sensitive systems and processes.
Technology integration plays a vital role in effective policy enforcement. Specifically, automated monitoring systems provide real-time compliance validation and exception reporting. Modern implementations leverage security information and event management platforms. Consequently, they correlate policy violations with potential security incidents.
Training and awareness programs ensure that policy requirements translate into consistent daily practices. Rather than generic security awareness sessions, effective programs provide role-specific training. Therefore, they address individual responsibilities within the broader PCI DSS policies and procedures framework.
Key training components include:
• Role-specific security requirements
• Incident response procedures
• Data handling best practices
• Regular refresher sessions and updates
Continuous improvement processes enable organizations to adapt their PCI compliance policy frameworks. Specifically, they base adaptations on operational experience, threat intelligence, and regulatory evolution. Regular assessment cycles identify opportunities for streamlining procedures. Meanwhile, they maintain or enhance security effectiveness.
Managing PCI DSS Password Requirements in Practice
Implementing PCI DSS password requirements within complex organizational environments requires careful balance. Specifically, organizations must balance security objectives and user productivity. They must consider:
• Technical infrastructure capabilities and limitations
• User behavior patterns and preferences
• Operational workflow requirements
• Integration with existing systems
Password management solutions can significantly simplify compliance with enhanced PCI password requirements. Simultaneously, they improve user experience through single sign-on capabilities and automated credential rotation. These systems often include policy enforcement engines. Therefore, they prevent common password selection errors.
Multi-factor authentication deployment represents one of the most impactful security improvements organizations can implement. Modern solutions offer various authentication factors:
• Biometric options (fingerprint, facial recognition)
• Hardware tokens and smart cards
• Mobile device integration and push notifications
• Software-based authenticators
Regular password policy assessment ensures that authentication requirements remain aligned with evolving threat landscapes. Meanwhile, they support business objectives. Organizations should monitor authentication failure patterns, user compliance rates, and security incident correlation. Consequently, they can optimize policy effectiveness.
Risk Assessment and Compliance Monitoring
Effective PCI policy frameworks incorporate comprehensive risk assessment methodologies. These identify vulnerabilities across technical, administrative, and physical security domains. These assessments should evaluate not only current compliance status. Additionally, they should assess emerging threats that could impact future security posture.
Risk assessment components include:
• Vulnerability scanning and penetration testing • Business impact analysis and threat modeling
• Gap analysis against PCI DSS requirements • Third-party risk evaluation and management
Compliance monitoring systems provide continuous visibility into policy adherence. Meanwhile, they generate evidence required for annual assessments and audits. Automated monitoring reduces administrative overhead. Furthermore, it ensures consistent evaluation across all policy areas.
Exception handling procedures define how organizations manage temporary deviations from established PCI DSS policies and procedures. These procedures should include:
• Approval workflows and authorization levels
• Compensating control requirements and implementation
• Remediation timelines and accountability measures
• Risk assessment and mitigation strategies
Moreover, they maintain security effectiveness during operational disruptions.
Regular compliance reporting enables executive leadership to maintain oversight of organizational security posture. Additionally, it identifies areas requiring additional investment or attention. Effective reporting balances detailed technical information with strategic business implications.
Common Implementation Challenges and Solutions
Resource constraints represent the most frequently cited obstacle to effective PCI compliance policy implementation. However, organizations can address these challenges through:
• Phased deployment strategies that spread costs over time
• Automation investments that reduce ongoing operational burden
• Strategic partnerships with specialized service providers
• Risk-based prioritization of critical security controls
Technical complexity within legacy environments often complicates policy implementation. This is particularly true for organizations with diverse technology infrastructures. Network segmentation strategies can reduce compliance scope. Meanwhile, they enable gradual modernization of critical systems.
User resistance to new security requirements typically emerges during initial policy deployment phases. Comprehensive change management programs can minimize these challenges. Specifically, they should:
• Emphasize business benefits and risk reduction
• Provide adequate training and support resources
• Involve users in policy development processes
• Establish feedback mechanisms for continuous improvement
Ongoing maintenance requirements for PCI DSS security policy frameworks demand sustained organizational commitment. This extends beyond initial implementation phases. Organizations should establish dedicated governance structures. Additionally, they should allocate appropriate resources for long-term policy management.
Building Effective Governance Structures
Governance frameworks for PCI information security policy implementation require clear definition. Specifically, they must define roles, responsibilities, and decision-making authority across all organizational levels. Executive sponsorship remains essential for securing necessary resources. Furthermore, it ensures consistent policy enforcement.
Policy committees should include representatives from multiple departments:
• Security and risk management teams
• Legal and compliance professionals
• Operations and business unit leaders
• IT infrastructure and application teams
Regular committee meetings enable ongoing assessment of policy effectiveness. Additionally, they identify improvement opportunities.
Communication strategies must ensure that policy requirements reach all relevant stakeholders. Meanwhile, they provide mechanisms for feedback and clarification. Effective communication programs utilize multiple channels:
• Written policies and procedure documents
• Training sessions and workshops
• Email updates and newsletters
• Intranet portals and knowledge bases
Furthermore, they accommodate diverse learning preferences and operational contexts.
Performance measurement systems enable organizations to evaluate PCI compliance security policy effectiveness. They do this through quantitative metrics and qualitative assessments. Regular measurement activities should inform continuous improvement initiatives. Additionally, they should guide resource allocation decisions.
Future-Proofing Your PCI Policy Framework
Emerging technologies continue to reshape payment processing environments. Therefore, PCI DSS policies and procedures must adapt to evolving operational requirements. Cloud computing, mobile payments, and artificial intelligence applications present both opportunities and challenges. Consequently, they require updates to traditional compliance approaches.
Technology considerations include:
• Cloud service provider security assessments
• Mobile payment application controls
• API security and authentication protocols
• Artificial intelligence and machine learning implementations
Threat landscape evolution demands proactive policy updates. These address emerging attack vectors and vulnerability patterns. Organizations should maintain awareness of industry threat intelligence. Meanwhile, they should conduct regular security assessments that identify potential policy gaps.
Regulatory changes within the payment card industry may require significant policy adjustments. This is because standards continue evolving. Maintaining relationships with industry associations and compliance consultants can provide early warning. Therefore, they alert organizations to upcoming changes that may impact their PCI policy framework.
Technology refresh cycles present opportunities to enhance policy effectiveness. Specifically, they enable implementation of more advanced security controls and monitoring capabilities. Organizations should align policy updates with planned infrastructure improvements. Consequently, they can maximize return on security investments.
Conclusion: Building Sustainable PCI Compliance
Developing and maintaining effective PCI policies and procedures requires sustained organizational commitment. This extends far beyond initial compliance achievement. Organizations that view PCI compliance as an ongoing strategic initiative typically achieve superior security outcomes. Meanwhile, they minimize long-term costs.
The investment in comprehensive PCI DSS information security policy frameworks delivers measurable returns:
• Reduced security incident frequency and severity
• Lower long-term compliance and audit costs
• Enhanced customer trust and brand reputation
• Improved overall security posture and risk management
Furthermore, organizations with mature policy frameworks often find that PCI compliance efforts strengthen their broader security capabilities.
Success in PCI compliance ultimately depends on treating policy development as an integral component of business operations. Rather than viewing it as an isolated compliance exercise, successful organizations integrate PCI compliance password requirements and broader policy mandates into daily workflows. Consequently, they create sustainable competitive advantages through demonstrated commitment to data protection and customer security.
By following the comprehensive guidance outlined in this resource, organizations can build robust PCI policy frameworks. These protect sensitive payment card data while supporting business objectives and operational efficiency. The key lies in viewing compliance not as a burden but as an opportunity. Therefore, organizations can enhance their security capabilities and customer trust through systematic implementation of proven best practices.
